Android telegram rat github
Windows Remote Administration Tool via Telegram (now in Python 3.7!) | Originally created by Ritiek
Why another one?
The current Remote Administration Tools in the market face 2 major problems:
- Lack of encryption.
- Require port forwarding in order to control from hundreds of miles.
This RAT overcomes both these issues by using the Telegram bot API.
- Fully encrypted. The data being exchanged cannot be spied upon using MITM tools.
- Telegram messenger app provides a simple way to communicate to the target without configuring port forward before hand on the target.
- Keylogger with window title log included
- Get target PC’s Windows version, processor and more
- Get target PC’s IP address information and approximate location on map
- Delete, Move files
- Show current directory
- Change current directory
- List current or specified directory
- Download any file from the target
- Upload local files to the target. Send your image, pdf, exe or anything as file to the Telegram bot
- Autostart playing a video in fullscreen and no controls for a youtube video on target
- Take Screenshots
- Execute any file
- Access to microphone
- Start HTTP Proxy Server
- Freeze target’s keyboard
- Schedule tasks to run at specified datetime
- Encode/Decode all local files
- Ping targets
- Update .exe — thanks LearnerZone
- Self-Destruct RAT
- Change wallpaper from file or url
- Execute cmd shell
- Take snapshots from the webcam (if attached)
- Execute arbitrary python 3.7 on the go
- Freeze target’s mouse
- [TODO] Browser (IE, Firefox, Chrome ) cookies retrieval
- [TODO] Password retrieval
- [TODO] Monitor web traffic (graphically?)
- [TODO] Bandwidth monitoring (stepping stone to web traffic monitoring) — started 28/10/2018
- [TODO] Fine-tuning scripting (i.e.: if app x is opened y is executed)
- [TODO] Capture clipboard (Text, Image)
- [TODO] Hide desktop icons
- [TODO] Audio compression
- [TODO] Name server lookup (/nslookup — #19)
- Chrome login/password retrieval
- Display ARP table
- Get active processes and services
- Shutdown/Reboot computer
- Display DNS Cache
& More coming soon!
- Clone this repository.
- Set up a new Telegram bot talking to the BotFather .
- Copy this token and replace it in the beginning of the script.
- Run compile.py
- Generates an executable binary
- To run the script: python RATAttack.py .
- Find your bot on telegram and send some command to the bot to test it.
- To restrict the bot so that it responds only to you, note down your chat_id from the console and replace it in the script and comment out the line return True . Don’t worry, you’ll know when you read the comments in the script.
- A folder named RATAttack will be created in your working directory containing keylogs.txt and any files you upload to the bot.
When using the below commands; use / as a prefix. For example: /pc_info .
You can copy the above to update your command list via BotFather so you don’t have to type them manually.
- Run compile.py . You can also pass —icon=
to use a custom icon. If you want to use UPX for compression, you can add —upx-dir [upx-3.95-win64 | upx-3.96-win32] , depending on your architecture. You can skip this last option if you have UPX in your PATH environment variable.
- You can also modify the name of hidden .exe file and location and name of the folder where the hidden .exe will hide itself. To do this; modify compiled_name and hide_folder respectively.
- Assign your known chat ids to beginning of RATAttack.py
- This project is still in very early stages, so you can expect some bugs. Please feel free to report them! Even better, send a pull request 🙂
- Any new features and ideas are most welcome! Please do submit feature requests by creating Issues
- Branch protection is enabled on master . You must work in an alternate branch (e.g. dev ) and make a PR. This is to ensure that master has a working and approved version of RvT.
A markdown file with credits: Credit file
People with PRs:
This tool is supposed to be used only on authorized systems. Any unauthorized use of this tool without explicit permission is illegal.
Источник
Android telegram rat github
Table of Contents
Windows file Dropper and (file Manager) using Telegram. this program will allow yout to download and upload files to any windows computer without port forwarding useing telegram and also is Fully encrypted means (The data being exchanged cannot be spied upon using MITM tools).
- upload File
- download File
- excute .exe remotly
- navigate File System
- Great Perfomance (using Async/Await)
- autoRun (Using schtasks)
- Fud (Fully Undetectable)
- multi client (program will genrate client id at first connection)
- [Todo] automatic file Graber
- [Todo] Spreader (re Infect Flash drives)
go to program Directory /source.
- Change const.dart file line 6 with your Own telegram bot api.
- Compile using [ dart2native bin/drop_it.dart -o bin/myApp.exe].
- -*** Note change your Const.dart programid to your compiled program Name.
