- Redirect URI (reply URL) restrictions and limitations
- Maximum number of redirect URIs
- Maximum URI length
- Redirect URIs in application vs. service principal objects
- Supported schemes
- Localhost exceptions
- Prefer 127.0.0.1 over localhost
- Restrictions on wildcards in redirect URIs
- Use a state parameter
- Next steps
- Redirect URLs for Native Apps
- App-Claimed https URL Redirection
- Custom URL Scheme
- Custom URL Scheme Namespaces
- Want to implement OAuth 2.0 without the hassle?
- Android get image from url SingleClientConnManager problem
- Answers
Redirect URI (reply URL) restrictions and limitations
A redirect URI, or reply URL, is the location where the authorization server sends the user once the app has been successfully authorized and granted an authorization code or access token. The authorization server sends the code or token to the redirect URI, so it’s important you register the correct location as part of the app registration process.
The Azure Active Directory (Azure AD) application model specifies these restrictions to redirect URIs:
Redirect URIs must begin with the scheme https . There are some exceptions for localhost redirect URIs.
Redirect URIs are case-sensitive and must match the case of the URL path of your running application. For example, if your application includes as part of its path . /abc/response-oidc , do not specify . /ABC/response-oidc in the redirect URI. Because the web browser treats paths as case-sensitive, cookies associated with . /abc/response-oidc may be excluded if redirected to the case-mismatched . /ABC/response-oidc URL.
Redirect URIs not configured with a path segment are returned with a trailing slash (‘ / ‘) in the response. This applies only when the response mode is query or fragment .
- https://contoso.com is returned as https://contoso.com/
- http://localhost:7071 is returned as http://localhost:7071/
Redirect URIs that contain a path segment are not appended with a trailing slash in the response.
- https://contoso.com/abc is returned as https://contoso.com/abc
- https://contoso.com/abc/response-oidc is returned as https://contoso.com/abc/response-oidc
Maximum number of redirect URIs
This table shows the maximum number of redirect URIs you can add to an app registration in the Microsoft identity platform.
| Accounts being signed in | Maximum number of redirect URIs | Description |
|---|---|---|
| Microsoft work or school accounts in any organization’s Azure Active Directory (Azure AD) tenant | 256 | signInAudience field in the application manifest is set to either AzureADMyOrg or AzureADMultipleOrgs |
| Personal Microsoft accounts and work and school accounts | 100 | signInAudience field in the application manifest is set to AzureADandPersonalMicrosoftAccount |
Maximum URI length
You can use a maximum of 256 characters for each redirect URI you add to an app registration.
Redirect URIs in application vs. service principal objects
- Always add redirect URIs to the application object only.
- Do not add redirect URI values to a service principal because these values could be removed when the service principal object syncs with the application object. This could happen due to any update operation which triggers a sync between the two objects.
Supported schemes
HTTPS: The HTTPS scheme ( https:// ) is supported for all HTTP-based redirect URIs.
HTTP: The HTTP scheme ( http:// ) is supported only for localhost URIs and should be used only during active local application development and testing.
| Example redirect URI | Validity |
|---|---|
| https://contoso.com | Valid |
| https://contoso.com/abc/response-oidc | Valid |
| https://localhost | Valid |
| http://contoso.com/abc/response-oidc | Invalid |
| http://localhost | Valid |
| http://localhost/abc | Valid |
Localhost exceptions
Per RFC 8252 sections 8.3 and 7.3, «loopback» or «localhost» redirect URIs come with two special considerations:
- http URI schemes are acceptable because the redirect never leaves the device. As such, both of these URIs are acceptable:
- http://localhost/myApp
- https://localhost/myApp
- Due to ephemeral port ranges often required by native applications, the port component (for example, :5001 or :443 ) is ignored for the purposes of matching a redirect URI. As a result, all of these URIs are considered equivalent:
- http://localhost/MyApp
- http://localhost:1234/MyApp
- http://localhost:5000/MyApp
- http://localhost:8080/MyApp
From a development standpoint, this means a few things:
Do not register multiple redirect URIs where only the port differs. The login server will pick one arbitrarily and use the behavior associated with that redirect URI (for example, whether it’s a web -, native -, or spa -type redirect).
This is especially important when you want to use different authentication flows in the same application registration, for example both the authorization code grant and implicit flow. To associate the correct response behavior with each redirect URI, the login server must be able to distinguish between the redirect URIs and cannot do so when only the port differs.
To register multiple redirect URIs on localhost to test different flows during development, differentiate them using the path component of the URI. For example, http://localhost/MyWebApp doesn’t match http://localhost/MyNativeApp .
The IPv6 loopback address ( [::1] ) is not currently supported.
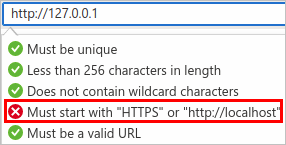
Prefer 127.0.0.1 over localhost
To prevent your app from being broken by misconfigured firewalls or renamed network interfaces, use the IP literal loopback address 127.0.0.1 in your redirect URI instead of localhost . For example, https://127.0.0.1 .
You cannot, however, use the Redirect URIs text box in the Azure portal to add a loopback-based redirect URI that uses the http scheme:
To add a redirect URI that uses the http scheme with the 127.0.0.1 loopback address, you must currently modify the replyUrlsWithType attribute in the application manifest.
Restrictions on wildcards in redirect URIs
Wildcard URIs like https://*.contoso.com may seem convenient, but should be avoided due to security implications. According to the OAuth 2.0 specification (section 3.1.2 of RFC 6749), a redirection endpoint URI must be an absolute URI.
