- Android
- Setting up your Android device
- A quick smoke-test
- Tracing open() calls in Chrome
- 💉 Frida’s Gadget Injection on Android: No Root, 2 Methods
- Alexandr Fadeev
- How it basically works
- Note: where to get an APK
- Method 1: Inject a libfrida-gadget.so as a dependency to a native library (JNI) inside of APK
- Steps
- Method 2: Injecting into bytecode
- Steps
- Check whether injection succeeded
- Error: Unable to create socket
- What’s Next ⏭️
- Research what files are being used
- Research data encryption
- Research more
- The Shadow of CSSLP
- Cheat Sheet: Legal, Regulations, Compliance in Security
- How I Passed CISSP
- Hacking Android app with Frida
- Motivation
- Preparation
- Getting ready
- phone
- Installing stuff
- Hello Frida
- Action
- Change method implementation
- Run method
- Bruteforce PIN breaking
- Listing loaded objects
- Imaginary Security
- Let there be instance
- Debug release
- Summarization
Android
In this tutorial we show how to do function tracing on your Android device.
Setting up your Android device
Before you start, you will need to root your device in case you haven’t done so already. It is technically also possible to use Frida without rooting your device, for example by repackaging the app to include frida-gadget, or using a debugger to accomplish the same. But, for this introduction we’re going to focus on the simplest case: a rooted device.
Also note that most of our recent testing has been taking place on a Pixel 3 running Android 9. Older ROMs may work too, but if you’re running into basic issues like Frida crashing the system when launching an app, this is due to ROM-specific quirks. We cannot test on all possible devices, so we count on your help to improve on this. However if you’re just starting out with Frida it is strongly recommended to go for a Pixel or Nexus device running the latest official software, or a device whose software is as close to AOSP as possible. Another option is using an emulator, ideally with a Google-provided Android 9 emulator image for arm or arm64. (x86 may work too but has gone through significantly less testing.)
You will also need the adb tool from the Android SDK.
First off, download the latest frida-server for Android from our releases page and uncompress it.
Now, let’s get it running on your device:
For the last step, make sure you start frida-server as root, i.e. if you are doing this on a rooted device, you might need to su and run it from that shell.
adb on a production build
If you get adbd cannot run as root in production builds after running adb root
you need to prefix each shell command with su -c . For example: adb shell «su -c chmod 755 /data/local/tmp/frida-server»
Next, make sure adb can see your device:
This will also ensure that the adb daemon is running on your desktop, which allows Frida to discover and communicate with your device regardless of whether you’ve got it hooked up through USB or WiFi.
A quick smoke-test
Now, on your desktop it’s time to make sure the basics are working. Run:
This should give you a process list along the lines of:
Great, we’re good to go then!
Tracing open() calls in Chrome
Alright, let’s have some fun. Fire up the Chrome app on your device and return to your desktop and run:
Now just play around with the Chrome app and you should start seeing open() calls flying in:
You can now live-edit the aforementioned JavaScript files as you read man open , and start diving deeper and deeper into your Android apps.
Источник
💉 Frida’s Gadget Injection on Android: No Root, 2 Methods
You will learn how to inject Frida’s Gadget into Android application (APK) using 2 different methods without having to root your Android device.
Alexandr Fadeev
You have 2 options to inject Frida’s Gadget to Android application:
Basic use case: you’ve got a third-party APK (Android application package), and you want to debug/trace/explore/reverse-engineer it, and you have your personal Android phone which you don’t want to root. It means you need Frida’s Gadget.
