- LUKS2 Encrypted Container on Android
- Setup
- Container
- Filesystem
- Simple: ExFAT (recommended)
- More secure: Ext4
- Shell script
- Unlock the container
- Mounting
- ExFAT
- Bind default folders
- Download
- Android mount encrypt container
- Manage TrueCrypt containers on your Android device
- EDS Lite
- Closing Words
- TrueCrypt Compatible Encryption on Android with EDS
- What is Encrypted Data Storage?
- Features of the Lite version
- Benefits of the Pro version
- Competition
LUKS2 Encrypted Container on Android
This post describes how dm-crypt / LUKS container files can be mounted on Android, completely with the standard command line open source tools. It is written for Android 10, but should also work on older versions. Root permissions are required.
Setup
The builtin android toybox does not include the required tools. Instead I recommend using Termux, a Terminal emulator app with an extensive package collection. So open Termux and execute:
This enables the repository containing root packages and installs the most important tools. Especially cryptsetup for handling the LUKS headers, tsu to run commands/shell as root while keeping the correct PATH to access the termux programs from /data/data/com.termux/files/usr/bin/ easily.
After installation in Termux you can also run these binaries from another terminal emulator app or adb shell, if you prefer that. Following steps must be all run from a root shell (su/tsu).
Container
If you already have an encrypted container/partition you can just copy/connect it to the phone and skip this step. Otherwise create a empty file with truncate (or dd ), you can choose any size you like, I use 5 GB here. Also don’t forget to replace test.img with a meaningful filename or path. /sdcard/ maps to the internal storage in /storage/emulated/0/ , for external microSD or USB storage look in /storage/ID/ .
cryptsetup will ask interactively for a password.
Filesystem
Filesystem support depends on the device kernel and can differ, use cat /proc/filesystems to check what is in the list. ExFAT and Ext4 should be available on almost any device though.
Native Linux filesystems (like ext4) make it a bit more complicated, because they support unix permissions on individual files and they are set by the Android system. Use exFAT if you want easy access to files created from other apps. This is more convenient, but if you prefer more security from possibly malicious apps you can use ext4 to get some sort scoped storage (from Android 11), where apps can only access files they created themselves.
Simple: ExFAT (recommended)
First step is to open the container with your passphrase, then simply create the fs:
Note: I could not find a package in Termux that contains mkfs.exfat , so you have to use a desktop linux instead for this step.
More secure: Ext4
Almost the same as with exFAT, open the container and make the fs:
Permissions on the mount point have to be fixed after mounting initially. Keep in mind that on Android every app runs as own user (name in u_APPID schema) and every file created by an app though the Android framework gets restrictive -rwx—— permissions for group and others, so they are not visible by all other apps. You have to manually chmod/chown after creation to make them accessible if required (more on that in the mount section).
Shell script
First the usual setup, set to abort on errors and check if we are running as root:
Unlock the container
Unlocking works simply with cryptsetup again, I have just added a check if the it is already open.
Mounting
Because of the Android architecture a few additional steps are required to get it properly mounted. Every app has its own mount namespace, that means mounts from other apps are not visible, so it would be per default only available to Termux or whatever Terminal you use and that is no good. A fix is to enter the root namespace and do it there, then the mount propagates to all child app namespaces:
Here -t specifies the target namespace, use simply PID 1, which is the init process. -m stands for mount namespace and then follows the command, in this case a bash shell with the commands piped into it. Instead of this extra script you can also omit the last part and type it manually into the shell.
Following commands go all into the mounts.sh script (must be run inside the init namespace).
Another Android specialty are the different storage views: default, read and write. They were added with Android 6 (Marshmallow) to be able to change permissions on runtime, through bind mounting the needed view into the specific app namespaces. Therefore the location is /mnt/runtime/VIEW and we have to mount there to make it available to the apps with correct permissions. It is enough to mount into the write view, because with the “simplified” permission model apps that got storage access granted see always this view. So to mount on the internal storage to luks/ start with:
In addition create the mount point, if it does not already exist.
ExFAT
Then finally mount it like that:
ExFAT does not save unix permissions or the SELinux context, so it is important to specify suitable values for mounting. GID 9997 equals group everybody , this makes it usable with all apps.
Ext4 requires similar values, but this time it can not be specified as mount option, instead it must be set on the mount point afterwards:
Now you should be able to create files and folders from a file manager and other apps inside the mountpoint. As already mentioned, these will be app specific (in this case for appID 256) and don’t allow access for others:
To make them “public” to other apps run the chgrp / chmod commands from above on the whole mountpoint again or just on a specific subdirectory.
