- Oversecured detects dangerous vulnerabilities in the TikTok Android app
- Vulnerability via NotificationBroadcastReceiver
- Vulnerability via DetailActivity
- Vulnerability via IndependentProcessDownloadService AIDL interface
- DenTNT.trmw.ru
- Записная книжка
- Android: Удалить предустановленные приложения на Meizu 16th
- Шаг 1
- Шаг 2
- Com ss android ugc aweme
- Com ss android ugc aweme
Oversecured detects dangerous vulnerabilities in the TikTok Android app
Oversecured is a startup focused on automatic vulnerability detection in mobile apps. We have created a cool technology that allows us to find vulnerabilities in Android apps developed using any technology or framework. The service is SaaS-based and allows anyone to check the security of any app they’re using. We’re providing an option for security researchers to scan arbitrary apps in order to submit discovered bugs to app owners, and a business option allowing developers to integrate Oversecured into the development process and scan each new version of the app before rolling it out to app markets. Sign up now to scan arbitrary apps and find your own vulnerabilities!
Oversecured has once again uncovered high-severity vulnerabilities, this time in the TikTok app. The app contained one vulnerability to theft of arbitrary files with user interaction and three to persistent arbitrary code execution. All these vulnerabilities could have been exploited by a hacker if a user had installed a malicious app onto their Android device. All the vulnerabilities have been removed. Users should update to the latest version on Google Play to enjoy the best experience.
