- Andriller Android Tool Cracked
- Andriller
- Review
- Free Download
- specifications
- An easy to use software solution that allows you to extract a very large amount of information from an Android powered device in a few steps
- What’s new in Andriller 3.6.0:
- Use a large number of database decoders
- Automatically generate reports
- Crack passwords and PINs
- Conclusion
- Andriller 2.6.1.1
- andriller 3.6.1
- Navigation
- Project links
- Statistics
- Classifiers
- Project description
- Andriller CE (Community Edition)
- Features
- Python Requirements
- System Dependencies
- Installation (Recommended way)
- Quick Start (run GUI)
- License
- Contributing
- Bug Tracker
- Donations
- Andriller android tool cracked
Andriller Android Tool Cracked
Andriller — программа предназначена для извлечения информации из Android-устройств.
Данную программу часто используют сотрудники правоохранительных органов и судебных инстанций.
Софт имеет множество функций, однако все они ориентированы исключительно на ознакомление с содержимым устройства.
Функционал:
1.Взлом экрана блокировки android
2.Подбор PIN-кода к андроиду
3.Взлом пароля от учетной записи владельца устройства
4.Расшифровка зашифрованных WhatsApp
5.Распаковка файлов резервных копий для Android
7.Автоматизированное извлечение данных
Эта функция требуют большой вычислительной мощности, так что лучше осуществлять локально, на своем компьютере
Методы описаны ниже:
Нам нужно получить «Соль» — это целое значение, которое требуется для взлома паролей.
Соль может быть как положительным, так и иметь отрицательные числа.
Значение соли может быть получено путем анализа файла setting.db или locksettings.db файла.
Если успешно получили значение соли то результат будет отображён в главном окне терминала.
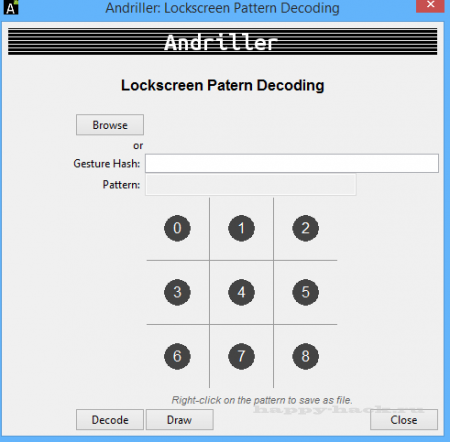
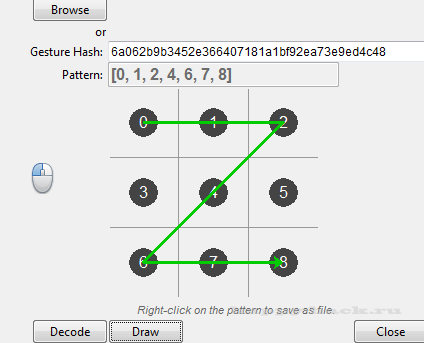
Взлом графического ключа на Android
Для декодирования графического ключа, выбираем режим «Gesture Pattern Decoding»
и нажимаем кнопку [Browse] и выберите файл gesture.key, расположенный в /data/system/gesture.key на Android устройстве.
В противном случае, просто представите графический ключ шаблон хэш (шестнадцатеричные строки файла gesture.key), и нажмите кнопку [Decode].
При декодировании, в шаблоне отобразится спискок последовательностей.
Когда шаблон будет заполнен, нажмите кнопку [Draw] и модель отобразится в визуальной форме.
Щелкните правой кнопкой мыши на графическое поле пароля, и сохраните файл PostScrip
Совет: если вы хотите задать свои варианты графического пароля но не имеете хэш-ключа или значение, вы можете дважды щелкнуть на «disabled» в графическом поле шаблона, и включить поле для редактирования. Введите шаблон в виде списка, и нажмите кнопку [Draw].
Картина будет нарисована, которая может быть сохранена в виде файла.
