Android Security Testing: Setting up burp suite with Android VM/physical device.
Oct 5, 2020 · 6 min read
Setting up the Burp suite with an android device is simple but a little tricky.
There are several ways to set up this environment.
1. Setting up Burp suite with Android VM (Needs Genymotion with virtual box).
2. Setting up Burp suite with Android physical Device (Needs Rooted android device).
Setting up Burp suite with Android VM (Needs Genymotion with virtual box) or with Android physical device.
Follow the below-mentioned steps:
Prerequisite:
i. Burp suite.
ii. Genymotion (With virtual box.).
ii. Android device ( Rooted.).
iii. adb tools. Click here to download.
iv. Setting up proxy and Certificate in Android VM/device.
v. Frida installed in host PC and Frida server file to run Frida from the Android device. (python installed in the host machine.(PC/laptop))
Step 1: Certificate export: Open Burp Suite. Go to Proxy → Options → Proxy Listener → click on import/ export CA certificate. → At the export choose Certificate in DER format.(eg. cacert.der) → Click on next → select any file name having extension as .der → Click on next.
Step 2: Go to the folder where you saved the Burp CA certificate. → Change the extension from .der to .crt (eg. cacert.crt)→ and save it.
Step 3: Proxy setting in burp: Go to Proxy → Options → Proxy Listener → Click on add → Select specific address and then select IP of the device where burp is running or Simply select All interfaces (It will intercept traffic all the traffic going through your system.). → Enable this config.
ii. Genymotion (With virtual box.).
Step 1: Installing Genymotion: Download Genymotion (Please select with the virtual box) from Click here to download. → Register with Genymotion → Login → Click on Add icon to add a new Virtual Device. → Select Android API according to Android version → select Device from the list → Click on Next. ( Recommended device and settings are in the attached screenshots.)
Step 3: Install Open Gapps/Google Play Services:
- Power on the VM device.
- Click on Open Gapps icon on side bar. Follow the steps and it will automatically download and install Gapps in your VM device.
ii. Android Physical Device.
Note: We need an android device having Android OS version 6.0 or newer. Along with this we need to root the device (there are different ways to root the device, flashing Magisk is one of the popular and recommended way to root an android device.).
Step 1: Just plug in the android device with USB cable into the system where want to capture the traffic.
you can download ABD tools from Click here . It will redirect to a page where you can select the ADB tools package according to your host machine. Select “sdk for winodws/mac/linux”. and then select the required terms and download. extract the tools at any location.(at this location you need to navigate in cmd/terminal when need to use ADB tools). ADB tools are useful while doing the out of the box stuff on Android, like direct installing an app in device from your laptop/pc or pushing any file directly to any location. (We will see the use of ADB in the upcoming steps.)
To globally install ADB tools: go to start in windows → search for “edit the system environment variables”. → open it → in advance tab → Environment variables → select and edit PATH in system variables → Click on New → paste the path of ADB tools directory (where you extracted, Downloaded ADB tools zip.).
iv. Setting up proxy and Certificate in Android VM/device.
Step 1: Setting up the proxy in Android: Power on the Android device/Android VM from Genymotion (If it shows IP related error at bootup, then go to virtual box start the device listed there and power off after it gets an IP.) → Go to Settings → go to WIFI → Hold on Wifi name listed there and select Modify Network. → Select proxy as Manual → Input Hostname as you Host machine’s IP/Port which was used to set as proxy listener at Burp proxy setting → Save.
Step 2: Setting up the burp Certificate in Android:
Open cmd/terminal. Move to the directory where ADB tools are present.
Push burp certificate to the android device: There are two ways to add a certificate in the Android device.
i. Adding a Certificate into user-defined certificates.: (Recommanded) push burp certificate (having extension as .crt) using the command
» adb push path_to_certificate /sdcard/Download/«.
Switch to android device → Go to settings → Security → install from Sdcard → Select the certificate from Download folder → it will ask to enter a name, Enter any name here (eg. Burp CA). → It will ask to add PIN security. → Enter the security Pin. → Next.
ii. Adding a Certificate into system-defined certificates.: Download and install OpenSSL form Click here. → open cmd and run command
» openssl x509 -inform DER -in path_to_certificate/cacert.der -out path_to_certificate/cacert.pem»
then run.
» openssl x509 -inform PEM -subject_hash_old -in cacert.pem»
it will show as hash value copy it save it for further use.
then run .