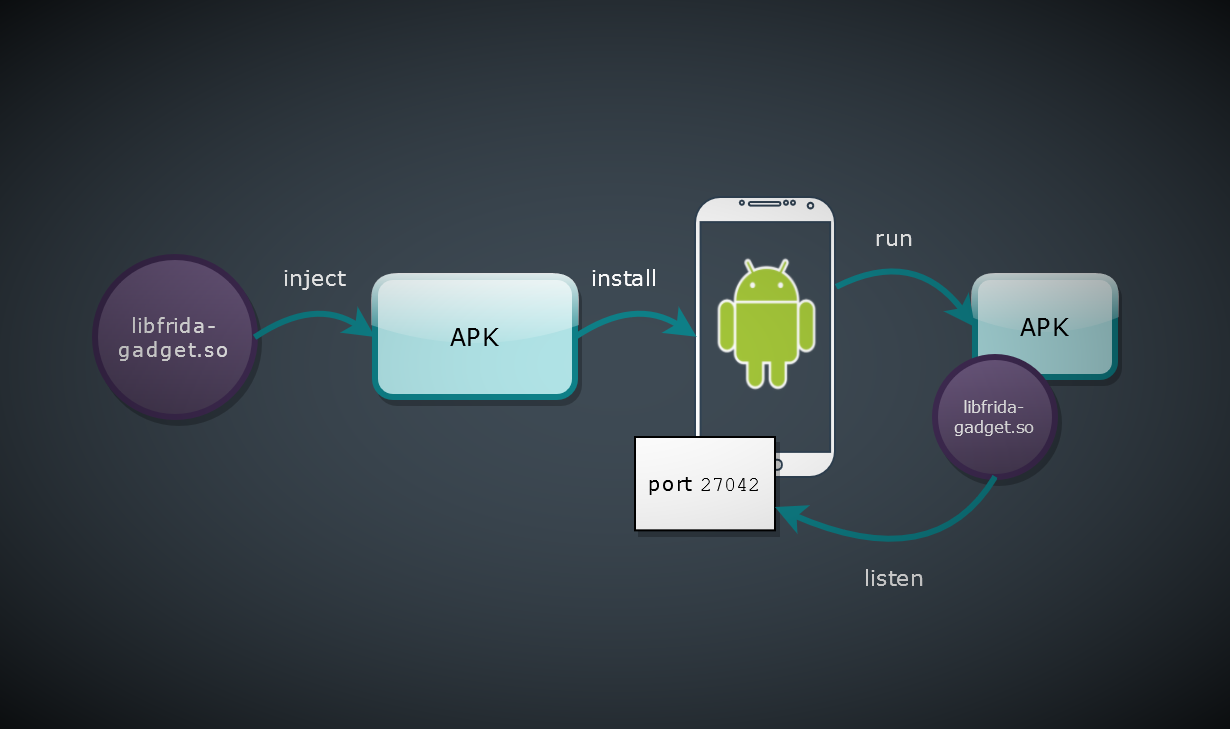
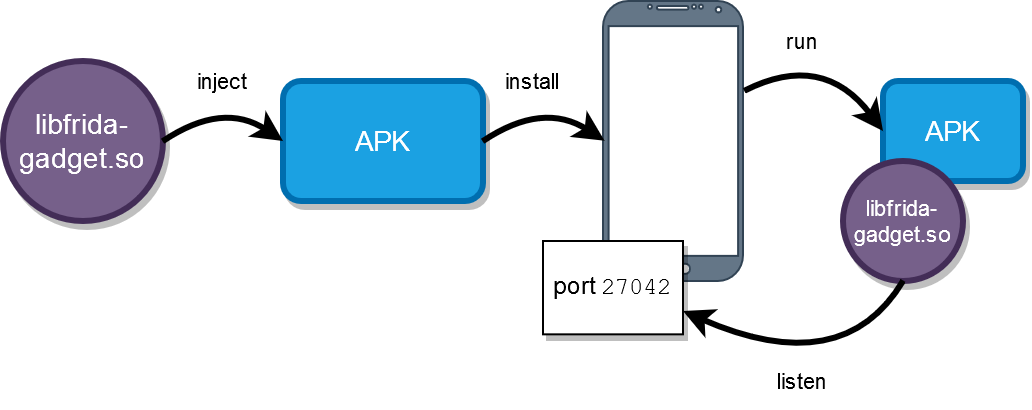
How it basically works
Note: where to get an APK
Google Play doesn’t allow you to download APK directly. If you decide to analyze some APK, but you haven’t got one yet, you have a bunch of options then: https://www.google.com/search?q=download+apk.
Method 1: Inject a libfrida-gadget.so as a dependency to a native library (JNI) inside of APK
📝 Basically, you need this article: https://lief.quarkslab.com/doc/stable/tutorials/09_frida_lief.html. The reason I’ve put my own steps here is a lot of caveats aiming to save time in future because of buggy versions of different tools, and because I’d like to escape all unnecessary steps I usually tend to follow.
✔️ For the shared library injection your APK should contain some native library (most probably a JNI library), and the injection is carried out by adding dependency to the native library.
⚠️ If the APK doesn’t contain native library then jump to the method #2.
Steps
Let’s say we want to inject libfrida-gadget.so to /lib/arm64-v8a/libfromapk.so .
- Download and unpack frida-gadget >= 12.8.8 for Android for arm64 (or arm32) from here https://github.com/frida/frida/releases. ⚠️ WARNING: Frida Gadget from 12.7.0 to 12.8.7 doesn’t bring up the server, and the bug was solved here: https://github.com/frida/frida-core/issues/286.
