- Опасная уязвимость в Android ставит под угрозу миллионы пользователей
- ‘SAW’-ing through the UI: Android overlay malware and the System Alert Window permission explained
- What is Android screen overlay and what’s it for?
- The System Alert Window Android App Permission
- Mobile App Vetting for Supply Chain
- Potential abuses of the System Alert Window permission
- Android overlay attacks and ransomware
- How can I protect myself against abuse of the System Alert Window permission?
- Android system alert windows
- About
- Android system alert windows
- About
- SYSTEM_ALERT_WINDOW – как получить это разрешение автоматически на Android 6.0 и targetSdkVersion 23
Опасная уязвимость в Android ставит под угрозу миллионы пользователей
Проблема связана с функцией SYSTEM_ALERT_WINDOW, позволяющей выводить срочные сообщения поверх окон других приложений.
Эксперты компании CheckPoint обнаружили серьезную уязвимость в ОС Android, которая облегчает задачу приложениям-вымогателям и банковским троянам, помогая создавать фишинговые страницы и окна с требованием выкупа.
Проблема связана с системой разрешений Android, в частности, с функцией SYSTEM_ALERT_WINDOW, позволяющей выводить срочные сообщения поверх окон других приложений. Первоначально данное разрешение появилось в версии Android 6.0.0 и пользователь должен был сам решать, каким приложениям позволено перекрывать экран своими сообщениями, но уже в Android 6.0.1 это право было автоматически присвоено всем приложениям, загружаемым из Google Play Store.
Данный функционал нередко эксплуатируется злоумышленниками в рамках фишинговых атак или для инфицирования устройств вредоносным ПО. Согласно информации CheckPoint, разрешение SYSTEM_ALERT_WINDOW используют 74% вымогательского ПО, 57% рекламных приложений и 14% банковских троянов.
Все загружаемые в Google Play Store приложения проходят проверку Google Bouncer, но, как показывает практика, система не так эффективна. К примеру, в апреле специалисты обнаружили в интернет-каталоге три приложения, содержавших модифицированную версию банковского трояна BankBot, способную обходить проверки Google Bouncer. Приложения эксплуатировали разрешение SYSTEM_ALERT_WINDOW для отображения фальшивых страниц авторизации банковских приложений с целью хищения паролей жертвы.
Исследователи проинформировали Google об уязвимости, однако в компании заявили, что проблема будет исправлена не раньше появления версии Android O, запланированной к выходу в третьем квартале нынешнего года. В новой версии будет представлено разрешение TYPE_APPLICATION_OVERLAY, которое запретит окнам приложений перекрывать системные окна и позволит пользователям получить доступ к настройкам для блокировки уведомлений приложений.
Источник
‘SAW’-ing through the UI: Android overlay malware and the System Alert Window permission explained
Over the past month, we’ve talked about a troublesome Android app permission called `SYSTEM_ALERT_WINDOW` a couple of times in our weekly #MobSec5 news digest — subscribe here. This week, researchers from University of California Santa Barbara and Georgia Institute of Technology released details about “Cloak and Dagger” a collection of attacks that take advantage of this permission. Customers 1 have asked me about `SYSTEM_ALERT_WINDOW` (abbreviated SAW for the purposes of my oh-so-witty headline) a nd how malware might abuse the Android overlay view to steal log-in credentials and the like from Android users. I wanted to explain the Android app permission in plain language, how it might be abused, and finally what people can do to mitigate the risk.
What is Android screen overlay and what’s it for?
