- OpSecX
- Online Security Education Platform
- Android Security Tools Expert – ATX
- Modules
- Introduction to ATX Course
- Apktool
- Dex2Jar, JD-GUI and Baksmali
- Androguard
- AndroBugs Framework
- Drozer
- Xposed Framework
- Frida
- Android security tools expert atx
- About
- OpSecX
- Online Security Education Platform
- Android Security Tools Expert – ATX
- Description
- What are the requirements?
- What am I going to get from this course?
- OpSecX Course Certificate
- Curriculum
- Reviews
- Android security tools expert atx
OpSecX
Online Security Education Platform
Android Security Tools Expert – ATX
This is a brand new course that covers the most commonly used android security assessment tools. Android Security assessment can be done with great ease if you have good expertise in the right tools. This course includes 12 different tools in over 30 videos. The course covers the features of tools like apktool, androguard, androbugs, dex2jar, baksmali, JD-GUI, drozer, qark, frida, xposed, appmon and mobsf. At the end of the course you will be proficient at using these tools in your day to day android application security assessments.
Modules
Introduction to ATX Course
Introduction to Android Security Tools Expert Course
Apktool
Introduction to Apktool
Apktool rebuilding APK
Dex2Jar, JD-GUI and Baksmali
Dex2Jar and JD-GUI
Androguard
Introduction to Androguard
Other Androguard Features
AndroBugs Framework
Introduction to AndroBugs Framework
Scanning APK with QARK
Scanning Source Code with QARK
Drozer
Introduction to Drozer
Android Application Security Assessment with Drozer