- use this command to hide console while app is running [editbin.exe /subsystem:windows
.exe]
editbin.exe is apart of the microsoft Visual studio 2019
About
Fully Undetectable telegram Rat dropper
Topics
Resources
Releases
Packages 0
Languages
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
Android telegram rat github
⬆️ ⬆️ ⬆️ This is link to YouTube video ⬆️ ⬆️ ⬆️
It’s Windows Remote Administration Tool who work via Telegram Bot.
How start using it?
- First step you need to create your telegram bot:
- open telegram
- go to @BotFather
- choose name and username of your bot
- @BotFaher send you token, you need to copy and save it
- go to your bot and type /start
- Second step you need to know your ChatId:
- in telegram go to @userinfobot and type /start
- he sent you your ChatId
- copy and save it id!
- Next you need to edit bot code:
- open file RAT.py in any text editor
- edit variables bot_token and chat_id at the beginning code afret imports on previously saved data
- save all changes
- In last step you need to create application .exe
- open terminal or cmd and type: pip install pyinstaller
- open directory where is RAT.py and type: pyinstaller -w -F RAT.py
- in current directory where is RAT.py will be created several folders
- in folder dist will be your RAT.exe
- /screen — screenshot
- /info — info about user
- /location — location on a map
- /kill_process — kill the process (process.exe)
- /reboot — reboot pc
- /shutdown — shutdown pc
- /pwd — know current directory
- /passwords_chrome — chrome passwords
- /passwords_opera — opera passwords
- /cockies_chrome — chrome cockies
- /cockies_opera — opera cockies
- /get_discord — get token of Discord session
- /cmd command — execute command in CMD
- /open_url — open link
- /ls — all files and folders in directory
- /cd — move to folder
- /download — download file
- /rm_dir — delete folder
About
Windows Remote Administration Tool that works with Telegram Bot
Источник
Telegram-RAT
📄 Установка:
Для работоспособности скрипта установите Python 3.8 и следующие библиотеки
- pip3 install pytelegrambotapi
- pip3 install opencv-python
- pip3 install cryptography
- pip3 install comtypes
- pip3 install pywin32
- pip3 install pyaudio
- pip3 install pillow
- pip3 install pycaw
- Если есть ошибка с pyaudio, скачайте отсюда
- Перейдите в директорию с whl-файлом и впишите в консоль pip3 install pyaudio.x.x.x.whl
- Создаём бота в телеграме через @BotFather , после чего находим его API-Токен
Теперь вам нужно получить ваш Telegram-ID. Для этого перейдите к @my_id_bot и сохраните ваш идентификатор.
Теперь вставьте скопированный токен и айди в скрипт RAT.py
- Теперь нажмите CTRL + S , чтобы сохранить изменения.
- Чтобы скомпилировать скрипт, воспользуйтесь pyinstaller’ом ( pip install pyinstaller )
- Теперь откройте CMD в директории со скриптом и впишите pyinstaller —onefile —noconsole RAT.py и подождите.
- Скомпилированный .exe файл будет в находиться в папке dist . И при запуске будет отправлять вам сообщение об онлайне.
- Чтобы узнать список команд, используйте /help
Источник
Digital Forensics Tips&Tricks: Telegram IM-based RAT — Part I
Did you know that Telegram IM becomes more and more popular as a toolkit to make some illegal do’s?
There are a lot of hidden channels and bots with different illegal and piracy content. I can suggest you an article where some of these points are described deeply.
But my point of interest is using Telegram as Remote Access Toolkit (RAT).

I see a potentially big field for attackers in this for at least 2 reasons:
- Telegram is completely legal product and it’s agent doesn’t look suspicious for antivirus software
- There is a lot of information about «How To Use Telegram as RAT» with detailed instructions on Youtube and other Internet resources
So, anyone can download it from Github or somewhere else and try to use IM as RAT
And here are some video manuals:
Ok, now you see — it’s not so hard to download Telegram-based RAT and understand how to use it. Moreover — almost all of these projects use a Python code. So, anyone can compile a python code to .exe using tools like pyinstaller or kind of this.
On final you’ll get — BOOM! — an executable RAT tool, which is undetectable for antiviruses!
Cool, heh?
Here are some capabilities of mvrozanti/RAT-via-Telegram for instance:
An attacker can customize the RAT (change an icon, add a certificate etc), then compile and send it as a phishing email attachement. What’s next? Anything!
Search for files (even on a network drives), execute apps and scripts, upload and download documents, receive a keylogs, blah-blah — anything!
Of course — an attacker needs the infected workstation has Internet access. But I think it’s not a big deal for some reasons.
Ok, the main question is How To Detect a Telegram RAT had been used or it is using right now on the workstation?
1. Modern malwares mostly created for long-term exploitation of IT-infrastructure. So, try to find a persistance points. The common way is to check the autorun keys:
On this screenshot you see an application with Adobe icon but it has non-standard name and location — check it on Virustotal or related service if you found kind of this one.