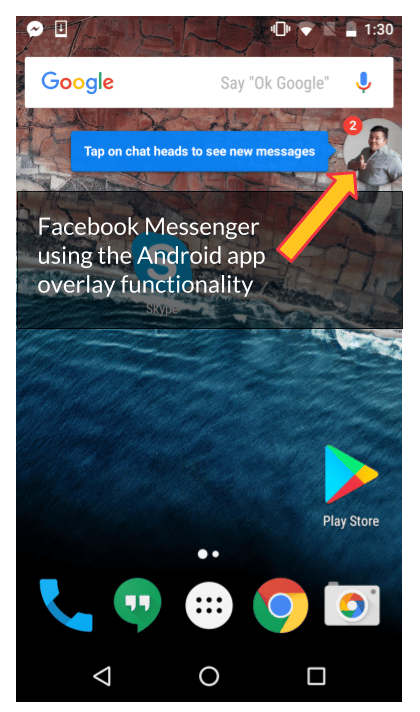
A screen overlay in Android, also referred to as “Draw On Top”, allows an app to display content over another app. The Android app permission SYSTEM_ALERT_WINDOW makes this possible. If you’ve ever used an app like Facebook Messenger or Lastpass, you’ve experienced screen overlay in action. Basically, the permission allows a developer to display content on the screen of your Android device after some trigger event.
For example, you may have seen the cute notification bubble in Facebook Messenger (also called a “chat head” — see the screenshot above) that includes a contact’s photo. If you tap the chat head, it leads to a pop-out version of the Messenger app. Have you noticed that you never gave Facebook Messenger permission to display that bubble?
The System Alert Window Android App Permission
Android Marshmallow (specifically Android 6 API Level 23), introduced the requesting of permissions at runtime. If an app wanted to access your calendar, camera, and other functionalities, the user needed to grant the permission. Unfortunately, that’s not always true of SYSTEM_ALERT_WINDOW . If a developer targets a lower API level like API level 22 in Android 5 (Lollipop), the Google Play store grants the permission without a runtime prompt. If your device uses Android 6.0.1 or higher and you install an app requesting the SYSTEM_ALERT_WINDOW permission, it’s granted by default! What this all means is that the only time a user will manually grant the “Draw Over App” permission is if they run Android 6.0.0 and the app is built for API level 23 or above, or when side-loading an app from a third party Android app store (something we usually recommend against for security’s sake).
This blows my mind, because if someone were so inclined, they could potentially compromise a user’s phone with the SYSTEM_ALERT_WINDOW permission using Android overlay malware. Overlay malware is not a new concept, and the Google Play Store has published a number of malicious apps that abused the Android screen overlay. The apps typically pose as something harmless. In one example of Android overlay malware discovered by ESET, a malicious flashlight app actually turned out to be banking trojan malware.
Mobile App Vetting for Supply Chain
Potential abuses of the System Alert Window permission
Generally, these attacks play out something like this
- A user downloads the malicious app
- A trigger activates the use of the SYSTEM_ALERT_WINDOW permission to display content over the top of the UI
- The screen asks the user for information, such as credentials, and the user divulges that information to make the screen overlay go away
The SYSTEM_ALERT_WINDOW permission makes a number of attacks possible, but overlay attacks seem to be the most prominent at this time. Once a malicious app has been installed on your device, the app will wait for the user to launch a target app. When the target app is launched, the malicious app produces an overlay to trick users into entering their credentials into a phony login screen. The user’s credentials are then sent to the attacker’s server.
The animation below demonstrates what an attack might look like on a victim’s phone. You can find the sample malware I used for the demonstration on Github: https://github.com/geeksonsecurity/android-overlay-malware-example.
Here’s what you’re seeing in the video:
- The user launches the Skype app
- The phony login screen is overlaid on top of the authentic login page
- After information is entered into the malicious screen, you see the actual Skype login page
Android overlay attacks and ransomware
With ransomware concerns rising in the wake of the WannaCry attack earlier this month, there have been some suggestions that overlay screens could be used to launch a ransomware attack on Android devices. This is pure speculation, but malware could potentially display an overlay screen demanding credit card information to make it go away. It’s possible some users will fall for the ploy when in reality their files weren’t encrypted or inaccessible and they could have exited the app via other means.
With that said, the Cloak and Dagger researchers have published a video demonstration of a clickjacking attack that might make such an attack possible. An overlay screen is displayed on top of the UI that includes “holes” that a user can be persuaded to click. Essentially, the user is “clicking through” the overlay screen to certain areas of a UI behind it. The clickjacking technique leverages both the SYSTEM_ALERT_WINDOW and BIND_ACCESSIBILITY_SERVICE . Such a technique could be repeated multiple times resulting in the user unknowingly clicking the settings interface to grant an app enough permissions culminating in the complete takeover of an Android device.