Identifying Attack Surface with Drozer
Drozer Infrastructure Mode
Xposed Framework
Introduction to Xposed Framework
Making an Xposed Module
Instrumenting Apps with Xposed
Frida
Introduction to Frida
Frida Python Binding
Bypassing Passcode with Frida Instrumentation
Источник
Android security tools expert atx
Mobile Security Framework (MobSF)
Version: v3.4 beta
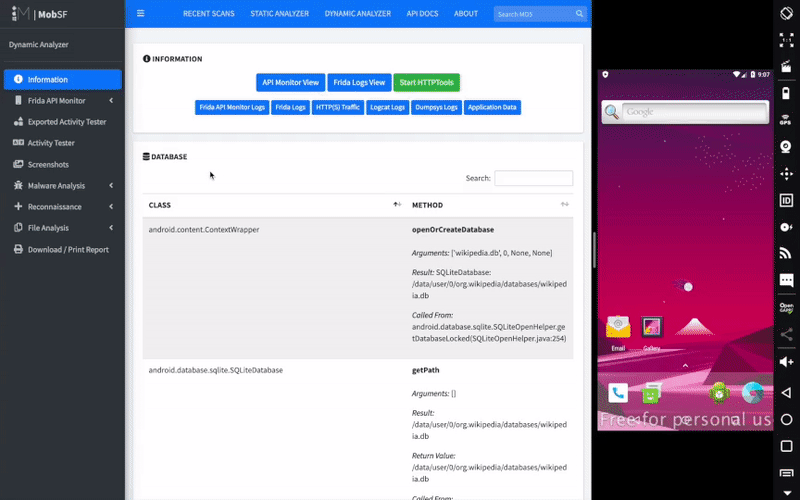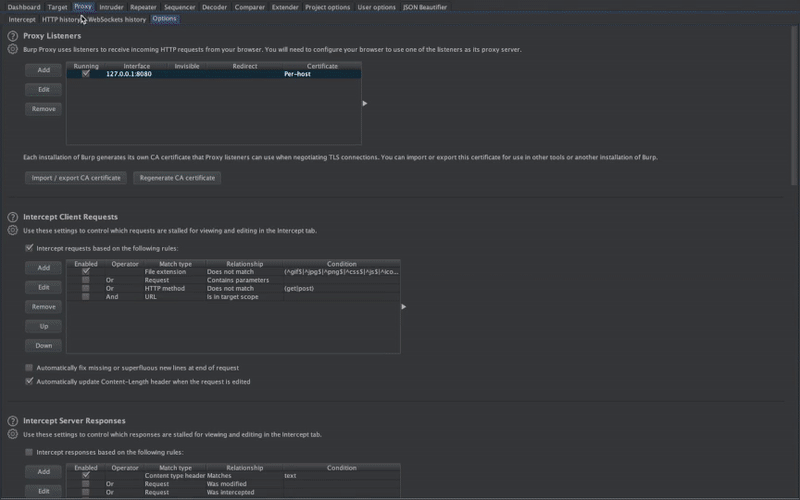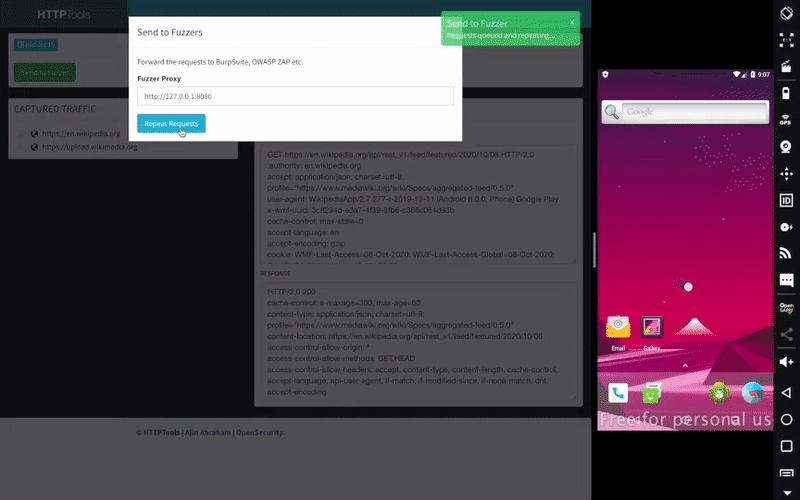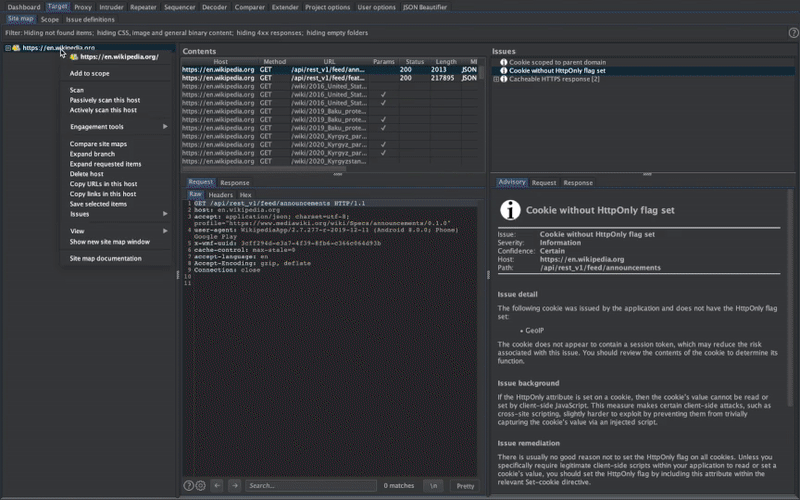
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis. MobSF support mobile app binaries (APK, XAPK, IPA & APPX) along with zipped source code and provides REST APIs for seamless integration with your CI/CD or DevSecOps pipeline.The Dynamic Analyzer helps you to perform runtime security assessment and interactive instrumented testing.
Made with 







MobSF is also bundled with Android Tamer, BlackArch and Pentoo.
If you liked MobSF and find it useful, please consider donating.
It’s easy to build open source, try maintaining a project once. Long live open source!

- Try MobSF Static Analyzer Online:
- MobSF in CI/CD: mobsfscan
- Conference Presentations: Slides & Videos
- MobSF Online Course: OpSecX MAS
- What’s New: See Changelog
e-Learning Courses & Certifications
- Free Support: Free limited support, questions, help and discussions, join our Slack channel
- Enterprise Support: Priority feature requests, live support & onsite training, see
Contribution, Feature Requests & Bugs
- Read CONTRIBUTING.md before opening bugs, feature requests and pull request.