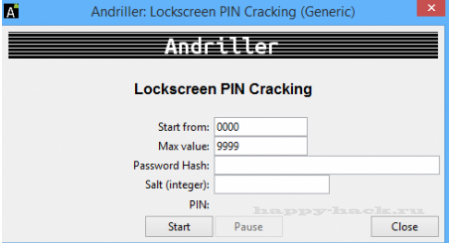
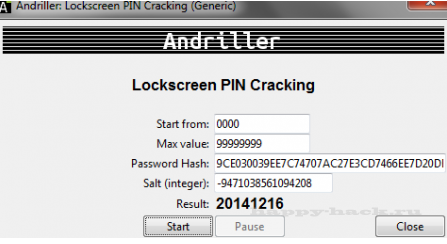
LockScreen PIN взлом пин-кода Android
1. Выберите минимальное и максимальное значение PIN-кода ;
По умолчанию, максимальное значение устанавливается 2. в 9999, возрастет, если требуется
2. Введите значение password.key файла
3. Введите значение соли в виде целого числа
4. Чтобы начать взлом пин-кода нажмите кнопку старт
5. После запуска взлома будет отображаться процент выполнения
Вы можете приостановить и возобновить взлом в любое время
Внимание ! Android устройства от Samsung использует другой тип хэширования паролей !
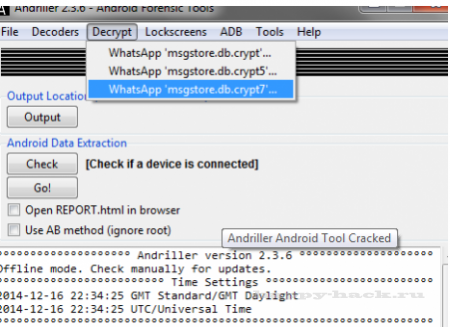
Расшифровки зашифрованных баз данных
Andriller поддерживает расшифровку зашифрованных WhatsApp баз данных:
Источник
Andriller
Review
Free Download
specifications
An easy to use software solution that allows you to extract a very large amount of information from an Android powered device in a few steps
What’s new in Andriller 3.6.0:
- GUI restructured
- Bugfix with WA decoder
- Dependencies updated
- CI/CD pipelines changed to Github Actions
Read the full changelog
Andriller is a tool that offers Android smartphone users the possibility to obtain data from them using powerful forensic tools. They provide the means to automatically extract data from non-rooted devices using a set of decoders.
Use a large number of database decoders
The application displays a fairly comprehensive interface which makes it easy to use by just about anyone. Its overall GUI design is rather plain and simple but it offers the advantage of being able to quickly and easily access all its features and tools from the main window.
Andriller enables you to import a number of database files which are processed by the application and used to generate reports. Once it manages to decode the data, it’s made available to you in a HTML file.
With this tool you can use decoders for Android devices which can obtain account information, messages, contacts, call history, browser data and much more.
Automatically generate reports
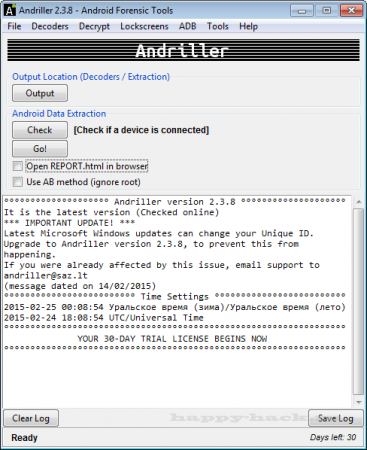
Getting the aforementioned data types is itself a very simple process. All you have to do is connect your phone to the PC, choose the output folder for the report, check to see if the phone is recognized and then, with a final click on the ‘Go!’ button, the app starts performing its job.
Depending on the amount of data that is to be extracted, the task might take a couple of minutes but Andriller notifies you when it’s done and the new HTML file will contain an easy to follow table with all the required data.
Crack passwords and PINs
Andriller can also help you on a bad day when you forget your lockscreen combination or your PIN number. It makes use of the gesture.key, setting.db or locksettings.db files in order to get the data needed to crack passwords.
Conclusion
Andriller is by all means a very capable tool that has a lot of potential to extract sensitive data from your Android smartphone and considering this fact, it needs to be used responsibly and it goes without saying that if you intend to use it, take all the necessary precautions and backup your phone.
Источник
Andriller 2.6.1.1
Andriller can provide you with a huge amount of forensic information about Android-powered smartphones. The application is capable of retrieving and decoding information from the phone’s operating system or from installed apps quite fast. It comes with other useful features as well, including lockscreen pattern and PIN acquisition.
The software is offered free of charge and you can have it up and running in no time. It works on all modern Windows platforms and it doesn’t require any special tools or services. Also, the application doesn’t use too much disk space, RAM or processing power, so you can run it even on older computers.
If an Android smartphone is connected to your computer, you can get started right away. The user interface has a simple layout and its controls are easy to master. You may click a button to check if the phone is properly connected or you can start retrieving forensic information right away, with a single click. An events log is presented on the same interface, so you will know what components the application is working on. The acquired information will be automatically in an HTML report, in a location of your choice.
