- 30 Best Free Hacking Apps & Tools For Android
- Android Hacking
- Introduction to Android Hacking
- Secure Coding Handbook
- Android Hacking Resources
- Android Hacking Tools / Android Hacking Apps
- How to Secure Your Android Device From Attackers
- The Three Biggest Threats to Android Devices
- Threat One: Data in Transit
- Threat Two: Untrustworthy App Stores
- Threat Three: SMS Trojans
- Three Ways to Protect Your Android Devices
- Use TLS Encryption
- Test Third-Party App Security
- Use Caution When Using SMS Payments
- Veracode for Application Security
30 Best Free Hacking Apps & Tools For Android
In this article, we will list the Top 30 Android Hacking Tools to help with networking & pentesting tasks.
30 Best Free Hacking Apps & Tools For Android
NMap for Android (NetworkMapper)
Network Mapper is an unofficial Android frontend for well known Nmap scanner. The frontend will help you to download and install Nmap as well as use it.
Nmap will help you to discover hosts, protocols, open ports, services and its configuration and vulnerabilities on networks.
FaceNiff
Image Credits: Faceniff
FaceNiff is an Android app that allows you to sniff and intercept web session profiles over the WiFi that your mobile is connected to. (Root is required)
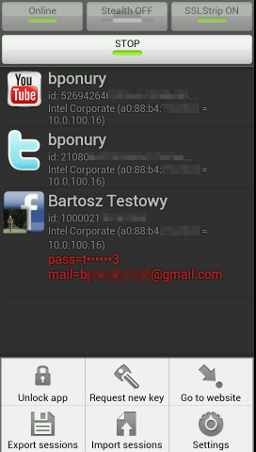
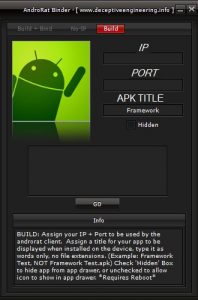
AndroRAT
AndroidRAT is an Android Remote Administration Tool for Android devices.
AnDOSid
AnDOSid is an android tool developed by Scott Herbert that you can use to launch DoS attacks from your mobile phone.
SSHDroid – Android Secure Shell
SSHDroid application will let you connect to your device from a PC and execute commands (like “terminal” and “adb shell”) or edit files (through SFTP, WinSCP, Cyberduck, etc.
Hackode
Hackode : The hacker’s Toolbox is an application for penetration tester, Ethical hackers, IT administrator, and Cybersecurity professionals to perform different tasks like reconnaissance, scanning performing exploits etc.
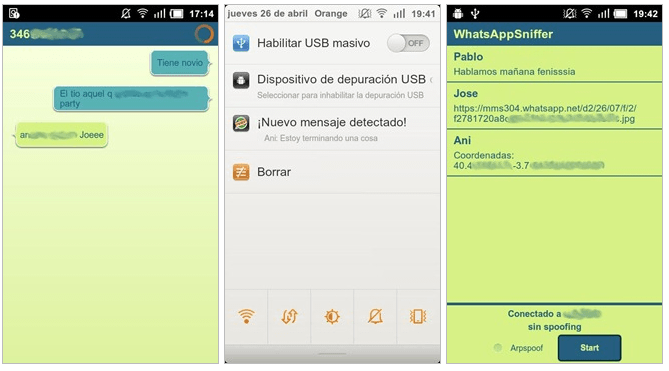
WhatsApp Sniffer
WhatsApp Sniffer Android app allows Android users to receive the text messages from WhatsApp application from phones that uses the same WiFi
Evil Operator
Using Evil Operator you can connect two friends into a phone conversation making them think they called each other!. Then you can record the call and share the recording with friends via social media and cloud services. Limitations: Only allows one free call a day! Evil Operator allows you to share tokens can with the PrankDial app.
Download Evil Operator
APK Inspector
APKinspector is a powerful GUI tool for analysts to analyze Android applications.
Download APK inspector
Kill Wi-Fi
Kill Wi-Fi app will make other devices in the same network think that your device is a router. So they will try to connect to the internet through you. WifiKill then drops the connections of these other devices.
Droidsheep
DroidSheep is an android Mitm tool developed by Andreas Koch for security analysis in wireless networks. It is a session hijacking tool that allows hackers to capture session cookies over the wireless network.
Download Droidsheep
dSploit
dSploit is a penetration testing suite developed for the Android operating.as of 2014 DSploit was merged with zANTI.