- Download and unpack your target APK. ⚠️ WARNING:
- Use apktool >= 2.4.1 .
- -rs is to not decode resources and sources, it will save you time and keep your nerves while compiling the APK back.
- unzip / zip doesn’t always work — application may not bring up.
- Copy frida-gadget to the unpacked APK directory.
- Write a Python script (say inject-gadget.py ) to inject the frida-gadget using lief (see installation instructions here: https://github.com/lief-project/LIEF).
- Run the script — patch libfromapk.so JNI.
- Check the injection succeeded.
- Re-pack APK.
- Sign APK.
I used «Uber APK signer»: https://github.com/patrickfav/uber-apk-signer ⚠️ WARNING: Archive should have *.apk extension to make Uber Signer work! - Install APK. ⚠️ WARNING:
- Allow untrusted third-party APK on your phone.
- Use -r flag to «reinstall» APK.
- Check the frida-gadget presence as described in the following chapter, but shortly:
- Trace the application (attach to gadget):
Pay attention that the Frida’s Gadget should start after you trigger some use case in your targeted Android application which loads the native library. The application invokes System.loadLibrary to load libfromapk.so and the latter loads libfrida-gadget.so . It may happen at any time and not mandatory at the application start. Try to work with an app for a while. For example, if you injected into libcrypto.so , then do some operations which use encryption. And then check again. Basically, application should freeze 💤 at the moment of gadget spawn. Also you can try to inject to another library.
Method 2: Injecting into bytecode
Inject a System.loadLibrary(«frida-gadget») call into the bytecode of the app, ideally before any other bytecode executes or any native code is loaded. A suitable place is typically the static initializer of the entry point classes of the app, e.g. the main application Activity, found via the manifest. An easy way to do this is to add the following smali code in a suitable function:
➡️ A «suitable place» could be a constructor of a main activity right above return statement which you can find in the AndroidManifest.xml (look for an . . tag).
Load libfrida-gadget.so from the function of the MainActivity
Pay attention that in this case Frida gadget will be loaded at the application start, so you have to connect to the one quickly from the computer:
Steps
- Disassemble
- Use apktool >= 2.4.1.
- Use -r to keep your nerves at the re-packing stage which is a buggy thing usually (let me drop details here).
- Download
- Use frida-gadget >= 12.8.8, see https://github.com/frida/frida-core/issues/286.
- Copy
- Find a smali file which contains main activity class. or ⚠️ Your APK may have main activity with a different class name. Try to investigate!
- Edit
1 Edit target/smali/. /A.smali (smali file with main activity).
2 Add a loadLibrary call there as shown below: - Build
- Sign
- Install
- Check the frida-gadget presence as described in the following chapter, but shortly:
- Trace the application (attach to gadget):
For more details about each step see description of the method #1.
Check whether injection succeeded
In both cases you need to know whether frida-gadget has been injected successfully.
- When Frida Gadget starts, it prints a log with Frida tag. If you see an error with Frida tag, it still means that injection succeeded basically, and Gadget is trying to start, but something else is wrong and additional investigation is needed (e.g. see how to fix «Error: Unable to create socket»).
- When Frida Gadget spawns it tries to create a listening socket on the port 27042. Use adb to connect to device and check the presense of the server.
- Use frida-ps to check whether Frida Gadget created a listening socket on device successfully. Use -U argument to verify your device via USB.
Error: Unable to create socket
You may see this error (if not, jump to the next chapter about how to research your application):
It means that APK doesn’t have INTERNET permissions. Check this in AndroidManifest.xml:
You will probably not see the corresponding permission (you see empty output from grep ).
Add the next line to AndroidManifest.xml in this case:
What’s Next ⏭️
Research what files are being used
For example, I started with a script to trace any request to filesystem which is the basic step to start from.
If you want to modify the initial script, then download it from codeshare (e.g. to tracefs.js ), modify it, and use like the following:
Research data encryption
Often you will need to catch a moment when application starts to encrypt some data, so you could print that data before it’s going to be encrypted. You can use my code snippet to intercept Java Crypto API, to print a symmetric key and data right before the final encryption step.
This code snippet is a simple and easy point to start, and there are other powerful cryptography interceptors on https://codeshare.frida.re (e.g. https://codeshare.frida.re/@dzonerzy/aesinfo/).
Research more
- Go to https://github.com/iddoeldor/frida-snippets and take there anything you need to trace with frida .
- https://codeshare.frida.re is an authentic source of Frida code snippets.
The Shadow of CSSLP
or «How I Passed CSSLP». My detailed feedback about preparation for CSSLP, study materials, training process, and passing CSSLP examination.