Oversecured security researchers scanned the app and discovered the following: 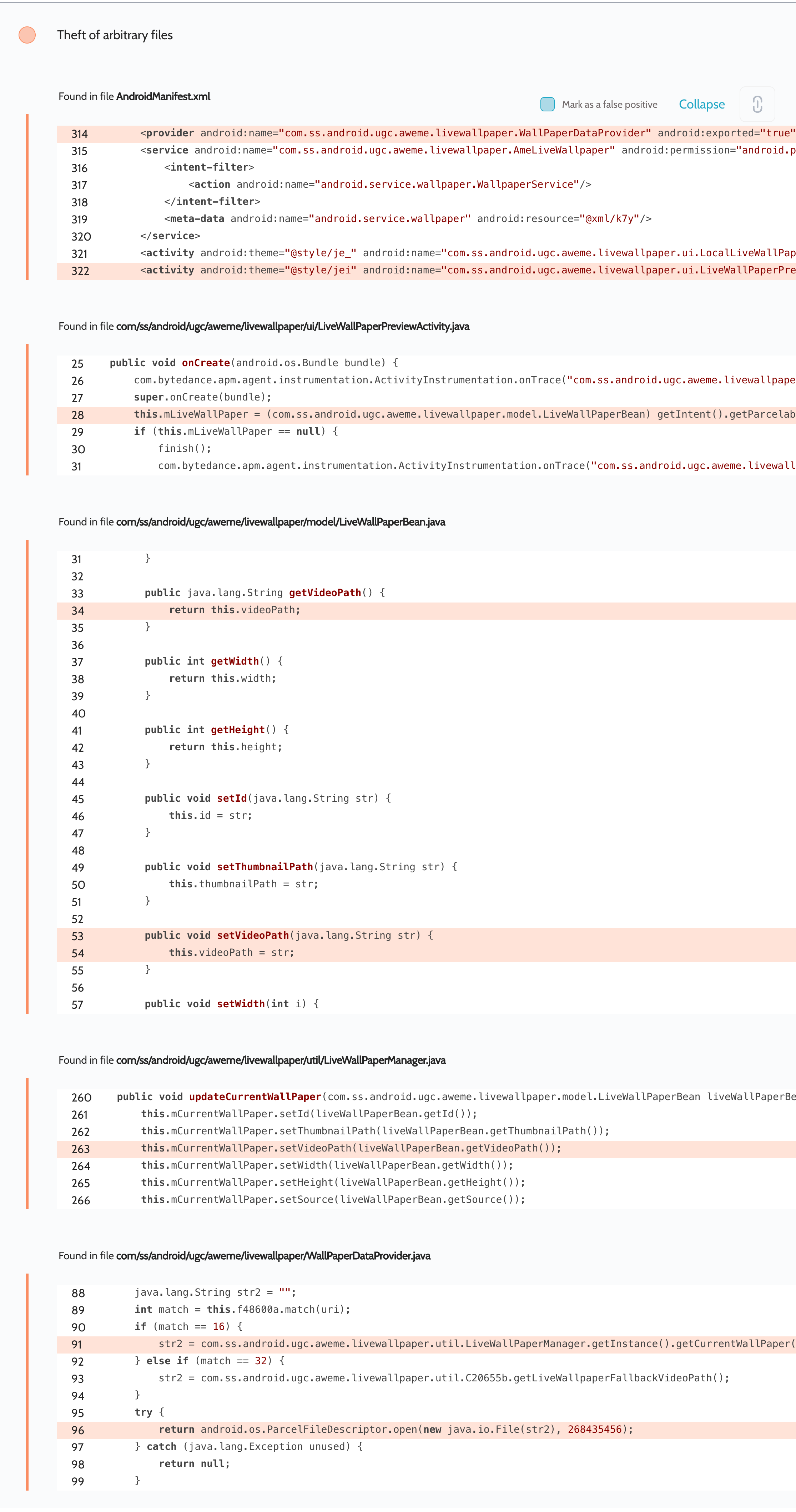
Since the path was fully controllable by the attacker, this provided read-only access to arbitrary files. An attacker could therefore gain access to any files stored in the app’s private directory, and also to history, private messages, and session tokens, resulting in complete access to the user’s account.
Proof of Concept
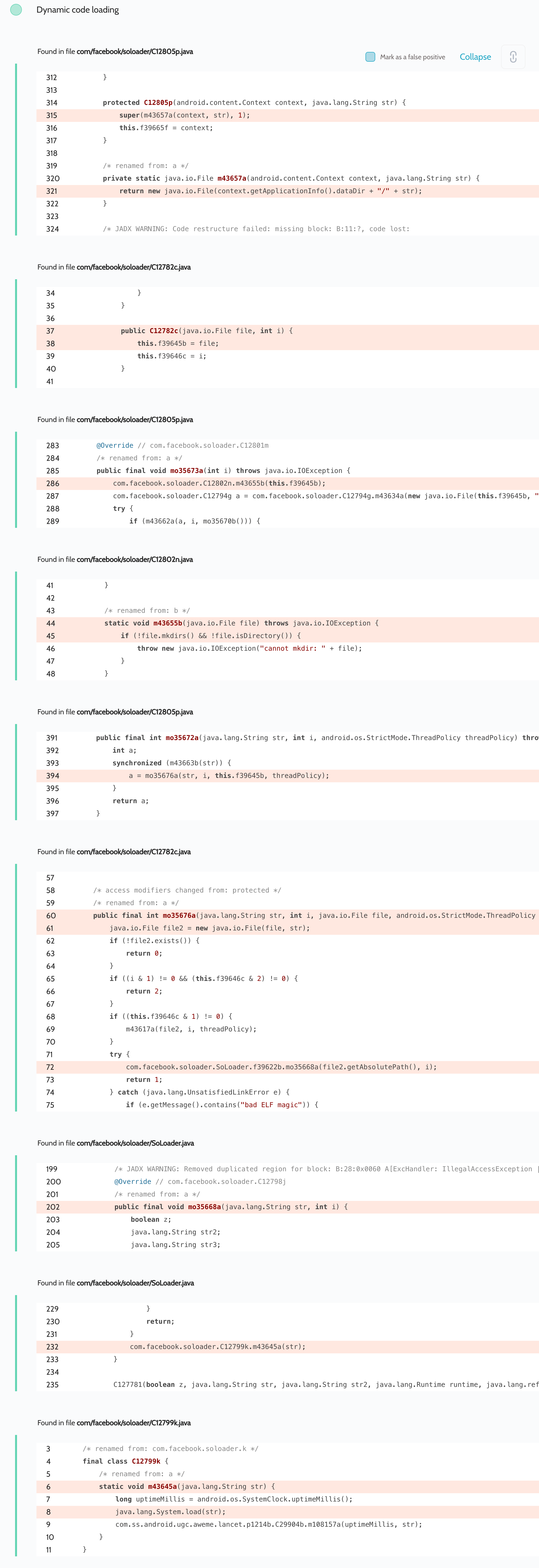
All code execution vulnerabilities were chained from two independent vulnerabilities: rewriting arbitrary files and dynamically loading code from a file. There are two types of native libraries on Android: libraries stored in the app’s resources ( app.apk/lib/. ) and libraries loaded dynamically from files. The first type have owner and group set to system , so even the app itself only has read-only access to those files. But the second are usually loaded into the app using a java.lang.System.load(path) call and can have arbitrary ownership, which is why developers often choose this approach to load dynamic code. In all three cases, Oversecured researchers discovered three separate libraries that were used to create Proof of Concepts. The vulnerability could have been exploited by an app that was only run once and then, say, deleted. The library would have been written to the app’s private directory and could have been loaded by the app even after the phone was