Zanti
zANTI™ is a mobile penetration testing toolkit that lets security managers assess the risk level of a network with the push of a button. This easy to use mobile toolkit enables IT Security Administrators to simulate an advanced attacker to identify the malicious techniques they use in the wild to compromise the corporate network.
Shark for root
Shark For Root is an android version of Wireshark it was designed for security experts and hackers. It is basically is a traffic sniffer that works on WiFi, 3G and tethered mode. The app is based on tcpdump and will work with tcpdump command-line options. Enjoy this excellent Android application.
Zip Signer
ZipSigner app allows you to sign update.zip files, APK, or JAR files using your own private keys or one of the four built-in certificates (media, platform, shared, testkey) All from your Android device. All output is automatically zip-aligned ZipSigner can work with existing keystores, or you can create keystores, keys, and self-signed certificates.
Wi-Fi Finder
Don’t worry about finding a Wi-Fi internet connection free or paid public Wi-Fi hotspots online or offline Wi-Fi Finder gives a detailed map of various Wi-Fi hotspots around you can come in really useful when hunting for Open Wireless Networks.
SSLStrip for Android
SSLStrip for Android is a port from the popular SSLStrip a Python tool created by Moxie Marlinspike. SSLStrip transparently hijacks HTTP traffic on a network essentially SSLStrip allows HTTPS traffic to be forced to use HTTP SSL stripping attacks can come in really handy when performing MITM attacks.
USBCleaver
The goal of the USB Cleaver is to silently recover information from a target Windows 2000 or higher computer, including password hashes, LSA secrets, IP information, etc… beauty lies in the fact that the payload can run silently and without modifying the system or sending network traffic, making it near invisible. It captures all the information to a LOG file stored in your sd card and can be reviewed at any time.
DroidSQLi
DroidSQLi is an android app that allows you to launch SQL injection attacks on a target URL. Best of all its all automated on any Android device.
Wi-Fi You
WiFi You is a powerful app collecting millions of wifi passwords shared by end-users worldwide and storing & distributing them from a cloud server users can then access Wi-Fi passwords via the apps and share passwords amongst friends.
Wi-Fi WPS WPA Tester
Test for WPS WPA/WPA2 vulnerable routers and test them to various Wi-Fi exploits from your Android Device (Device requires Root).
CSploit
CSploit is one of the most complete and advanced IT security professional toolkit on Android.
Network Discovery
Computer/device discovery and port scanner for local area network automated from your Android device.
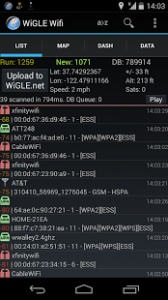
Wiggle – Wi-Fi Wardriving
Wiggle is an open-source wardriving app to netstumble, display and map found wireless networks and cell towers anywhere in the world, easily uploading to the http://wigle.net database. WiGLE was started in 2001 and now has over 250 million wifi networks worldwide.
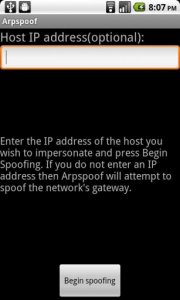
Arpspoof for Android
Android port of popular Arpspoof MITM Tool.
DroidSheep Guard
This Android app can protect you from MITM “Man in the Middle” attacks such as DroidSheep, Faceniff, etc. The app can alert you on unusual activity and give you options on what to do.
DroidBox
DroidBox was developed to offer a dynamic analysis of Android applications.
Fing Network Scanner
Fing Network Scanner Discovers what devices are connected to any Wi-Fi network, map devices, detect intruders, assess network security risks.
Kali Linux Nethunter
Kali NetHunter is an Android ROM overlay that includes a robust Mobile Penetration Testing Platform. The overlay includes a custom kernel, a Kali Linux chroot, and an accompanying Android application, which allows for easier interaction with various security tools and attacks. – Wikipedia
IMSI Catcher Sniffer
AIMSICD is an Android app to detect IMSI-Catchers. These IMSI catching devices are false mobile towers acting between the target mobile phone(s) and the real towers of service providers.
If you enjoyed this article please consider sharing it on social media and with your friend’s thanks for supporting HackingVision.
If you have found a spelling error, please, notify us by selecting that text and pressing Ctrl+Enter.
Источник
Android Hacking
There’s a big difference between hackers (people who like to experiment with computer systems to make them do unintended things) and attackers (criminals who exploit vulnerabilities in computer systems to gain access to data or processes).