Wildcard URIs are currently unsupported in app registrations configured to sign in personal Microsoft accounts and work or school accounts. Wildcard URIs are allowed, however, for apps that are configured to sign in only work or school accounts in an organization’s Azure AD tenant.
To add redirect URIs with wildcards to app registrations that sign in work or school accounts, use the application manifest editor in App registrations in the Azure portal. Though it’s possible to set a redirect URI with a wildcard by using the manifest editor, we strongly recommend you adhere to section 3.1.2 of RFC 6749. and use only absolute URIs.
If your scenario requires more redirect URIs than the maximum limit allowed, consider the following state parameter approach instead of adding a wildcard redirect URI.
Use a state parameter
If you have several subdomains and your scenario requires that, upon successful authentication, you redirect users to the same page from which they started, using a state parameter might be helpful.
In this approach:
- Create a «shared» redirect URI per application to process the security tokens you receive from the authorization endpoint.
- Your application can send application-specific parameters (such as subdomain URL where the user originated or anything like branding information) in the state parameter. When using a state parameter, guard against CSRF protection as specified in section 10.12 of RFC 6749).
- The application-specific parameters will include all the information needed for the application to render the correct experience for the user, that is, construct the appropriate application state. The Azure AD authorization endpoint strips HTML from the state parameter so make sure you are not passing HTML content in this parameter.
- When Azure AD sends a response to the «shared» redirect URI, it will send the state parameter back to the application.
- The application can then use the value in the state parameter to determine which URL to further send the user to. Make sure you validate for CSRF protection.
This approach allows a compromised client to modify the additional parameters sent in the state parameter, thereby redirecting the user to a different URL, which is the open redirector threat described in RFC 6819. Therefore, the client must protect these parameters by encrypting the state or verifying it by some other means, like validating the domain name in the redirect URI against the token.
Next steps
Learn about the app registration Application manifest.
Источник
Redirect URLs for Native Apps
Native applications are clients installed on a device, such as a desktop application or native mobile application. There are a few things to keep in mind when supporting native apps related to security and user experience.
The authorization endpoint normally redirects the user back to the client’s registered redirect URL. Depending on the platform, native apps can either claim a URL pattern, or register a custom URL scheme that will launch the application. For example, an iOS application may register a custom protocol such as myapp:// and then use a redirect_uri of myapp://callback .
App-Claimed https URL Redirection
Some platforms, (Android, and iOS as of iOS 9), allow the app to override specific URL patterns to launch the native application instead of a web browser. For example, an application could register https://app.example.com/auth and whenever the web browser attempts to redirect to that URL, the operating system launches the native app instead.
If the operating system does support claiming URLs, this method should be used. This allows the identity of the native application to be guaranteed by the operating system. If the operating system does not support this, then the app will have to use a custom URL scheme instead.
Custom URL Scheme
Most mobile and desktop operating systems allow apps to register a custom URL scheme that will launch the app when a URL with that scheme is visited from the system browser.
Using this method, the native app starts the OAuth flow as normal, by launching the system browser with the standard authorization code parameters. The only difference is that the redirect URL will be a URL with the app’s custom scheme.
When the authorization server sends the Location header intending to redirect the user to myapp://callback#token=. , the phone will launch the application and the app will be able to resume the authorization process, parsing the access token from the URL and storing it internally.
Custom URL Scheme Namespaces
Since there is no centralized method of registering URL schemes, apps have to do their best to choose URL schemes that won’t conflict with each other.
Your service can help by requiring the URL scheme to follow a certain pattern, and only allow the developer to register a custom scheme that matches that pattern.
For example, Facebook generates a URL scheme for every app based on the app’s client ID. For example, fb00000000:// where the numbers correspond to the app’s client ID. This provides a reasonably sure method of generating globally unique URL schemes, since other apps are unlikely to use a URL scheme with this pattern.
Another option for apps is to use the reverse domain name pattern with a domain that is under the control of the app’s publisher. This is also something that can be enforced by the service.
Want to implement OAuth 2.0 without the hassle?
We’ve built API access management as a service that is secure, scalable, and always on, so you can ship a more secure product, faster.
Источник
Android get image from url SingleClientConnManager problem
I am using following code to get the images of a logo and save it in the database.
The first image added perfectly, but rest of the cases it is not working and giving the following warning.
What is problem in my code? What to change to solve it?
Answers
You need to consume the content before you can reuse the connection. This may be a duplicate of Exception using HttpRequest.execute(): Invalid use of SingleClientConnManager: connection still allocated
I think that you need to consume the content even if the response code is not HttpStatus.SC_OK, and in your exception handlers.
Run the app in debug mode and set a breakpoint on if (requestCode == SELECT_PICTURE) and inspect each variable as you step through to ensure it is being set as expected. If you are getting a NPE on img.setImageURI(selectedImageUri); then either img or selectedImageUri are not set.
Putting a ‘/’ at the end of URL causes the redirect to happen because your server likes urls that end in ‘/’. POST is fully supported by the URL your server redirects you to, but the client is executing a GET request when it behaves according to your setRedirecting() call (cURL does the same exact thing with the -L switch) The fix is to either put a ‘/’ at the end of URL, or to grab the Location header from the response yourself and then initiate another POST request manually.
This can be observed in wireshark. You can test the theory by trying to perform a GET request with your browser to the URL with a slash appended to it. That will cause the browser to get a 405. Here’s the fixed code for Android, this code uses the simple fix of appending a ‘/’ to the URL (not production ready):
You declared ImageView as
You have to set Image on ImageView. It should be like this
If you are using a client which extends AbstractHttpClient, such as DefaultHttpClient you can do the following to get the cookies after executing the request.
Источник