rebooted or the app restarted. All vulnerabilities relating to arbitrary code execution would have lead to the app and its users becoming thoroughly compromised. The PoC we sent to TikTok made it possible to gain access to arbitrary files stored in the private directory, thus providing access to the user’s account as well as their private messages and videos. Moreover, an attacker could do the same things that the TikTok app could based on its permissions: access user pictures and videos stored on the device, audio records and web browser downloads, record audio and video from the user’s microphone and camera without consent when the app is in use, and read contacts. All the data obtained could have been sent to the attacker’s server in the background without the user knowing, and then analyzed.
Vulnerability via NotificationBroadcastReceiver
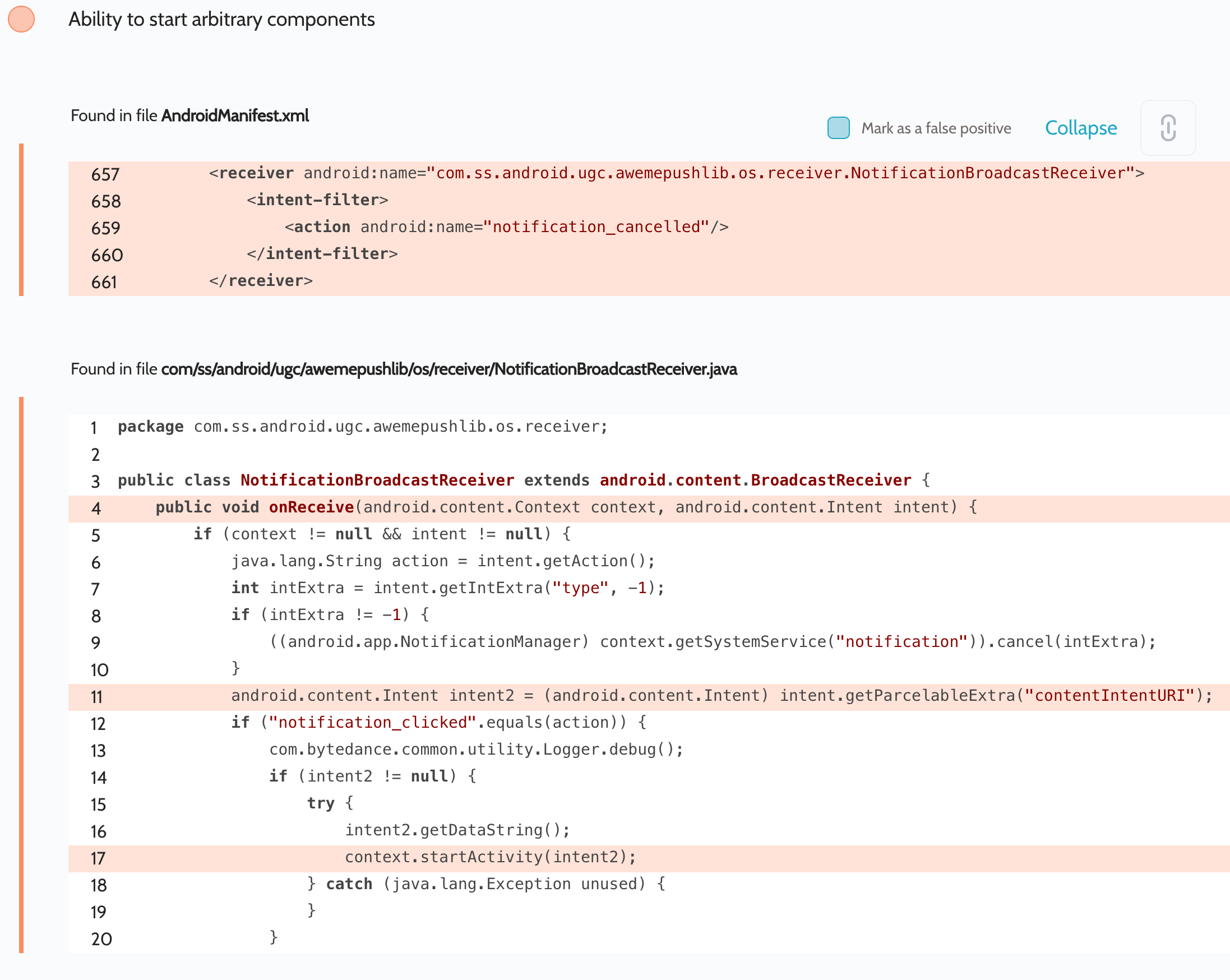
It also receives an Intent from key contentIntentURI and passes it to startActivity(. ) . Thus, an attacker gains the ability to launch arbitrary activities with arbitrary data and flag values. As we described in our article on Access to app protected components, the attacker can gain access to arbitrary Content Providers with the parameter android:grantUriPermissions=»true» . A provider like this was discovered in the TikTok app:
which makes it possible to obtain read/write access to arbitrary files:
using path . The attacker can generate a URI like content://com.zhiliaoapp.musically.fileprovider/name/data/user/0/com.zhiliaoapp.musically/etc
to access arbitrary protected files belonging to the app.
We then discovered a large number of references to native libraries in the app’s code. The most interesting point is that these native libraries are often not even used by the app. In these cases they create a predefined path to the library (for example, /data/user/0/app_package/files/lib.so ) and verify its existence using File.exists() , calling System.load(path) if it does exist. That is just what we found in the case of TikTok: a large number of references to libraries that the app was not using and that an attacker would have needed to write a pre-created file to a predefined path in the TikTok app’s private directory.
In this case we studied the app’s scan report once again, specifically the Dynamic code loading section, and found a lot of references in the app:
For this PoC we selected a library located at the path /data/user/0/com.zhiliaoapp.musically/lib-main/libimagepipeline.so .
Proof of Concept
The attacker needs to create a native library in advance (e.g. by compiling their app and extracting the library from it), using the following code fragment:
When the library is loaded to System.load(path) the command chmod -R 777 /data/user/0/com.zhiliaoapp.musically/ is executed and changes file rights from private to world-readable/writable.
Code in the attacker’s app:
When TikTok is launched next, and on all subsequent occasions, it will automatically load the specified library and execute the code contained in it, leading to persistent arbitrary code execution.