- For Project updates and announcements, follow @ajinabraham or @OpenSecurity_IN.
- Github Issues are only for tracking bugs and feature requests. Do not post support or help queries there. We have a slack channel for that.
Static Analysis — Android
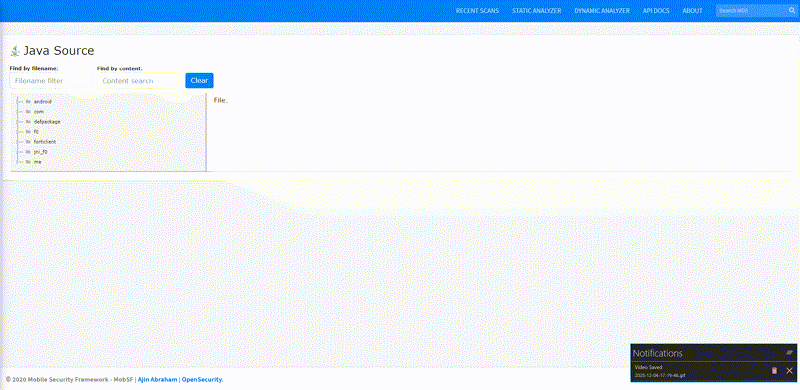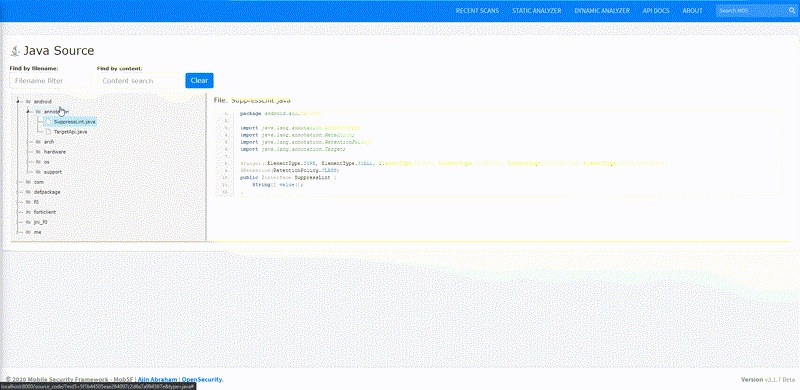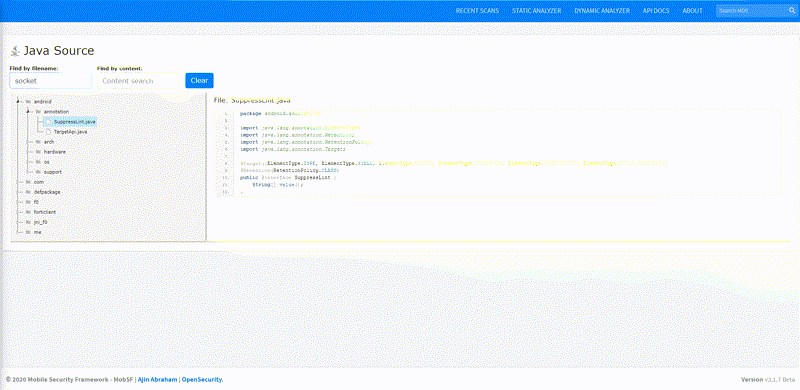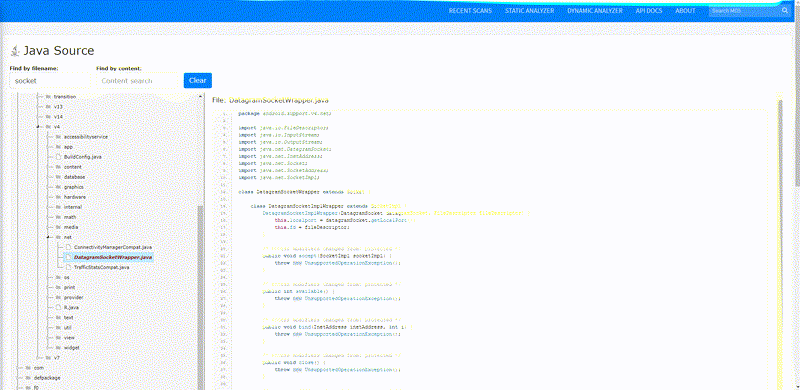
Static Analysis — Android Source Tree-view
Static Analysis — iOS
Dynamic Analysis — Android APK
- Amrutha VC — For the new MobSF logo
- Dominik Schlecht — For the awesome work on adding Windows Phone App Static Analysis to MobSF
- Esteban — Better Android Manifest Analysis and Static Analysis Improvement.