» mv path_to_certificate/cacert.pem path_to_certificate/ .0» or simply rename the file cacert.pem as .0
Now copy the certificate tot the device. here is the list of commands to execute.
» adb remount» →
» adb push .0 /sdcard/Download» →
» adb shell» →
» mv /sdcard/Download/ .0 /system/etc/security/cacerts/» →
» chmod 644 /system/etc/security/cacerts/ .0«
Note: The benefit of adding a burp certificate into system-defined certificates is, we don’t need to follow step V. which is Frida setup. (But it’s not a recommended way because sometimes it misses some API calls.)
Reference: https://enderspub.kubertu.com/burp-suite-ssl-pinning
V. Frida installation in host PC and running frida server from Android device.
Step 1: Installation Frida in the host PC: run command to install Frida in host pc “ pip install frida-tools «.
Step 2: Running Frida from android device:
- run command “ adb shell getprop ro.product.cpu.abi » to know the processor architecture. →
- download the Frida server file from Click here. (Select your file according to the processor architecture if arm than arm file and if it is x86 than select x86 file.) →
- extract tile xz file → copy the file which is present in the extracted folder to the android device via the command “ adb push ./frida-server-12.x.y-android-xyz /data/local/tmp/ » →
- Now disable SELinux ( This is one time process.): “ adb shell » → in the shell: » su » → » setenforce 0 «.
- Start Frida server by command: “ adb shell » → » /data/local/tmp/frida-server-12.x.y-android-xyz & «
Step 3: Creating js file to do SSL pinning.: This needs to fix certificate-related errors and capture traffic in Burp suite.
create a js file named frida-ssl-pin.js And paste the following content in it and save the file.
var array_list = Java.use(“java.util.ArrayList”);
var ApiClient = Java.use(‘com.android.org.conscrypt.TrustManagerImpl’);
ApiClient.checkTrustedRecursive.implementation = function(a1, a2, a3, a4, a5, a6) <
// console.log(‘Bypassing SSL Pinning’);
var k = array_list.$new();
return k;
>
Step 4: Running the Frida receiver/client from the host machine.:
- Open the app in android device. now find the process name by running the command from cmd: “ frida-ps -U «. and copy the process name.
- run Frida receiver/client by running the command: “ frida -U -l path_to_js_file/frida-ssl-2.js —no-paus -f com.example.application «. This will open the app again.. and now you are ready to capture traffic in Burp Suite.
- Whenever the device restarts, We need to repeat the steps of running the Frida server from the android device.
- In the case mentioned in point 1, we need to start the Frida receiver/client in the host machine also.
Источник
Configuring Burp Suite With Android Nougat
Table of Contents
This last weekend I started testing a new Android app for fun, and ran into some trouble getting Burp Suite working properly. I burned a whole afternoon troubleshooting the issue, and decided to write up what I found out and two different ways I got it working.
Background
I’ve done quite a bit of Android testing in the past and my setup usually involves a Genymotion VM or my old rooted Nexus Tablet. I run Burp Suite locally, install the User Cert as outlined in Portswigger’s documentation, configure a WiFi proxy and I’m off the races.
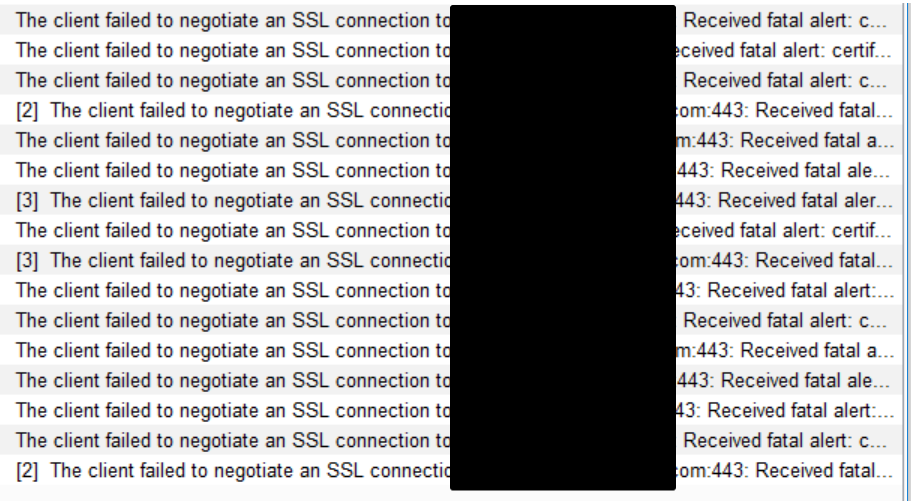
This particular app I wanted to test, however, required a minimum API level 24 (Android 7.0 — “Nougat”) and suddenly it wasn’t working. I followed the steps I always do but saw nothing but “connection reset” errors in Burp:
After a few frustrating hours of troubleshooting, I finally figured out the issue lied with the latest versions of Android (API >= 24). Before I go any further, all the information I needed was found in these great write-ups:
Starting with Nougat, Android changed the default behavior of trusting user installed certificates. It’s no longer possible to just install the Burp CA from the sdcard to start intercepting app traffic. Unless otherwise specified, apps will now only trust system level CAs. The failure happens “invisibly” and is responsible for all the alerts I saw in Burp Suite.