Bind default folders
Some apps don’t allow custom data locations, for example many camera apps always write into DCIM . A solution is to bind mount these folder to some folders inside the encrypted mount:
Download
The complete two parts of the script can be downloaded here: luks.sh + mounts.sh
Place them in the same directory on the phone, for example with adb push *.sh /sdcard/ .
Источник
Android mount encrypt container
Для функционирования программы необходимы права root пользователя.
Краткое описание:
Шифрование данных на устройстве и в Dropbox.
Описание:
EncFS на Android
Это бесплатное и с открытым исходным кодом решение шифрования файлов на основе EncFS (http://www.arg0.net/encfs).
Сначала прочтите это: Приложение находится в стадии разработки. Предназначено только для опытных пользователей Android. Монтаж EncFS и TrueCrypt пространств требует ROOT и поддержку ядра FUSE (в некоторых CyanogenMod ROM). Загрузка с/на Dropbox и создание EncFS пространства на вашем телефоне поддерживается на всех устройствах.
ОБРАТНАЯ СВЯЗЬ: Пожалуйста, отправьте отчет, если вы испытываете принудительный выход, и направьте свои замечания, предложения, сообщения об ошибке и патчи: http://code.google.com/p/cryptonite/issues/list
На некоторых устройствах, приложение не запускается. Информация об этой ошибке будет особенно ценится, потому что я не могу воспроизвести это на данный момент. Смотрите https://code.google.com/p/cryptonite/issues/detail?id=9
БЕЗОПАСНОСТЬ: Читайте о важных соображениях безопасности: http://code.google.com/p/cryptonite/wiki/S. yConsiderations
Разрешения:
Интернет: требуется разрешение на доступ к Dropbox.
SD-карта: требуется доступ для чтения и записи файлов.
FAQ: Почему я не могу расшифровать и зашифровать файлы на лету?
Почему я не могу создать тома EncFS на устройстве Motorola?
Почему я не могу получить доступ к любой папке в моем пространстве Dropbox?
Почему я должен предоставлять права суперпользователя для подключения томов EncFS и TrueCrypt?
Смотрите http://code.google.com/p/cryptonite/wiki/F. yAskedQuestions
Установка на нерутованных устройствах: Если вы хотите получить без root поддержку приложения для CyanogenMod, пожалуйста, голосуйте за это повышением и / или доведите это до сведения CM разработчиков:
https://code.google.com/p/cyanogenmod/issues/detail?id=5034
Исходный код: доступна https://code.google.com/p/cryptonite/source/checkout
Русский интерфейс: Неизвестно
версия: 0.6.12
Версия 0.6.8
Версия 0.6.6
Версия 0.6.5
Версия 0.6.3
Версия 0.6.2
Версия 0.6.0
Версия 0.4.5
Версия 0.4.4
Сообщение отредактировал Gridzilla — 07.12.15, 15:55
Источник
Manage TrueCrypt containers on your Android device
I used the encryption software TrueCrypt for several years on all of my Windows PCs to protect data on the devices. I usually encrypt all partitions using the application so that the data is only accessible in encrypted form when the PC is turned off, and so that someone who wants access to the PC needs to supply the password on boot that decrypts the data.
Sometimes, I do make use of TrueCrypt containers instead. Container files are usually smaller files that work similar as they protect files that you move into them from third-party access. The main advantage here is that they are flexible to use. Not only can you select any file name and extension, their smaller size makes them ideal for moving them to other devices or systems, or for hiding them in plain sight.
One of the limitations of TrueCrypt up until now was that there was no official support for mobile devices. While you can move the container files to your Android device, for instance by using Dropbox, you cannot really open them on it.
Update: TrueCrypt development ended under mysterious circumstances. Encryption programs like VeraCrypt were created that are based on TrueCrypt’s format. Recent versions of EDS support VeraCrypt, LUKS, and EncFs container formats as well.