- Matan Dobrushin — For adding Android ARM Emulator support to MobSF — Special thanks goes for cuckoo-droid
- Shuxin — Android Binary Analysis
- Abhinav Saxena — (@xandfury) — For Travis CI and Logging integration
Netguru (@karolpiateknet, @mtbrzeski) — For iOS Swift support, Rule contributions and SAST refactoring.
- Maxime Fawe — (@Arenash13) — For Matching Strategy implementation of SAST pattern matching algorithms.
- Abhinav Sejpal (@Abhinav_Sejpal) — For poking me with bugs, feature requests, and UI & UX suggestions
- Anant Srivastava (@anantshri) — For Activity Tester Idea
- Anto Joseph (@antojoseph) — For the help with SuperSU
- Bharadwaj Machiraju (@tunnelshade) — For writing pyWebProxy from scratch
- Rahul (@c0dist) — Kali Support
- MindMac — For writing Android Blue Pill
- Oscar Alfonso Diaz — (@OscarAkaElvis) — For Dockerfile contributions
- Thomas Abraham — For JS Hacks on UI
- Tim Brown (@timb_machine) — For the iOS Binary Analysis Ruleset
- Shanil Prasad (@Rajuraju14) — For improving iOS ATS Analysis
About
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
Источник
OpSecX
Online Security Education Platform
Android Security Tools Expert – ATX
This is a brand new course that covers the most commonly used android security assessment tools. Android Security assessment can be done with great ease if you have good expertise in the right tools. This course includes 12 different tools in over 30 videos. The course covers the features of tools like apktool, androguard, androbugs, dex2jar, baksmali, JD-GUI, drozer, qark, frida, xposed, appmon and mobsf. At the end of the course you will be proficient at using these tools in your day to day android application security assessments.
Description
Android Security Tools Expert is a brand new android application security course from OpSecX.
This course covers the most commonly used open source android security assessment tools. Android Security assessment can be done with great ease if you have good expertise in the right tools. This course includes 12 different tools in over 30 lectures. The course covers the features of tools like apktool, androguard, androbugs, dex2jar, baksmali, JD-GUI, drozer, qark, frida, xposed, appmon and mobsf in detail. This course is best suited for android security engineers, aspiring security students, android developers, security engineers, and security consultants. We have great open source tools available at our disposal, but some are not documented well, or it’s difficult to follow. This course is designed to act as a detailed how to for these tools and helps you to make the best use of these. We cover the most important and useful features of these security tools that you can benefit in your day to day android application security assessments.
What are the requirements?
- Basic Idea of how android applications work.
- Comfortable with working on command line interfaces
- Basic understanding of Android Application Security
What am I going to get from this course?
- Over 30 lectures covering 12 android security tools
- In depth explanation of the tools and their features
- Practical demonstrations with detailed explanations
- Learn how to use security tools to perform security assessment of android applications.
OpSecX Course Certificate
Upon successful completion of the course, you will be given a Certificate of Appreciation and the certificate can be verified from OpSecX online.