Vulnerability via DetailActivity
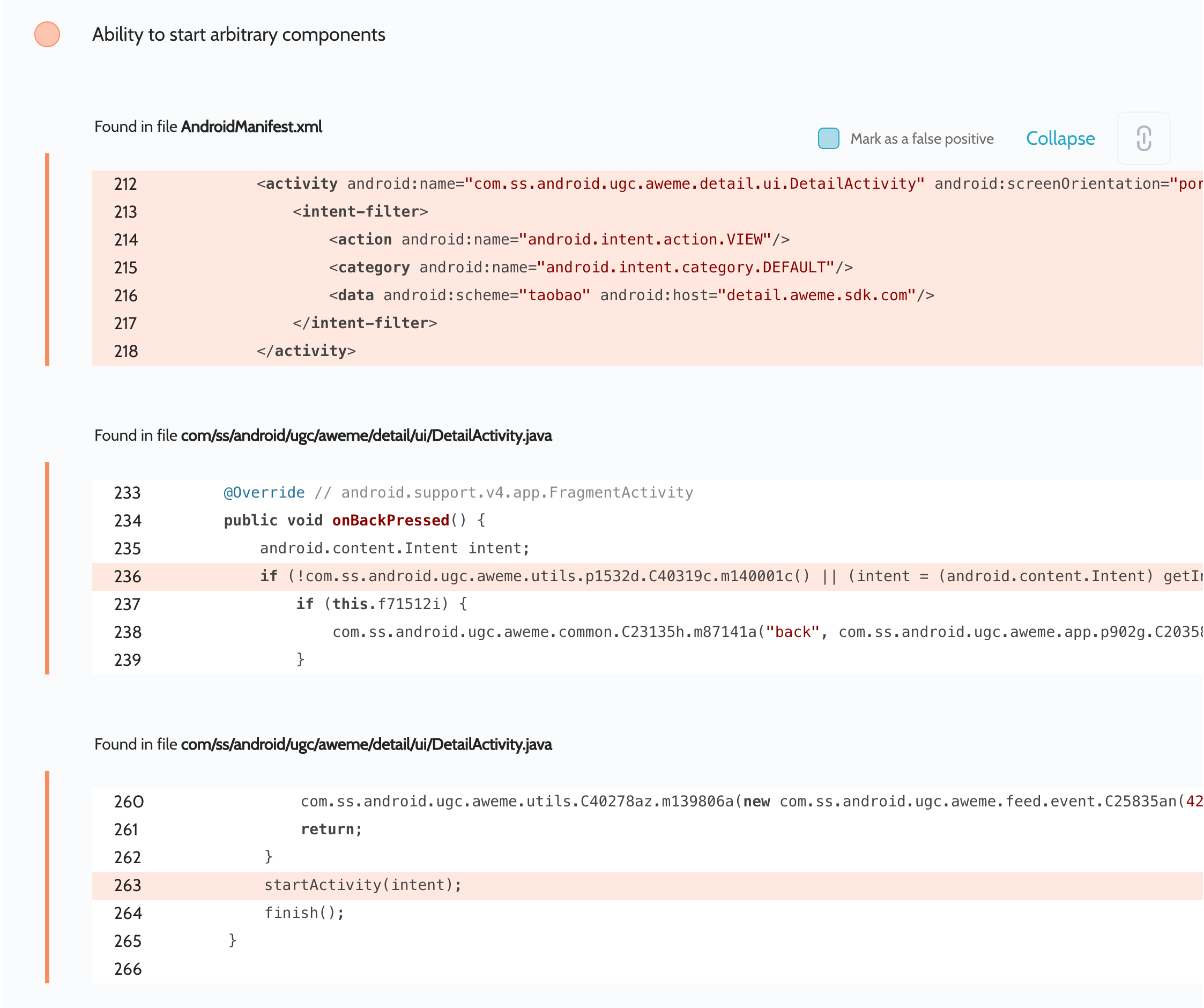
it then passes the object it receives to startActivity(. ) when the phone’s Back button is pressed
As in the previous PoC, we used the provider com.zhiliaoapp.musically.fileprovider to write arbitrary files to the library at /data/user/0/com.zhiliaoapp.musically/app_librarian/14.7.5.6172264464/libAkeva.so
Proof of Concept
The code to generate the native library is the same. The Java code for the attacker’s app:
Vulnerability via IndependentProcessDownloadService AIDL interface
The app also included an unprotected service com.ss.android.socialbase.downloader.downloader.IndependentProcessDownloadService , which returned a binder object in the file com/ss/android/socialbase/downloader/downloader/DownloadService.java :
allowing the attacker to call arbitrary methods belonging to this interface. One of the methods available is tryDownload , which takes a URL for file download, a file name, and a save path. To exploit this vulnerability successfully, an attacker would have needed to create an object of class com.ss.android.socialbase.downloader.model.DownloadInfo and write the necessary values to it, then pack it to com.ss.android.socialbase.downloader.model.DownloadTask and use app code via the Reflection API to convert it into the right format for passing via AIDL.
Proof of concept
Dangerous vulnerabilities can be found even in the most popular apps, such as TikTok. Oversecured aims to help developers correct all vulnerabilities in their apps. We are glad we could make TikTok more secure, and we are grateful to the TikTok team for their responsiveness, their quick reaction, and their help in uncovering the vulnerabilities.