In this article, we’ll cover the basics of hacking on Google’s widely used Android system.
Introduction to Android Hacking
Since its release in 2008, adoption of Android has soared, and it is now by far the most common mobile operating system.
The reasons for Android’s success are tied to its release as open source software, which allows application developers much better insight into its inner workings. The robust set of applications and extensions to Android translates to Android appearing on many different types of hardware.
In fact, Android has been so successful that it already captures more than 80% of the market share for mobile operating systems, with that number expected to climb to nearly 90% by 2022, according to Statista.
The same openness that makes Android appealing to mobile developers also makes it attractive to hackers. The open platform makes it easy to hack on. Of course, while most hackers simply enjoy experimenting with hardware and software, there are always going to be attackers who seek to exploit vulnerabilities. Download our free secure coding handbook to make sure your Android applications aren’t vulnerable to common exploits.
Secure Coding Handbook
Android Hacking Resources
There are hundreds of resources on the internet for people who want to get involved in Android hacking, from communities to lists of tools and guidebooks.
Here are a few places to get started:
- Veracode Community — Chat with security experts, hackers, and developers about all things application development, including security and modification.
- Android-Exploits — This is an open source guide on Android exploits and hacks from GitHub user sundaysec, with links to additional resources and tools.
- Hacking Android: 80 Pages of Experts’ Tutorials — You’ll find code and tutorials on Android security, hacking, and exploits from monthly hacking and cybersecurity magazine Hakin9.
- XDA Developers forum — This is an Android development and hacking community with millions of users.
Android Hacking Tools / Android Hacking Apps
In addition to manual coding, there are many applications built around hacking Android systems. These range from apps targeted at end users who want to extend their Android device’s battery life or customize other parts of its operating system to deep system hacks used by more sophisticated hackers and attackers.
Here are a few of the most popular:
- Apktool – This tool is used for reverse engineering third party, closed, binary Android applications.
- Dex2jar – This widely available tool works with Android .dex and Java .class files, enabling the conversion of one binary format to another.
- JD-GUI – This is a graphic utility tool that stands alone and displays Java sources from .class files.
How to Secure Your Android Device From Attackers
Although most people who use these hacking applications have no ill intent, they can also be used by attackers to find and exploit security flaws found in Android software.
Developers and organizations can use a secure software development lifecycle to minimize their risk of exposure to exploits that could see their customers’ private information leaked or their financial assets stolen or threatened.
The Three Biggest Threats to Android Devices
Threat One: Data in Transit
Mobile devices, including those running Android as an operating system, are susceptible to man-in-the-middle attacks and various exploits that hack into unsecured communications over public Wi-Fi networks and other wireless communication systems. By hijacking a user’s signal, attackers can impersonate legitimate web services, steal data, or intercept calls and text messages.
Threat Two: Untrustworthy App Stores
Untrustworthy app stores can cause headaches due to lack of security protocols. Ensure that your app store of choice for Android applications takes adequate security precautions and has a strong security review program in place. Sideloading, in which you install apps without an app store, is also a process to manage carefully due to a lack of foundational security measures.
Threat Three: SMS Trojans
Malicious apps can sometimes include SMS trojans, which come in the form of compromised applications. This type of app accesses a mobile device’s calling or text message capabilities, allowing them to do things like send text messages with malicious links to everyone in a user’s address book. These links can then be used by attackers to distribute computer worms and other malicious messages to fee-based services, incurring fees on behalf of the user and profiting scammers.
Three Ways to Protect Your Android Devices
Use TLS Encryption
OWASP shows that insufficient encryption is a big problem for many types of applications. By using Transport Layer Security (TLS), you can encrypt internet traffic of all types for securely generating and exchanging session keys. This protects data against most man-in-the-middle and network spying attacks.
Test Third-Party App Security
The best way to avoid malicious apps is to only use apps from the official Google Play store. Google Play uses significantly better security checks than third-party sites, some of which may contain hundreds of thousands of malicious apps. If you absolutely need to download an app from a third-party store, check its permissions before installing, and be on the lookout for apps which that for your identity or the ability to send messages to your contacts when they don’t need to.
Use Caution When Using SMS Payments
Set your Android phone to limit the ability of apps to automatically spend your money. Apps that ask for payment via SMS are a red flag and should be avoided if at all possible.
Veracode for Application Security
Veracode is designed to help developers and organizations secure their applications — whether they’re released on Android or any other system. Contact us today to learn how we can help you.
Источник