There’s two ways to bypass this, and I’ll walk through them both.
- Install the Burp CA as a system-level CA on the device. My recommendation for the easiest solution, but does require a rooted device. Also added benefit of not having to set a lockscreen PIN 🙂
- Modify the manifest and repackage the app. Slightly more work, but doesn’t require root privileges.
Note: I did all this with Burp Suite Pro on my Windows 10 machine and am using an Android 7.1 (API25) Genymotion VM, but the steps should be applicable to any setup.
Install Burp CA as a system-level trusted CA
Since the “traditional” way of installing a user certificate doesn’t work anymore in Nougat and above, for me the easiest solution is to install the Burp CA to the system trusted certificates. You can see all the system CAs that are bundled with an Android device by going to Settings -> Security -> Trusted Credentials and viewing system CAs. You’ll see the similar CAs you’d see in a browser bundle.
Trusted CAs for Android are stored in a special format in /system/etc/security/cacerts . If we have root privileges, it’s possible to write to this location and drop in the Burp CA (after some modification).
Export and convert the Burp CA The first step is to get the Burp CA in the right format. Using Burp Suite, export the CA Certificate in DER format. I saved it as cacert.der
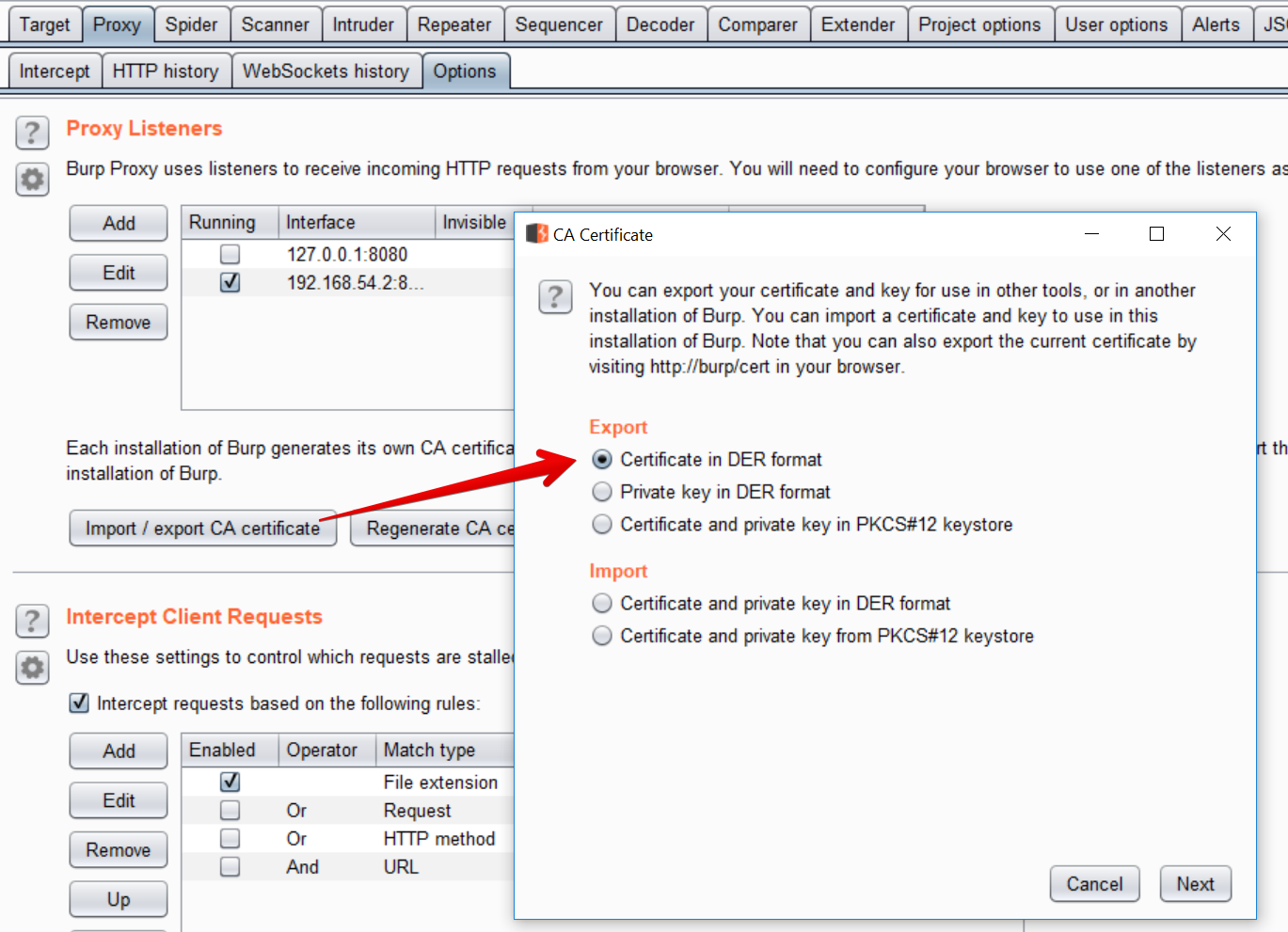
Android wants the certificate to be in PEM format, and to have the filename equal to the subject_hash_old value appended with .0 .
Note: if you are using OpenSSL subject_hash , not the “old” one
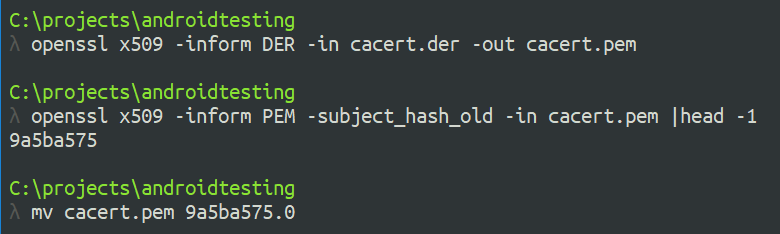
Use openssl to convert DER to PEM, then output the subject_hash_old and rename the file:
For example, with my certificate:
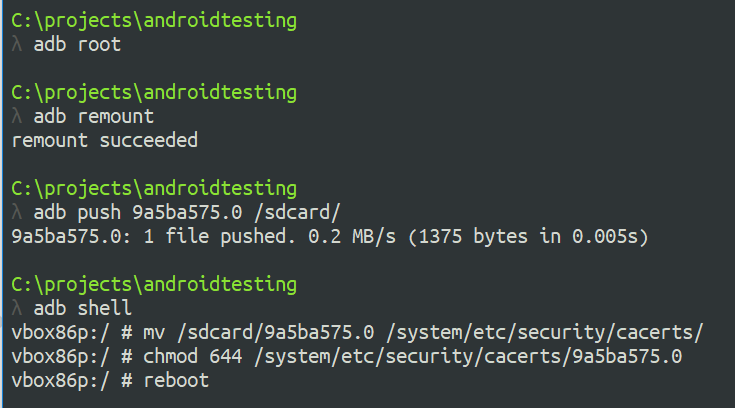
Copy the certificate to the device We can use adb to copy the certificate over, but since it has to be copied to the /system filesystem, we have to remount it as writable. As root, this is easy with adb remount .
The just drop into a shell ( adb shell ) and move the file to /system/etc/security/cacerts and chmod it to 644:
Lastly, we have to full reboot the device with either adb reboot or a power cycle.
After the device reboots, browsing to Settings -> Security -> Trusted Credentials should show the new “Portswigger CA” as a system trusted CA.