Источник
DenTNT.trmw.ru
Записная книжка
Android: Удалить предустановленные приложения на Meizu 16th
Аналогично с инструкцией для Honor/Huawei удаляем китайские предустановленные приложения для Meizu 16th.
Для удаления китайских (неудаляемых) приложений без root, можно воспользоваться ADB.
Шаг 1
1. Для начала нужно включить режим разработчика:
Настройки ▶ О телефоне ▶ Версия прошивки (7 раз)
2. После ввода пароля появится уведомление о том, что «Вы стали разработчиком».
3. Включаем отладку по USB:
Настройки ▶ Специальные возможности ▶ Для разработчиков ▶ [ОТЛАДКА] ▶ Отладка по USB ▶
4. Можно проверить, видно ли устройство через ADB:
Шаг 2
5. Заходим в adb-шелл (все команды далее выполняются в шелле):
6.Выводим список установленных программ (пакетов):
7. Выбираем нужные (скорее ненужные) для себя программы и для каждой выполняем команду pm uninstall -k —user 0
- Flyme DSGame — мини-игры:
- Meizu Reading — приложение для чтения:
- Каая-то утилита для работы с базовой станцией (ненужное мне барахло):
- Migu Music:
- VipShop — тут и так всё понятно:
- Andreader — электронная книга:
- Baidu Searchbox — китайский аналог приложения поиска от Google:
- Jingdong mall — онлайн покупки:
- 美团-团购美食电影 — Приложение для онлайн заказов (актуально для Китая):
- Weibo — китайский сервис микроблогов:
- Sogou — китайский редактор методов ввода пиньинь:
- Новостной агрегатор:
- TikTok:
- Taobao — очередной сервис онлайн-покупок:
- Ctrip путешествия — Сервис бронирования отелей и т.п. услуги для путешествий:
- Ассистент (аналог Google-ассистент):
- Поиск Google:
- Экранный помощник Flyme:
- Миграция (перенос данных):
- Поиск:
Источник
Com ss android ugc aweme
Краткое описание:
Социальная сеть для будущих звёзд музыки.
Описание:
«musical.ly — самая большая в мире платформа для креативных людей. В musical.ly любой может в считаные секунды снять классный клип и поделиться им со всем миром. Скачайте лучшее приложение для создания коротких видео и станьте звездой!
Лучшее сообщество крутых коротких видео. Наслаждайся своим летом с TikTok!
TikTok — это глобальное видеосообщество. Здесь вы найдете классные короткие видео и сможете поделиться яркими моментами из собственной жизни со всем миром. Снимайте оригинальный контент с масками, фильтрами и стикерами. Жизнь пролетает быстро — каждая секунда на счету!
■ Миллионы видео, подобранные для вас
Мы создаём ленту на основании видео, которые вам нравятся. TikTok подстраивается под ваши вкусы и показывает интересный вам контент.
■ Сообщество креативных людей
Тысячи авторов оригинального контента делятся в TikTok своими талантами и идеями. В TikTok каждый может раскрыть свой творческий потенциал!
■ Огромная звуковая библиотека
Накладывайте миллионы бесплатных треков и интересных звуков на свои видео. Мы регулярно обновляем библиотеку с популярной музыкой во всех жанрах.
■ Оригинальные эмодзи и маски
Выведите свои видео на новый уровень с 100+ бесплатными эмодзи, кучей масок и бьюти-эффектами.
■ Простые в использовании инструменты для создания и редактирования видео
■ Регулярно обновляемые маски для прямых эфиров
Требуется Android: 4.4+ / 4.1+
Русский интерфейс: Да
Для общения не по теме приложения (оффтоп), создан Клуб TikTok’a: Клуб Пользователей TikTok
версия: 10.7.1 GP ]TikTok — вместе с musical.ly
версия: 8.3.1 TikTok — вместе с musical.ly (Пост hussein209 #76632232)
версия: 8.0.0 Сообщение №30, автор siegheilx
версия: 6.8.0 musical.ly (Пост visitov2013 #71345231)
версия: 5.5.0 musical.ly (Пост Kirishak #61193851)
версия: 5.0.4 musical.ly (Пост v;adden #60476505)
версия: 5.0.3 musical.ly (Пост speed888 #57616824)
версия: 5.0.2 musical.ly (Пост CyberEgo #57370110)
версия: 4.5.2 
Сообщение отредактировал iMiKED — 29.11.21, 16:06

What’s New
— bug fix
Сообщение отредактировал CyberEgo — 20.01.17, 00:03
musical.ly 5.0.3. Обновлено 22 января 2017 года.