By the way — this is the results of checking Telegram-based RAT executive file. As you see, just minor part of engines detected it as suspicious.
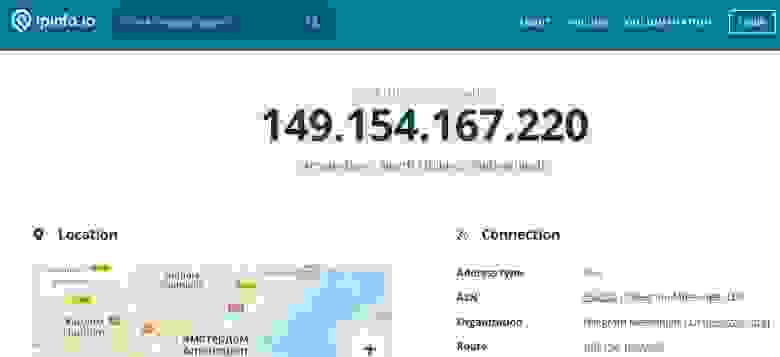
2. Since something strange was found in the autorun, the next obvious step is to check the process list. Well, here we’ve found this Adobe-like process with active network session:
Ok, let’s check this IP address… And — BOOM! — it’s a Telegram IP
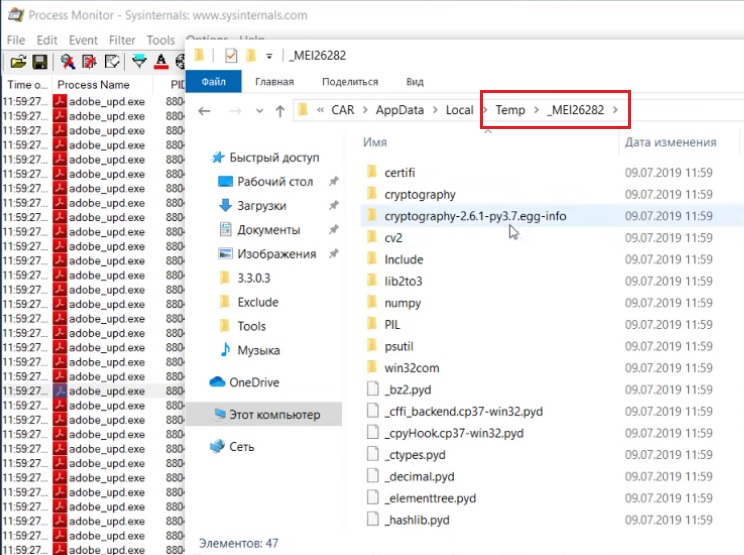
3. How to find out the behaviour of this process? Try to use Process Monitor!
To get a more comfortable view don’t forget to use filter by process & filesystem operations:
You can see a lot of different operations on files and folders and some filenames give us an important information about the process functions (win32clipboard.pyd).
Moreover, we noticed the active process creates a number of temporary python files — we can use this knowledge further, during the investigation process.
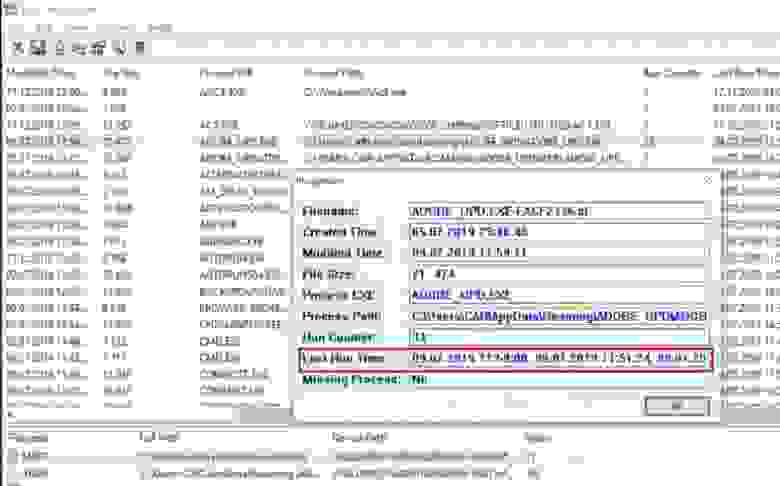
4. For instance, two ways to understand what date when RAT was started first time:
- Check the system prefetch list using WinPrefetchView
- Check the processes’ network usage statistics from SRUM using NetworkUsageView
Ok, now you have the exact date and may continue your investigation to understand where this file came from: check a browsers history, check whether the email attachments were opened and executed on this period etc
Thank you again for attention! I’ll be back soon with a new good stuff!
Источник