Andriller Android Tool Cracked
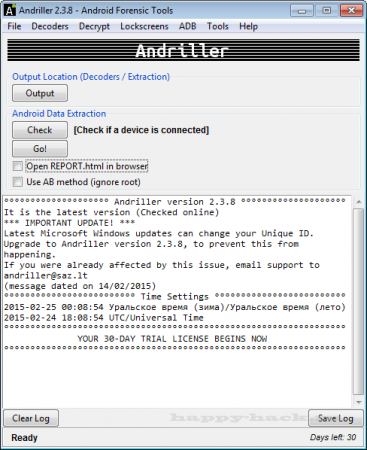
Andriller — программа предназначена для извлечения информации из Android-устройств.
Данную программу часто используют сотрудники правоохранительных органов и судебных инстанций.
Софт имеет множество функций, однако все они ориентированы исключительно на ознакомление с содержимым устройства.
Функционал:
1.Взлом экрана блокировки android
2.Подбор PIN-кода к андроиду
3.Взлом пароля от учетной записи владельца устройства
4.Расшифровка зашифрованных WhatsApp
5.Распаковка файлов резервных копий для Android
7.Автоматизированное извлечение данных
Эта функция требуют большой вычислительной мощности, так что лучше осуществлять локально, на своем компьютере
Методы описаны ниже:
Нам нужно получить «Соль» — это целое значение, которое требуется для взлома паролей.
Соль может быть как положительным, так и иметь отрицательные числа.
Значение соли может быть получено путем анализа файла setting.db или locksettings.db файла.
Если успешно получили значение соли то результат будет отображён в главном окне терминала.
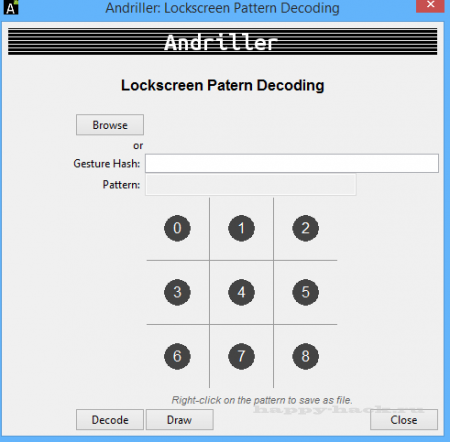
Взлом графического ключа на Android
Для декодирования графического ключа, выбираем режим «Gesture Pattern Decoding»
и нажимаем кнопку [Browse] и выберите файл gesture.key, расположенный в /data/system/gesture.key на Android устройстве.
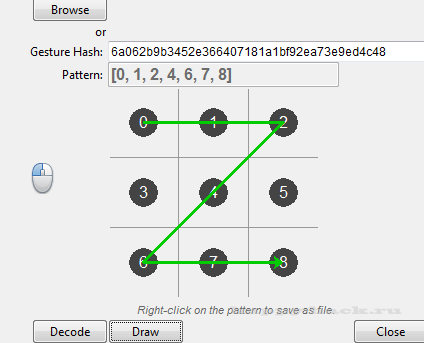
В противном случае, просто представите графический ключ шаблон хэш (шестнадцатеричные строки файла gesture.key), и нажмите кнопку [Decode].
При декодировании, в шаблоне отобразится спискок последовательностей.
Когда шаблон будет заполнен, нажмите кнопку [Draw] и модель отобразится в визуальной форме.
Щелкните правой кнопкой мыши на графическое поле пароля, и сохраните файл PostScrip
Совет: если вы хотите задать свои варианты графического пароля но не имеете хэш-ключа или значение, вы можете дважды щелкнуть на «disabled» в графическом поле шаблона, и включить поле для редактирования. Введите шаблон в виде списка, и нажмите кнопку [Draw].
Картина будет нарисована, которая может быть сохранена в виде файла.
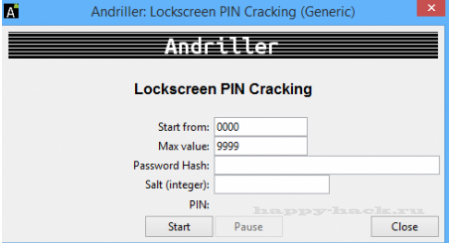
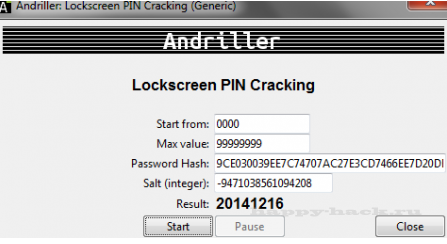
LockScreen PIN взлом пин-кода Android
1. Выберите минимальное и максимальное значение PIN-кода ;
По умолчанию, максимальное значение устанавливается 2. в 9999, возрастет, если требуется
2. Введите значение password.key файла
3. Введите значение соли в виде целого числа
4. Чтобы начать взлом пин-кода нажмите кнопку старт
5. После запуска взлома будет отображаться процент выполнения
Вы можете приостановить и возобновить взлом в любое время
Внимание ! Android устройства от Samsung использует другой тип хэширования паролей !