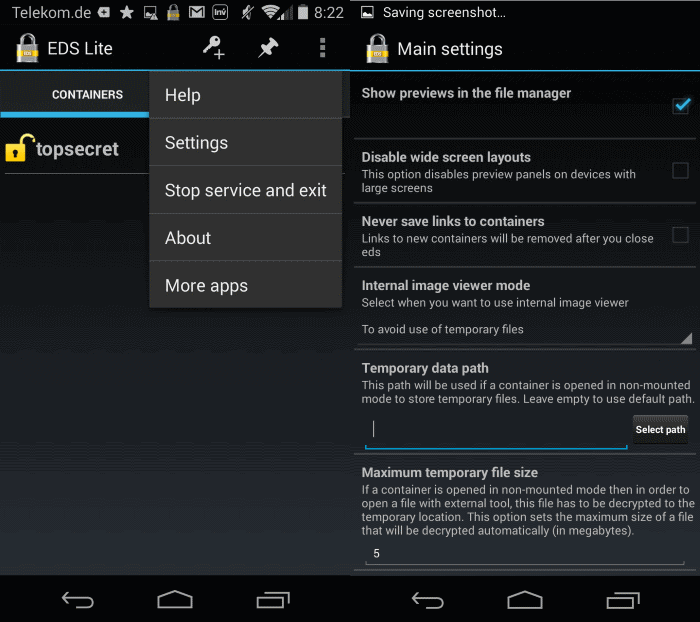
EDS Lite
Encrypted Data Store (EDS) is an application for Android devices that is available as a free lite version and a paid version. The encryption software supports TrueCrypt container files which means that you can load them in the application on your Android device.
The Lite version is limited severely though:
- It only supports AES, Serpent and Twofish algorithms.
- No hidden container support.
- No keyfile support.
- No direct access to containers via network shares or directly from a PC.
- No media playback from within container files.
- No indexed search to find files or records.
- No container synchronization with Dropbox.
- No container mounting (requires root).
As you can see, quite a lot of limitations. If all you want to do is gain access to files stored in a TrueCrypt container, then the free version may be sufficient for that provided that the container was created using one of the three supported algorithms and uses the FAT file system.
So how do you get the TrueCrypt container on the Android device? You can still use Dropbox for that or any other cloud synchronization service such as Google Drive, but the linking won’t be automatic in this case. If you run the full version of the app, you can automate the process further.
All you need to do is pick the container file in your Dropbox folder on Android to add it to the list of available containers. Supply the password to display its files and access them like any other file on the system.
Since Dropbox is not automatically syncing files to Android — only file information — you either need to download the container file manually to your device, or use an application such as Dropsync to automatically do so.
What I like about EDS Lite in particular is that it requires no network access. In fact, the only three permissions it requests are to modify or delete contents on USB storage, test access to protected storage, and prevent the device from sleeping.
The full version of EDS requires additional permissions though including full network access.
Additional information about the application and its feature set are available on the author’s homepage.
Closing Words
If you want to access TrueCrypt containers on your Android device, then EDS is the application to install for that. It is easy enough to setup and use, even though I wish it would offer better file management capabilities (especially copying files to a container).
The free version is somewhat limited, and if have encrypted a container using a non-supported algorithm, require key file support, direct access to containers on network shares, or Dropbox integration, then you may want to consider purchasing the full version of the application instead.
Источник
TrueCrypt Compatible Encryption on Android with EDS
- Application: EDS Lite
- Developer: Sovworks
- Current version: 1.1.1.26 / 1.3.2.90
- Price: Free / $5,40
When it comes to securing your data, TrueCrypt is popular choice for those who want to create encrypted storage to save sensitive files. This powerful open-source encryption software supports most of the desktop operation systems; alas it lacks support for mobile platforms. Android application called Encrypted Data Storage or simply EDS will give you access to the encrypted data on your Android phone or tablet.
Encrypted Data Storage Screenshot
What is Encrypted Data Storage?
EDS is an Android app that will store your files in the secure container encrypted using AES-256 algorithm. The application uses file format that is compatible with TrueCrypt, so you can open the container created on your Android device with your desktop computer and vice versa.
Encrypted Data Storage comes in two versions: free EDS Lite that supports all general data protection functions, and a paid version, called EDS that features many advanced features.
Features of the Lite version
EDS Lite allows you to create encrypted storage files, open them and work in so-called “normal” mode. In “normal” mode EDS Lite will open encrypted container, but it won’t provide “on-the-fly” encryption. You’ll have to decrypt files to a temporary location on your device to open them in external application. This is a less secure approach, than TrueCrypt’s “mounted” mode, when you can work directly with encrypted files in any application. You have to remember that while container’s encryption is strong and cannot be easily compromised, a full copy of a document will be created outside the container. This file if it has not been securely wiped could be recovered and compromised.