Also of concern is that nothing currently indicates to an app that another app is overlaying its UI. And this may be possible via apps published on the Google Play store, not a third party app store. While it might be tempting to call this a bug that can be patched, it seems like a fundamental flaw in Android’s permissions design.
How can I protect myself against abuse of the System Alert Window permission?
According to the Cloak and Dagger paper, an estimated 10 percent of apps on the Google Play store use the SYSTEM_ALERT_WINDOW permission. While an administrator might tempted to prohibit users from installing apps that request SYSTEM_ALERT_WINDOW , doing so would likely result in a staff revolt.
Some of the most popular apps on the store call on the SYSTEM_ALERT_WINDOW — not just malware. Users can see what apps have the permission using the instructions in the table below (instructions may not apply to all devices).
| Version | How to review apps with Draw Over Other Apps permission |
|---|---|
| Android 7 | Settings > Apps > “Gear symbol” > Special Access > Draw over other apps |
| Android 6 | Settings > Apps > “Gear symbol” > Draw over other apps |
| Android 5 | Settings > Apps > Select app and look for “draw over other apps” |
In addition, before downloading an app, you can check to see if the app uses the `SYSTEM_ALERT_WINDOW` permission by reading the “Permission Details” on the app’s page in the Google Play Store and looking for a “draw over other apps” bullet.
What makes these `SYSTEM_ALERT_WINDOW`-based attacks so scary is Google’s app vetting process has failed to identify a few of these apps before they’re published on the public app store. Google has, however, started tackling this issue in Android O. There are reports that the beta version of Android O includes a mechanism that will notify users that app overlay is taking place. While this is a step in the right direction, Google might need to consider treating the overlay permission in the same way it treats camera permissions. Still, users stuck on older versions of Android could still fall victim.
1 Special thanks to Dan Dumitrescu, security specialist at a financial institution.
What to read next:
Mobile banking Trojans: What can financial institutions do?
A seeming resurgence in mobile banking Trojans has financial institutions asking questions. NowSecure CTO David Weinstein has answers.
Источник
Android system alert windows
A flutter plugin to show Truecaller like overlay window, over all other apps along with callback events. Android Go or Android 11 & above, this plugin shows notification bubble, in other android versions, it shows an overlay window.
1. Clip of example app and 2. Working of button click in the background

Android 10 & below, Android GO (API 27)
Uses ‘draw on top’ permission and displays it as a overlay window
Android 11 & above
User has to allow ‘All conversations can bubble’ in the notification settings of the app. Uses Android Bubble APIs to show the overlay window inside a notification bubble.
Android GO (API 29)
User has to manually enable bubbles from the developer options. Uses Android Bubble APIs to show the overlay window inside a notification bubble.
Displays as a notification in the notification center [Help Needed]
Request overlay permission
Show the overlay
Register for onClick events (button click)
Close the overlay
Use this snippet, if you want the callbacks on your main thread, instead of handling them in an isolate (like mentioned above)
Create an isolate_manager.dart
While initializing system alert window in your code
Now the callBackFunction should looks like
About
A flutter plugin to show Truecaller like overlay window, over all other apps along with callback events. In Android Go or Android 11 & above, this plugin shows notification bubble, in other android versions, it shows an overlay window.
Источник
Android system alert windows
Example project showing use of SYSTEM_ALERT_WINDOW permission on Android 23+, with back button interception.
. IMPORTANT UPDATE. [2019-05-08] We all SAW it coming (pun intended), but the Android team have finally given us an idea of where the out-of-app UI interaction that system-alert-window enabled is going. Confirmed at Google IO 2019: it’s going away. Part of the flakily-recorded «Whats New In Android» talk mentions it here.
- On first launch, the app will check that it has permission to draw over other apps, and will show the user the corresponding prompt if not.
- Once permission is granted, opening the app starts a service that inflates a layout and adds it to the screen as an overlay.