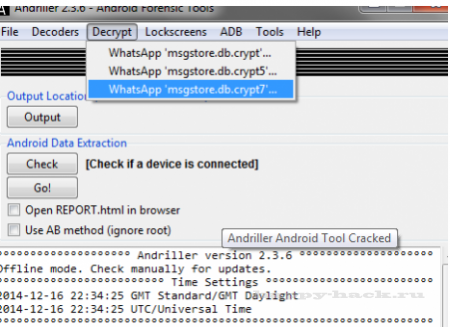
Расшифровки зашифрованных баз данных
Andriller поддерживает расшифровку зашифрованных WhatsApp баз данных:
Источник
Andriller
Andriller — is software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices. It has features, such as powerful Lockscreen cracking for Pattern, PIN code, or Password; custom decoders for Apps data from Android (some Apple iOS & Windows) databases for decoding communications. Extraction and decoders produce reports in HTML and Excel formats.
Features
- Automated data extraction and decoding
- Data extraction of non-rooted without devices by Android Backup (Android versions 4.x, varied/limited support)
- Data extraction with root permissions: root ADB daemon, CWM recovery mode, or SU binary (Superuser/SuperSU)
- Data parsing and decoding for Folder structure, Tarball files (from nanddroid backups), and Android Backup (backup.ab files)
- Selection of individual database decoders for Android apps
- Decryption of encrypted WhatsApp archived databases (.crypt to .crypt12, must have the right key file)
- Lockscreen cracking for Pattern, PIN, Password (not gatekeeper)
- Unpacking the Android backup files
- Screen capture of a device’s display screen
Python Requirements
It is highly advised to setup a virtual environment to install Andriller and its dependencies in it. However, it is not essential, and the global environment can also be used. Depending on how Python was setup, it may be needed to substitute python and pip to python3 and pip3 retrospectively for the instructions below.
Источник
Andriller android forensic tools oppo
Andriller CE (Community Edition)


Andriller — is software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices. It has features, such as powerful Lockscreen cracking for Pattern, PIN code, or Password; custom decoders for Apps data from Android (some Apple iOS & Windows) databases for decoding communications. Extraction and decoders produce reports in HTML and Excel formats.
- Automated data extraction and decoding
- Data extraction of non-rooted without devices by Android Backup (Android versions 4.x, varied/limited support)
- Data extraction with root permissions: root ADB daemon, CWM recovery mode, or SU binary (Superuser/SuperSU)
- Data parsing and decoding for Folder structure, Tarball files (from nanddroid backups), and Android Backup (backup.ab files)
- Selection of individual database decoders for Android apps
- Decryption of encrypted WhatsApp archived databases (.crypt to .crypt12, must have the right key file)
- Lockscreen cracking for Pattern, PIN, Password (not gatekeeper)
- Unpacking the Android backup files
- Screen capture of a device’s display screen
- 3.6-3.9 (64-bit version recommended)
It is highly advised to setup a virtual environment to install Andriller and its dependencies in it. However, it is not essential, and the global environment can also be used. Depending on how Python was setup, it may be needed to substitute python and pip to python3 and pip3 retrospectively for the instructions below.
Источник
[TOOL][Forensic] Andriller — data acquisition from Android devices
Breadcrumb
den4uk
Member
Moderators: if this thread is in wrong place please forgive and move it to a location best suitable for this thread.
Self-introduction I come from law-enforcement digital forensics background aimed at data extractions from mobile devices.
I would like to introduce a tool that I created.
Andriller
http://andriller.com
Andriller is a Windows GUI forensic tool, that performs read-only, forensically sound, non-destructive acquisition from Android devices. The executable is run from a terminal or by executing directly; it produces results in the terminal window, and a report in a HTML format.
Download Andriller from the download page and install. To use the software you need to obtain a license key (free trial available). Instructions on doing this will be provided on the page
Note: Android version 4.2.2+ requires to authorise the PC to accept RSA fingerprint. Please do so, and tick the box to remember for future.