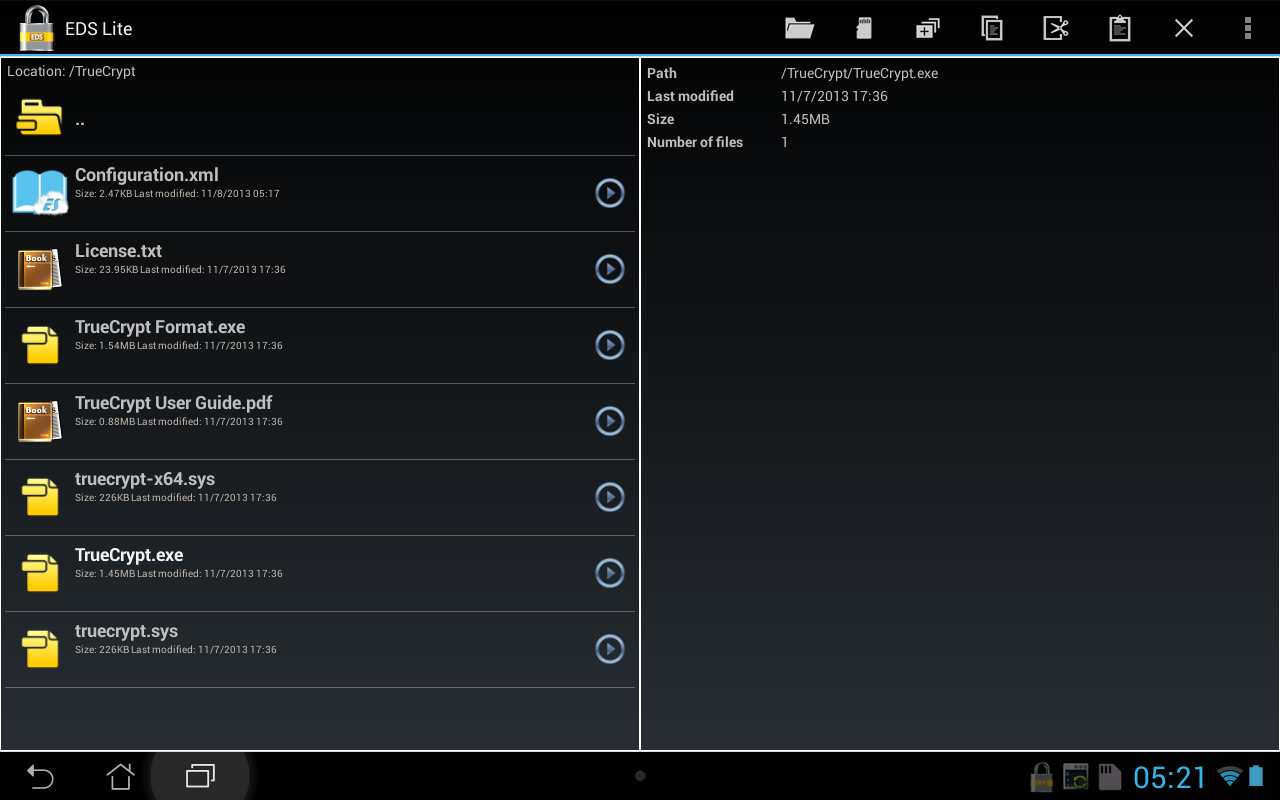
Although EDS Lite cannot mount containers as a system-wide folder it does have an integrated file manager to browse content of a storage files.
Lite version has limited support for container files created with TrueCrypt. It will only open a file that has been encrypted with the following settings:
- Encryption Algorithm: AES
- Hash Algorithm: SHA-512 (note that TrueCrypt uses RIPEMD-160 hash algorithm by default)
- Filesystem: FAT
Encrypted Data Storage Screenshot
Benefits of the Pro version
Though EDS Lite is a powerful application there are even more improvements and additions in Pro version including:
- Support for a wide range of encryption and hash algorithms.
- Support for NTFS, EXT2, EXT3 and EXT4 file systems.
- You can create and access hidden volumes that are created within another volume.
- Containers can be protected not only with password but also using keyfiles.
- Support for “mounted” mode with “on-the-fly” encryption. However this mode requires root access on your device.
- You can synchronize your container files using Dropbox.
Competition
There are two main alternatives to Encrypted Data Storage:
- Cryptonite – open-source application that brings EncFS and TrueCrypt support to Android. Cryptonite is a powerful application but it isn’t very user-friendly at this moment and is intended for experienced Android users only. Some of the application’s features require root access. TrueCrypt volumes can be mounted using command-line only.
- LUKS Manager – another app that provides on-the-fly encryption but it is not cross-compatible with TrueCrypt. LUKS Manager requires root access and will not work on non-rooted devices.
Источник