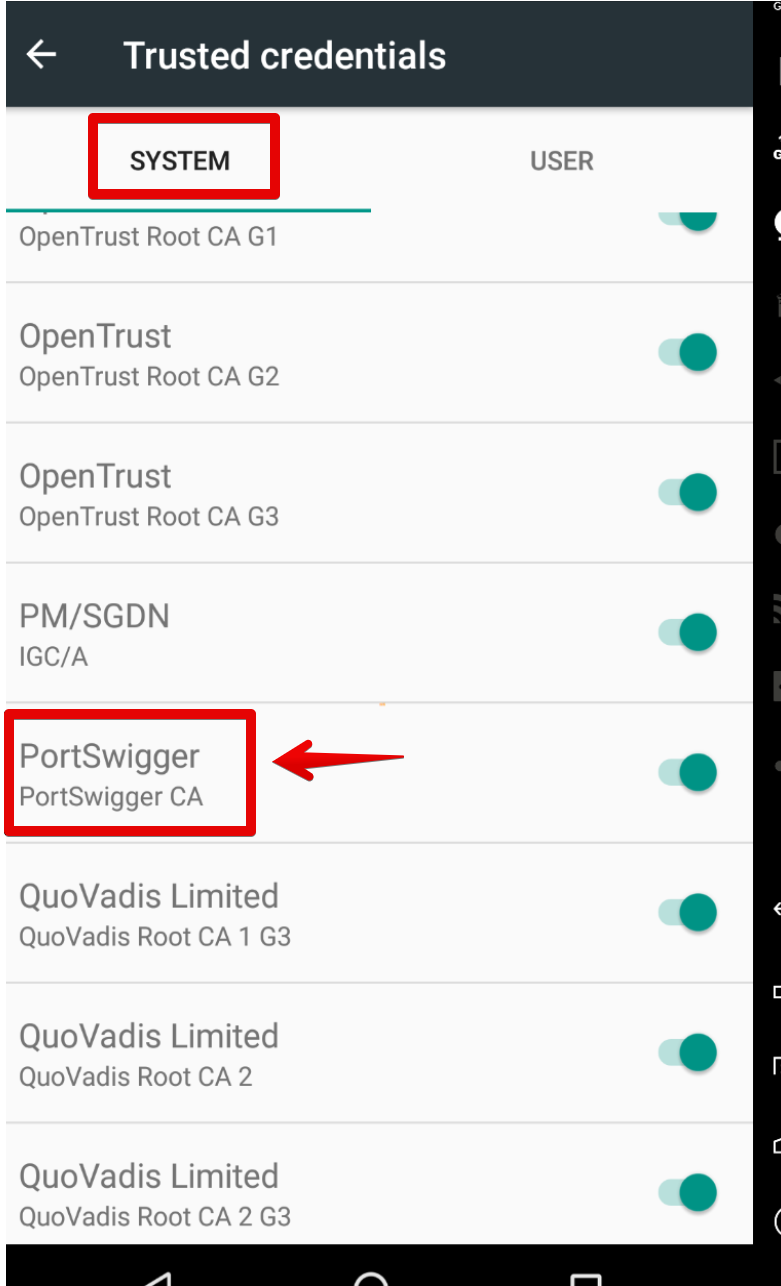
Now it’s possible to set up the proxy and start intecepting any and all app traffic with Burp 🙂
Mofiying and repackaging an app
If you don’t have root or don’t want to modify the system trusted certificates, you can install the Burp CA as a user cert and then modify the specific APK you want to MitM.
Starting with Nougat, apps will ignore user-installed certificates by default. This is evident by looking at logcat output when launching the app:
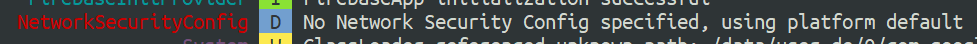
Without a network security config, the app will only trust system CAs and will not honor the user installed Burp certificate.