Cheat Sheet: Legal, Regulations, Compliance in Security
My cheat sheet I used to prepare for CISSP about how I understand and memorize legal and regulations in cybersecurity. I publish it because I use it, and you can use it too.
How I Passed CISSP
I have been awarded the CISSP certification! Here is how.
Источник
Hacking Android app with Frida
Side image is of course Frida Kahlo auto portrait, besides her name she has no connection with topic
Motivation
Lately I attended to Sekurak hacking party — it’s event organized by Sekurak where they show how easy is to hack stuff like IP cameras, routers, phones. I guess Sekurak is known mainly in Poland, but they are real professionals in area of security. During this event Michał Bentkowski was showing how easy it is to spy on Android app communication and also change app behavior using tool named Frida. It was cool but scary at the same time from developers perspective. Gladly in company I work for, we have Community of Practise so with my colleague we’ve decided to make similar show about hacking Android apps for others during next CoP meeting. I’ve extended a bit things that Michał showed at Sekurak meeting and it took me some time to find them on various blog posts or Youtube videos, so I’d like to share.
Preparation
Even if Frida is pretty easy to use, there are some steps you will need to take to make it work.
Getting ready
- python installed — I’ve got 2.7 and it works just fine, not sure if there are any issues with Python 3.x
- pip installed (its now bundled with Python distributions)
- reasonable console — if you are on Linux or Mac you already have one, for Windows…I use ConEmu with git bash commands installed
- ADB working from console — you already have ADB installed with Android Studio (well Android SDK to be accurate), but if you haven’t been using separate console app it’s possible that it’s not added to PATH
phone
- Frida works on Android OS between 4.2 and 6
- it needs to use Dalvik, not ART
- it should be rooted — well… there is a way to avoid this but I did not check it.
To achieve it all pretty easly and cheap, I just used emulator 🙂 with following details:
- you need to know what architecture your Android device, for my emulator it’s x86
- if you already have neat console app, it would be super cool to know how to use it
- also basics of Python and JavaScript will help — if you know ANY other language it will be just enough, we wont be making enterprise scale banking app, just simple hacking scripts
Installing stuff
To install Frida on your PC just go to console and type pip install frida
Now we’d like to send frida-server to our device and run it, so Frida on our PC can communicate with it. On GitHub release page are versions for all possible uses (also Windows or OSX), but we are hacking Android so we need to find frida-server-10.7.7-android-x86.xz or newer, but always exactly for our device architecture. Now unpack the archive and send frida-server file to your device using: adb push
- adb shell will get us to device shell
- cd /data/local/tmp will take us to where we’ve send frida-server
- (optional) mv
frida-server to change file name for easer to use, without version and architecture name - chmod 755 frida-server to change permissions
- ./frida-server to finally run it
Notice that you wont get any info in console, it will just start running. Every other command should be run from separate terminal. It’s also a good idea to open logcat in separate terminal adb logcat .
Hello Frida
We are all good to go 🙂 Let’s check if Frida on PC is getting along with Frida-server on device: frida -U asvid.github.io.fridaapp — It’s necessary to know full app package name, and to have app running on device. Flag -U tells Frida to check the USB connected device, or in my case, Android emulator.
Console should now look like that:
We are officially in. Now we can type commands here and our app should obey. Lets just do something simple: Java.androidVersion will just return in console which Android is our device running. Pretty…lame. Lets run something better: Java.perform(function()
Action
Running frida commands in console is a bit annoying, it’s extremely easy to mistype or forget to close some braces. Other way is to write script to file and run it by Frida. frida -U -l script.js asvid.github.io.fridaapp It can be even better with Python script that will run JavaScript script. Why we need Python and JavaScript if we want to hack app written in Java or Kotlin compiled to bytecode and that runs on Dalvik Virtual Machine? Well Python is just to make it easer to run JavaScript files, that will fool Dalvik to run them instead of app instructions.
I’ve made very simple app for hacking with Frida demonstration that is available here. There is signing key provided so you can build yourself a signed release APK, but since it’s not obfuscaded in anyway by ProGuard hacking scripts will work the same as on debug version. In tools directory we have dex2jar and jd-gui that we wont be using this time, but they are worth checking if you like to hack APK without having it’s code. For now all we are interested about is in frida-server directory.
If we look into script.py we can see that it does similar thing as we did in console, it looks for pid for our app package and attatches JavaScript file to run with it. It also have all JavaScript files already listed, we will go through all of them. To run this script just type python script.py .