APK: 
Источник
Com ss android ugc aweme
Обсуждение Motorola Edge 20 Pro (Global)/Edge S Pro (China)

Описание | Обсуждение » | Motorola Edge 20 » | Покупка » | Обсуждение камеры »
Платформа: Android 11, оболочка My UX (Global)/MY UI 2.0 (China)
Процессор: Qualcomm Snapdragon 870 (1 Cores Kryo 585 Prime Cortex A77 3.2 GHz + 3 Cores Kryo 585 Gold Cortex A77 2.42 GHz + 4 Cores Kryo 585 Silver Cortex A55 1.8 GHz, Adreno 650 GPU)
Экран: 6.7′, 2400×1080 FHD+ P-OLED, 20:9, 405 ppi, 144 Hz (touch 576 Hz), HDR10+, Corning Gorilla Glass 5
Оперативная память: 12 GB LPDDR5 2750 MHz — Global, 6/8/12 GB LPDDR5 2750 MHz — China,
Встроенная память: 256 GB UFS 3.1 — Global, 128/256 GB UFS 3.1 — China
Расширяемая память: не поддерживается
Стандарты связи:
Global
2G: GSM band B2/3/5/8
3G: WCDMA band B1/2/4/5/8
4G: LTE-FDD band B1/2/3/4/5/7/8/12/13/17/20/26/28/32/66
4G: LTE-TDD band B34/38/39/40/41/42/43
5G: band n1/n3/n5/n7/n8/n28/n38/n41/n66/n77/n78
China
2G: GSM band B2/3/5/8
3G: WCDMA band B1/2/5/8
4G: LTE-FDD band B1/2/3/4/5/7/8/12/17/20/26/28
4G: LTE-TDD band B34/38/39/40/41
5G: band n1/n28/n41/n78
Сим-карты: Nano-sim (2sim)
Основная камера: тройной модуль
Основной сенсор (wide) — 108mp, F/1.9, 0.7μm (в бининге 2.1μm — 12mp), PDAF autofocus
Дополнительный сенсор (ultrawide) — 16mp, F/2.2, 1.0μm, autofocus, Macro mode
Дополнительный сенсор (telephoto) — 8mp, F/3.4, 1.0μm, 5x Optical zoom (50x Digital zoom), PDAF autofocus, OIS stabilization
Фронтальная камера: одинарный модуль
Основной сенсор (wide) — 32mp, F/2.25, 0.7μm (в бининге 1.4μm — 8mp), fixed focus
Видеозапись: 8K [email protected], 4K UHD [email protected]/60fps, FHD [email protected]/60fps, Slow motion video FHD [email protected]/960fps, HD [email protected], EIS
Периферия: WiFi 802.11 a/b/g/n/ac/ax (2.4GHz и 5GHz), Wi-Fi 6, 2×2 MIMO, 8×8 MU-MIMO, Bluetooth 5.1, GPS, A-GPS, Galileo, GLONASS, поддержка NFC, USB Type-C 3.1
Датчики: сканер отпечатков в боковой гране, Gravity sensor, Ambient light sensor, Proximity sensor, Gyro, Accelerometer, Compass
Звук: кодек Qualcomm Aqstic WCD9385, 3 mic, single speakers, Waves Maxx® Audio Mobile
Аккумулятор: встроенный, 4500/4520 mAh, быстрая зарядка TurboPower 30w/33w (10v-3a/11v-3a), поддержка QC4.0+/PD3.0
Корпус: алюминиевая рама, тыльная поверхность из стекла или из веганской кожи, Water repellent design, защита от брызг IP52
Размеры: 163.5×76.2×7.99/8.49mm, 185/189g
Доступные цвета: Midnight Blue, Iridescent White, Blue vegan leather
Источник