Note: Devices with Superuser or SuperSU App require to authorise root access from an unlocked screen. Please grand permissions if requested.
Once andriller is executed, it will produce permilinary results in the terminal window; for rooted devices it will download and decode the content automatically. It will produce a new folder in the location where it was executed, where the main «REPORT.html» file can be opened in a web browser.
Supported data extraction:
Non-root devices (Android versions 2.x):
— Android device make and model
— IMEI, build version, OS version
— Wifi mac address
— Time and date check
— SIM card details (for a some Galaxy Sx devices only)
— Synchronised accounts
Non-rooted devices (via backup method, Android versions 4.x and above)
— Wi-Fi passwords (WPA-PSK/WEP)
— Call logs (Samsung) register
— Android browser saved passwords
— Android browser browsing history
— Google Chrome saved passwords
— Google Chrome browsing history
— Facebook* chat messages
— Facebook* user viewed photographs
— Facebook* user notifications
— WhatsApp* contacts list
— WhatsApp* chat messages
— Kik Messenger* chat messages
— BBM* chat messages (Blackberry Messenger)
— Viber* chat messages
Rooted devices (via root adbd or ‘su’ binary, any Android versions):
— Security lockscreen pattern gesture extraction (decoding online)
— Security lockscreen PIN code cracking (up to 8 digits long)
— Wi-Fi passwords (WPA-PSK/WEP)
— Synchronised accounts and profile picture
— Bluetooth mac address and name
— Phonebook contacts
— Call logs register
— Call logs (Samsung) register
— SMS messages
— Android browser saved passwords
— Android browser browsing history
— Google Chrome saved passwords
— Google Chrome browsing history
— Facebook* friends list
— Facebook* chat messages
— Facebook* user viewed photographs
— Facebook* user notifications
— WhatsApp* contacts list
— WhatsApp* chat messages
— Kik Messenger* chat messages
— BBM* chat messages (Blackberry Messenger)
— Viber* chat messages
* = if an Application is installed
Andriller comes with absolutely no warranty. Even though Andriller was written in a way to be a forensically sound read-only utility, I do not take any responsibility to any damage or harm caused to your computer systems or your Android devices, which may be believed to have been caused by executing Andriller. I also do not take any responsibility of any unsolicited, non-consensual or unlawful misuses of this utility. It is the end user’s responsibility to believe an appropriate consent or a lawful excuse was obtained if the utility is used with an other’s Android devices, and they are aware what the utility does.
Источник
Andriller : Software Utility With A Collection Of Forensic Tools For Smartphones
Andriller is software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices.
It has features, such as powerful Lockscreen cracking for Pattern, PIN code, or Password; custom decoders for Apps data from Android (some Apple iOS & Windows) databases for decoding communications. Extraction and decoders produce reports in HTML and Excel formats.
Features
- Automated data extraction and decoding
- Data extraction of non-rooted without devices by Android Backup (Android versions 4.x, varied/limited support)
- Data extraction with root permissions: root ADB daemon, CWM recovery mode, or SU binary (Superuser/SuperSU)
- Data parsing and decoding for Folder structure, Tarball files (from nanddroid backups), and Android Backup (backup.ab files)
- Selection of individual database decoders for Android apps
- Decryption of encrypted WhatsApp archived databases (.crypt to .crypt12, must have the right key file)
- Lockscreen cracking for Pattern, PIN, Password (not gatekeeper)
- Unpacking the Android backup files
- Screen capture of a device’s display screen
Python Requirements
- 3.6+ (64-bit version recommended)
It is highly advised to setup a virtual environment to install Andriller and its dependencies in it. However, it is not essential, and the global environment can also be used. Depending on how Python was setup, it may be needed to substitute python and pip to python3 and pip3 retrospectively for the instructions below.
Windows only: when installing Python from https://www.python.org, make sure Add Python to PATH is ticked.
System Dependencies
[Ubuntu/Debian] Install from Terminal:
$ sudo apt-get install android-tools-adb python3-tk
[Mac] Install from brew cask:
$ brew cask install android-platform-tools
[Windows] : Included.
Installation (Recommended way)
Create a virtual environment using Python 3:
$ python3 -m venv env
Activate the virtual environment:
$ source env/bin/activate
Install Andriller with its Python dependencies (same command to upgrade it):
(env) $ pip install andriller -U
Quick Start (run GUI)
(env) $ python -m andriller
Источник