Change method implementation
First script shows how we can change method implementation. Sample app is running method sum() every second and loggs output. We can change it’s implementation without app even noticing it 🙂 In change_method.js file in Java.perform() block we first find class that contains sum() method — we have whole app project so it’s not hard to find methods and classes, but if we want to hack someone’s APK, even after obfuscating with Proguard it works the same way. APK can be extracted with dex2jar tool. Java.use() returns us class object with access to it’s variables and methods (note that it is NOT an instance of this class). To change method implementation we just need to overwrite it with new method.
Interesting thing is that we can still use this.sum() — it’s because we haven’t change original method or class, we just told Dalvik to run our JavaScript instead. In this case we are printing in console original method parameters and then run it with completely others, and return value. At this point I felt absolute power!
Run method
We’ve changed method implementation, but we still needed app to run method, it’s because we didn’t have access to actual object. But we can have it, why not, we are world class hackers at this point. In file instance.js we use a bit different method Java.choose() that looks for loaded objects and select one with fitting name.
Method takes two callbacks: called when instance is found and other called when method is completed. In first callback we get access to instance of class we were looking for, and we can call it’s methods. Remember that it means method will be called when instance is found, not at start of your app, because looking for instances takes a while. So YAY! we’ve showed a toast.
Bruteforce PIN breaking
In some apps like Evernote you can set internal PIN to protect your data from unwanted access. It means PIN has to be stored locally on your device, encrypted of course and hashed. When user provides PIN you just compare hashes, so no plain text PIN is available at any point. In FridaApp I’ve provided just simple method that checks if PIN is “1234”, but image that its reading hash from SharedPreferences and compares it with hashed user input. No matter what security precautions you take, at the end of a day you want method that takes a String and returns a Boolean . Lets hack it! In brutal.js we have our PIN destroyer. At first we need instance of class that contains PIN checking method. Than we can run this method for diferent PIN numbers and check which one returns true . I’ve done it in a loop that iterates from 0 to 100000, so it covers all 5 digit PIN numbers. Loop stopes when method returns true and prints number in console along with time it took.
Listing loaded objects
We’ve already done this in console, but there we’ve go ALL of objects, it was impossible to find what we can hack. Gladly I’ve wrote class_list.js script that can list only ones in my app.
Yes in console you can use | grep asvid but its usefull to do it inside script in case you would need to use it further.
Imaginary Security
All previous scripts were working arount MainActivity class or instance, it’s safe to assume 99% of apps has such class. But now since we’ve listed loaded objects we can see there is mysterious Security object loaded. If we check app code, we can see its a field in MainActivity and its used to encode text from input and stores it in SharedPreferences . It’s also used to read and decode this text that is next printed below input. If you check SharedPreferences of sample app it might contain something like that:
Looks serious, but why even bother cracking it when we can read it like it wasn’t even encoded? In script security.js I’m using some old tricks: Java.choose() to find instance of Security class, and running method getPassword() on found instance.
Let there be instance
In sample app there is one class left — SomeClass . But it wasn’t listed on loaded classes, in Android Studio its name is gray so it’s not being used anywhere. Is there a way to use it somehow? Yeap, we just need to create instance of it. There is a log of code in some_class.js script but most important is this:
So here I’m getting a class that I want to create instance of, and just… create an instance. And now I can do whatever I want with this instance. At first script is just printing in console output from methods with same name but different signatures — easy. Then it’s changing both implementations with help of overload() method, because we need to specify which ones implementation we are changing. Finally, script is printing values in public and private field of our SomeClass instance. Private doesn’t really mean anything for us now, script will change its value (which was also final ) to anything we order it.
Debug release
Last script is inspired by silly idea, that developers can hide things from users simply checking if build is debug or release . Like additional buttons used for testing, app logic changes or logging. Remember that in MainActivity there is a method that runs every second and prints in console result of adding 30 and 50, we were changing this method implementation before. This method uses two types of logging, standard Log.d() and Logger.log() . This second method is checking build type, and prints only for debug . So if you build release app you will see only first log. Script debug.js is at first looking for Logger instance in memory, and then changes its showLogs flag to true , from its original value of kinda isDebug() . And now we get both logs in logcat.
Summarization
I’ve tried to show some basic functions of Frida with easy to use scripts. Hope you had fun and will experiment on your own apps, I surely will. Real world app would have obfuscated code, so it will be much harder to know which class and method you need to use to achieve what you want, but it will still work the same way. I’m just an Android developer — not really a hacker, or security guru, but learning about Frida pushed me to think way more about my apps security. It’s always better to break (and fix) your own app before someone else does it.
Источник