To get around this, it involves:
- Disassembling the APK
- Adding a new XML resource to define a network security profile
- Modifying AndroidManifest.xml
- Repackaging and self-signing the APK
Disassemble and modify the APK Start by using apktool to disassemble the APK
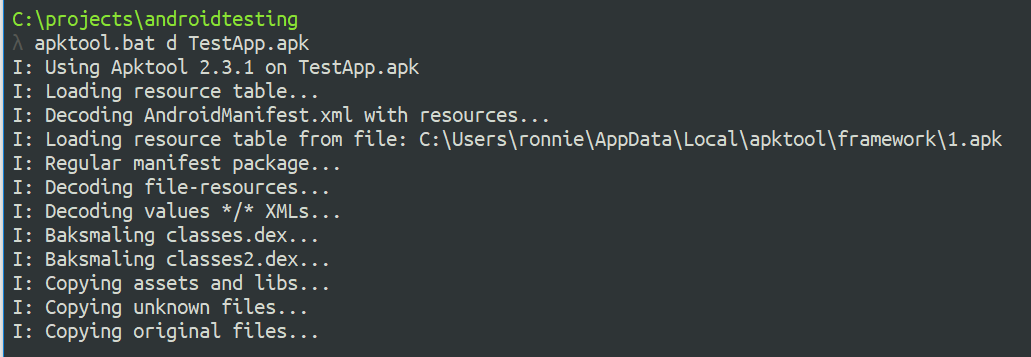
Next, add a new network security config by creating the file network_security_config.xml in the res/xml directory:
The config needs to explicitly state that trusting user certs is acceptable. The entire contents should be:
Finally, we have to define the network security config in AndroidManifest.xml . In the tag, add the android:networkSecurityConfig attribute pointing to the new XML file:
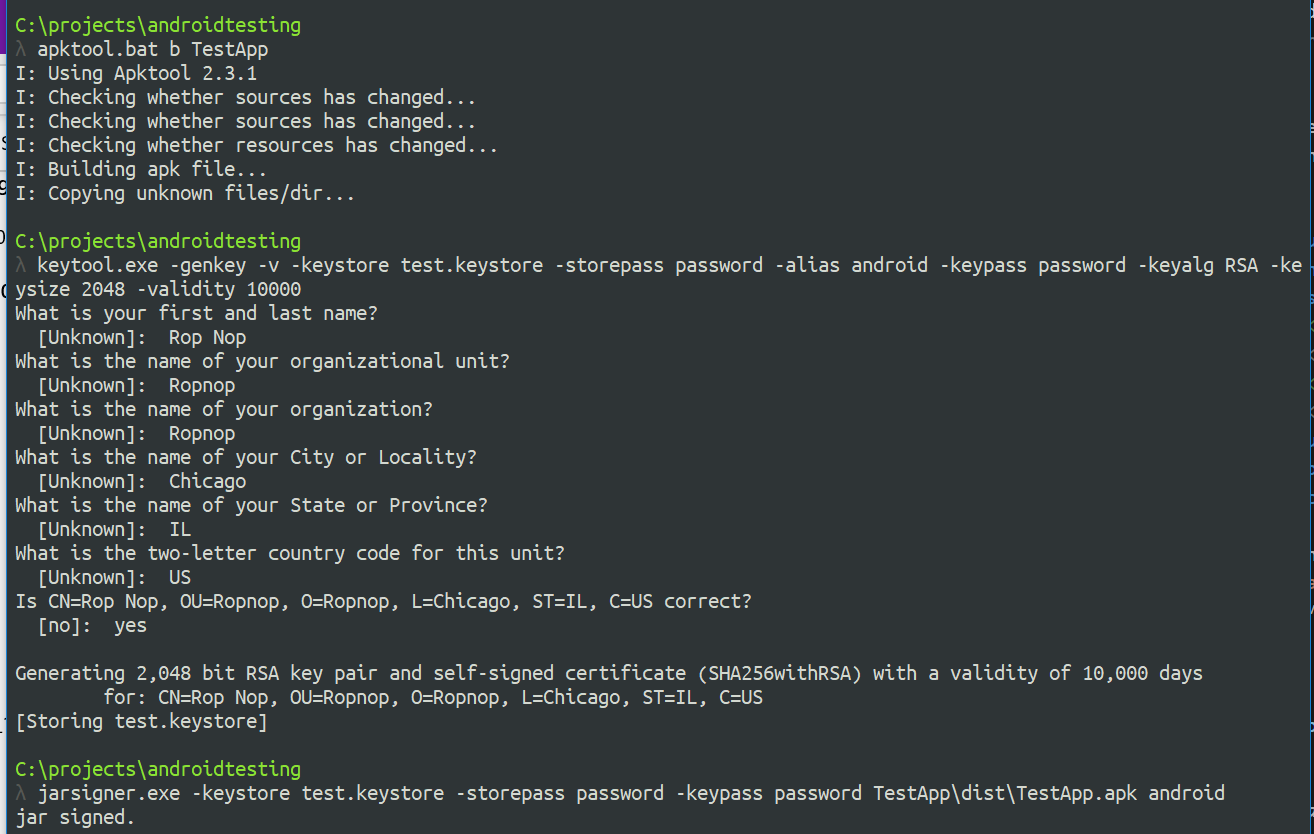
Reassemble and Sign Finally, the APK must now be rebuilt and signed in order to be installed. Using apktool b , a new build will be created in the dist/ directory:
To self-sign the app, use keytool to create a new keystore and key, then jarsigner to sign the new APK:
Lastly, install the new APK with adb :
Now, when we start the application, the logcat output will indicate a new network security config is being used:
With the Burp CA installed to user certificates, we can now MitM the application traffic!
Источник