Curriculum
Section 1: Introduction to the Course
1. Introduction
Section 2: Apktool
2. Introduction to Apktool
3. Smali 101
4. Apktool rebuilding APK
Section 3: Dex2Jar, JD-GUI and Baksmali
5. Dex2Jar and JD-GUI
6. Baksamli
Section 4: Androguard
7. Introduction to Androguard
8. Other Androguard Features
Section 5: AndroBugs Framework
9. Introduction to AndroBugs Framework
Section 6: QARK
10. Scanning APK wth QARK
11. Scanning Source Code with QARK
Section 7: Drozer
12. Introduction to Drozer
13. Android Application Security Assessment with Drozer
14. Identifying Attack Surface with Drozer
15. Drozer Infrastructure Mode
Section 8: Xposed Framework
16. Introduction to Xposed Framework
17. Making an Xposed Module
18. Instrumenting Apps with Xposed
Section 9: Frida
19. Introduction to Frida
20. Frida Tools
21. Frida CLI
22. Frida Python Binding
23. Bypassing Passcode with Frida Instrumentation
24. Bypassing RootBeer with Frida
Section 10: Appmon
25. Getting started with AppMon
26. Appmon Sniffer
27. Appmon Intruder & Tracer
Section 11: Mobile Security Framework – MobSF
28. Mobile Security Framework Static Analysis
29. Mobile Security Framework Dynamic Analysis
30. Mobile Security Framework Web API Fuzzing
Reviews
There are no reviews yet.
Only logged in customers who have purchased this product may leave a review.
Источник
Android security tools expert atx
Copy raw contents
Mobile Security Framework (MobSF)
Version: v3.4 beta
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis. MobSF support mobile app binaries (APK, XAPK, IPA & APPX) along with zipped source code and provides REST APIs for seamless integration with your CI/CD or DevSecOps pipeline.The Dynamic Analyzer helps you to perform runtime security assessment and interactive instrumented testing.
Made with 







MobSF is also bundled with Android Tamer, BlackArch and Pentoo.
If you liked MobSF and find it useful, please consider donating.
It’s easy to build open source, try maintaining a project once. Long live open source!

- Try MobSF Static Analyzer Online:
- MobSF in CI/CD: mobsfscan
- Conference Presentations: Slides & Videos
- MobSF Online Course: OpSecX MAS
- What’s New: See Changelog
e-Learning Courses & Certifications
- Free Support: Free limited support, questions, help and discussions, join our Slack channel
- Enterprise Support: Priority feature requests, live support & onsite training, see
Contribution, Feature Requests & Bugs
- Read CONTRIBUTING.md before opening bugs, feature requests and pull request.
- For Project updates and announcements, follow @ajinabraham or @OpenSecurity_IN.
- Github Issues are only for tracking bugs and feature requests. Do not post support or help queries there. We have a slack channel for that.
Static Analysis — Android
Static Analysis — Android Source Tree-view
Static Analysis — iOS
Dynamic Analysis — Android APK
- Amrutha VC — For the new MobSF logo
- Dominik Schlecht — For the awesome work on adding Windows Phone App Static Analysis to MobSF
- Esteban — Better Android Manifest Analysis and Static Analysis Improvement.
- Matan Dobrushin — For adding Android ARM Emulator support to MobSF — Special thanks goes for cuckoo-droid
- Shuxin — Android Binary Analysis
- Abhinav Saxena — (@xandfury) — For Travis CI and Logging integration
Netguru (@karolpiateknet, @mtbrzeski) — For iOS Swift support, Rule contributions and SAST refactoring.
- Maxime Fawe — (@Arenash13) — For Matching Strategy implementation of SAST pattern matching algorithms.
- Abhinav Sejpal (@Abhinav_Sejpal) — For poking me with bugs, feature requests, and UI & UX suggestions
- Anant Srivastava (@anantshri) — For Activity Tester Idea
- Anto Joseph (@antojoseph) — For the help with SuperSU
- Bharadwaj Machiraju (@tunnelshade) — For writing pyWebProxy from scratch
- Rahul (@c0dist) — Kali Support
- MindMac — For writing Android Blue Pill
- Oscar Alfonso Diaz — (@OscarAkaElvis) — For Dockerfile contributions
- Thomas Abraham — For JS Hacks on UI
- Tim Brown (@timb_machine) — For the iOS Binary Analysis Ruleset
- Shanil Prasad (@Rajuraju14) — For improving iOS ATS Analysis
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник








 Netguru (@karolpiateknet, @mtbrzeski) — For iOS Swift support, Rule contributions and SAST refactoring.
Netguru (@karolpiateknet, @mtbrzeski) — For iOS Swift support, Rule contributions and SAST refactoring.