Besides gathering information about the operating system and the installed apps, the software can perform other operations as well. As previously mentioned, the software can decode gesture patterns for the lock screen, crack PINs, brute force passwords and much more. The supported operations are neatly categorized in a series of menus, on the upper edge of the interface. Furthermore, preparing and executing them is quite easy, even for novice users.
Anything you wish to know about a smartphone, including its gesture pattern and PIN can be retrieved at a moment’s notice with Andriller.
Pros:
The software can retrieve a wide range of forensic data about Android smartphones. It can also crack passwords, decode gestures and perform many other operations. The software is free, lightweight and easy to install.
Cons:
There are no obvious issues to mention.
Источник
andriller 3.6.1
pip install andriller Copy PIP instructions
Released: Oct 31, 2021
Andriller CE | Android Forensic Tools
Navigation
Project links
Statistics
View statistics for this project via Libraries.io, or by using our public dataset on Google BigQuery
License: MIT License (MIT License)
Tags andriller, android, forensic, forensics, adb, dfir
Requires: Python >=3.6, denco
Classifiers
- License
- OSI Approved :: MIT License
- Operating System
- OS Independent
- Programming Language
- Python :: 3
Project description
Andriller CE (Community Edition)
Andriller — is software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices. It has features, such as powerful Lockscreen cracking for Pattern, PIN code, or Password; custom decoders for Apps data from Android (some Apple iOS & Windows) databases for decoding communications. Extraction and decoders produce reports in HTML and Excel formats.
Features
- Automated data extraction and decoding
- Data extraction of non-rooted without devices by Android Backup (Android versions 4.x, varied/limited support)
- Data extraction with root permissions: root ADB daemon, CWM recovery mode, or SU binary (Superuser/SuperSU)
- Data parsing and decoding for Folder structure, Tarball files (from nanddroid backups), and Android Backup (backup.ab files)
- Selection of individual database decoders for Android apps
- Decryption of encrypted WhatsApp archived databases (.crypt to .crypt12, must have the right key file)
- Lockscreen cracking for Pattern, PIN, Password (not gatekeeper)
- Unpacking the Android backup files
- Screen capture of a device’s display screen
Python Requirements
- 3.6-3.9 (64-bit version recommended)
It is highly advised to setup a virtual environment to install Andriller and its dependencies in it. However, it is not essential, and the global environment can also be used. Depending on how Python was setup, it may be needed to substitute python and pip to python3 and pip3 retrospectively for the instructions below.
Windows only: when installing Python from https://www.python.org, make sure Add Python to PATH is ticked.
System Dependencies
[Ubuntu/Debian] Install from Terminal:
[Mac] Install from brew cask:
Installation (Recommended way)
Create a virtual environment using Python 3:
Activate the virtual environment (Linux/Mac):
Activate the virtual environment (Windows):
Install Andriller with its Python dependencies (same command to upgrade it):
Quick Start (run GUI)
License
Contributing
Contributions are welcome, please make your pull requests to the dev branch of the repository.
Bug Tracker
Bugs and issues can be submitted in the (Issues) section.
Donations
You may make donations to the projects, or you can also just buy me a beer:
Источник
Andriller android tool cracked
Andriller CE (Community Edition)


Andriller — is software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices. It has features, such as powerful Lockscreen cracking for Pattern, PIN code, or Password; custom decoders for Apps data from Android (some Apple iOS & Windows) databases for decoding communications. Extraction and decoders produce reports in HTML and Excel formats.
- Automated data extraction and decoding
- Data extraction of non-rooted without devices by Android Backup (Android versions 4.x, varied/limited support)
- Data extraction with root permissions: root ADB daemon, CWM recovery mode, or SU binary (Superuser/SuperSU)
- Data parsing and decoding for Folder structure, Tarball files (from nanddroid backups), and Android Backup (backup.ab files)
- Selection of individual database decoders for Android apps
- Decryption of encrypted WhatsApp archived databases (.crypt to .crypt12, must have the right key file)
- Lockscreen cracking for Pattern, PIN, Password (not gatekeeper)
- Unpacking the Android backup files
- Screen capture of a device’s display screen
- 3.6-3.9 (64-bit version recommended)
It is highly advised to setup a virtual environment to install Andriller and its dependencies in it. However, it is not essential, and the global environment can also be used. Depending on how Python was setup, it may be needed to substitute python and pip to python3 and pip3 retrospectively for the instructions below.
Источник