Note: This screenshot shows the example app drawing over the top of another running app: motorsport-circuits. So don’t expect a map to appear when you run the example code! You just get the green box and bugdroid.
If any other app is running when the the app launches, they will lose focus, but onPause will not be called — the app behaves as a system alert, as the title suggests.
It’s deliberately translucent and not full screen so that other apps can be seen running in the background, but you can make the app run full window by modifying the layout XML, and making the background colour opaque.
KeyEvent interception is shown on the back button; if you try to press the back button whilst the alert is shown, it’ll be intecepted and a message shown in the logs.
Touches are intercepted whilst the alert/app is shown, even though other apps might be visible in the background they can’t be interacted with.
Touch the View itself to close and kill the Service.
About
Example project showing use of SYSTEM_ALERT_WINDOW permission on Android 23+, with back button interception.
Источник
SYSTEM_ALERT_WINDOW – как получить это разрешение автоматически на Android 6.0 и targetSdkVersion 23
Facebook, Evernote, Pocket – все приложения получают это разрешение на Android 6.0 автоматически, даже если они нацелены на 23 ( targetSdkVersion=23 ).
Было много документации относительно новой модели разрешения Marshmallow. Один из них: SYSTEM_ALERT_WINDOW был «продвинут» до класса «выше опасных», что требует специального вмешательства пользователя, чтобы приложения были предоставлены им. Если приложение имеет targetSdkVersion 22 или ниже, приложение получает это разрешение автоматически (если требуется в манифесте).
Тем не менее, я заметил некоторые приложения, которые получают это разрешение, не требуя отправки пользователя на специальную страницу настроек Draw over other apps разрешениями Draw over other apps . Я видел Facebook, Evernote, Pocket – и, возможно, их больше.
Кто-нибудь знает, как приложение может получить это разрешение без участия пользователя в Settings -> Apps -> Draw over other apps ?
Это новое поведение, введенное в Marshmallow 6.0.1 .
Каждое приложение, запрашивающее разрешения SYSTEM_ALERT_WINDOW и устанавливаемое через Play Store (версия 6.0.5 или выше, требуется), автоматически предоставит разрешение.
Если вместо этого приложение загружается набок, разрешение автоматически не предоставляется. Вы можете попробовать загрузить и установить Evernote APK с сайта apkmirror.com . Как вы можете видеть, вам нужно вручную предоставить разрешение в Settings -> Apps -> Draw over other apps .
Это коммиты [1] [2], которые позволяют Play Store автоматически предоставлять разрешение SYSTEM_ALERT_WINDOW .
Yeh После того, как Marshmallow выйдет, Android сделает уровень безопасности более палкой, но для
Вы можете показать плавающее действие и все, что вы можете заставить пользователя дать разрешение на него. Следуя кодам в вашем методе Oncreate () Поместите этот код после setContentView
Действие ACTION_MANAGE_OVERLAY_PERMISSION непосредственно запускает экран разрешения «Нарисуйся по другим приложениям».
Привет, мой выше код работает 100% Исправить
Но я только обнаружил, что многие ребята все еще ищут, как можно разрешить ACTION_MANAGE_OVERLAY_PERMISSION навсегда, как если бы пользователь разрешил разрешение. После этого не спрашивайте его каждый раз, когда он открывает приложение, так что слушайте решение для вас. 1) Проверьте, есть ли устройство api 23+
2) если 23+ api, то проверьте, разрешает ли пользователь или нет
3) если разрешил один раз не доставить его до Settings.ACTION_MANAGE_OVERLAY_PERMISSION & if еще не разрешил, то попросите проверить разрешение во время выполнения
Теперь onActivityResult код в onActivityResult
Теперь, наконец, код метода checkPermission
И не забудьте объявить эту общедоступную переменную в своем классе
Если приложение предназначено для API 22 или ниже, то Play Store предоставит разрешения SYSTEM_ALERT_WINDOW и другие, когда пользователь нажмет на установку (показывая предупреждение), даже если его устройство Android 6.0. В противном случае, если приложение предназначено для API 23 или выше, так что Разрешение будет запрашиваться во время выполнения.
Источник