- Kraken V2 Android Banking RAT
- Librax
- gabije2290
- bumugipap
- Ishivagowd
- Tima_767
- Tima_767
- Rryba59
- jadihas170
- Kraken V2 Android Banking RAT
- bilalkhanicom
- Kraken v2 android banking rat
- About Kraken 2
- Kraken 2 and Other Tools
- Authors/Contributors
- Kraken V2 Android Banking RAT
- Kraken v1.5 Unleashed
- Read Me — The Manual — How To.
- Terms & Conditions
- Download & Install Kraken
- Preparations.
- Unleash the Kraken!
- Bruteforce
- Dictionary Method
- Recovery Speed
- Autosave progress & Continue
- Password Backup
- Extract Recovererd Files
- Prefix and Suffix
Kraken V2 Android Banking RAT
Librax
Registered User
gabije2290
Registered User
bumugipap
Registered User
Ishivagowd
Registered User
Tima_767
Registered User
Tima_767
Registered User
Rryba59
Registered User
jadihas170
Registered User
NEW YEAR 2022 TRANSFER DISCOUNTS DEALS AVAILABLE
300$ FOR 2500$
400$ FOR 4500$
500$ FOR 6000$
850$ FOR 12000$
1,600$ Transfer = 250$ Bitcoins.
2,000$ Transfer = 300$
3,000$ Transfer = 350$
4,000$ Transfer = 400$
5,000$ Transfer = 500$
6,000$ Transfer = 600$
8,000$ Transfer = 800$
9,000$ Transfer = 850$
Note: Im doing local/domestic and international Cashapp Transfer.
Local transfers are instant and take only couple of hours but international transfers take 12 hours to 72 hours max.
We use hacked Cashapp accounts to transfer money into your accounts,
this is best if you have a Cashapp account on fake info then you cant get track.
1,600$ Transfer = 250$
2,000$ Transfer = 300$
3,000$ Transfer = 350$
4,000$ Transfer = 400$
5,000$ Transfer = 500$
6,000$ Transfer = 600$
8,000$ Transfer = 800$
9,000$ Transfer = 850$
I will only need your paypal email address.
For example if you ordered $2000 transfer then i will send you $2000 into 3 or 4 parts like $800+$200+$600+$400 = $2000
it is because i send a single transaction of $2000 from a single account then it will show fishy to paypal agents
and they will block the transaction immediately and also there is transfers limits issue in many accounts.
-Available Paypal Accounts For Countries Mentioned Below
(US/CA/UK/FR/GR/IN/RU/AU/BR/IT/ES)
1,600$ Transfer = 250$
2,000$ Transfer = 300$
3,000$ Transfer = 350$
4,000$ Transfer = 400$
5,000$ Transfer = 500$
6,000$ Transfer = 600$
8,000$ Transfer = 800$
9,000$ Transfer = 850$
Note: Only 1 time transfer on 1 name in a week , if you need daily transfers then you must have to use more names .
Prepaid Cards (Visa — Mastercard — American Express) :-
These cards are not associated with a bank account or person and are therefore considered the safest cards to use. These cards costs are a little more expensive than cloned cards because we’ve already clearing a clone card and transferring money to a prepaid card. With this card you can enjoy all the possibilities of use (shopping in stores and withdrawals) along with peace of mind.
Источник
Kraken V2 Android Banking RAT
bilalkhanicom
New member
Kraken V2 Android Banking RAT
The description is not complete as the bot was finished by itself
Send SMS — send SMS with the specified text to the number specified in the command;
Start USSD — execute a USSD request;
Start Application — launch the application specified in the command;
Replace URL Admin Panel / Forwarding — change the address of the managing server;
Get All SMS — send copies of SMS stored on the device to the managing server;
Get All Installed Applications — get information about installed applications;
Get All Permissions — check the availability of additional permissions to work;
Get Logs Keylogger — start intercepting keystrokes;
Show Message Box — show the dialog box with the text specified in the command;
Show Push Notification — show push notifications whose contents are specified in the command;
Show Automatically Push Notification — show a push notification whose content is specified in the Trojan’s code;
Start Fake-Locker — block the device screen by the WebView window, which will show the contents of the web page specified by the server;
Get Numbers From Phone Book — transfer all numbers from the phone book to the server;
Sending SMS to your Contacts — send SMS to all contacts from the phone book;
Request Permission For Injection — request permission to access data;
Request Permission For Geolocation — request permission to determine the location of the device;
Start Accessibility Service — request access to accessibility features;
Start Permission — request access to additional permissions;
Start Forward Calls — start forwarding calls to the number specified by the attackers;
Stop Forward Calls — stop call forwarding;
Open Link in Browser — open the specified link in the browser;
Open Link in Activity — open a link to a web page in a WebView;
CryptoLocker — encrypt files stored on the device and show a message with a ransom request;
Decrypt File System — decrypt files;
Record Sound — start recording the environment using the microphone built into the device;
Get IP Bot — determine the IP address of the device;
Kill Bot — clear the Trojan’s configuration file and stop the malicious application.
Kraken,Kraken rat,how to use kraken rat,how to setup Kraken rat,how to config Kraken,how to install Kraken,how to hack android,how to hack android phone,how to steal android phone,
Источник
Kraken v2 android banking rat
Please Refer to the Kraken 2 Github Wiki for all updates moving forward. We are in the process of moving all relevant information/links to the Github Wiki page. Thank you for your patience.
As of September 2020, we have created a Amazon Web Services site to host many of the most widely-used Kraken2 indices, available at https://github.com/BenLangmead/aws-indexes.
KrakenTools is a suite of scripts to assist in the analysis of Kraken results. KrakenTools is an ongoing project led by Jennifer Lu. Please see the KrakenTools webpage for more details.
About Kraken 2
Kraken 2 is the newest version of Kraken, a taxonomic classification system using exact k-mer matches to achieve high accuracy and fast classification speeds. This classifier matches each k-mer within a query sequence to the lowest common ancestor (LCA) of all genomes containing the given k-mer. The k-mer assignments inform the classification algorithm. [see: Kraken 1’s Webpage for more details].
Kraken 2 provides significant improvements to Kraken 1, with faster database build times, smaller database sizes, and faster classification speeds. These improvements were achieved by the following updates to the Kraken classification program:
- Storage of Minimizers: Instead of storing/querying entire k-mers, Kraken 2 stores minimizers (l-mers) of each k-mer. The length of each l-mer must be ≤ the k-mer length. Each k-mer is treated by Kraken 2 as if its LCA is the same as its minimizer’s LCA.
- Introduction of Spaced Seeds: Kraken 2 also uses spaced seeds to store and query minimizers to improve classification accuracy.
- Database Structure: While Kraken 1 saved an indexed and sorted list of k-mer/LCA pairs, Kraken 2 uses a compact hash table. This hash table is a probabilistic data structure that allows for faster queries and lower memory requirements. However, this data structure does have a
Kraken 2 and Other Tools
The following tools are compatible with both Kraken 1 and Kraken 2. Both tools are designed to assist users in analyzing and visualizing Kraken results.
Bracken allows users to estimate relative abundances within a specific sample from Kraken 2 classification results. Bracken uses a Bayesian model to estimate abundance at any standard taxonomy level, including species/genus-level abundance.
Pavian has also been developed as a comprehensive visualization program that can compare Kraken 2 classifications across multiple samples.
KrakenTools is a suite of scripts to assist in the analysis of Kraken results. KrakenTools is an ongoing project led by Jennifer Lu.
Authors/Contributors
For technical issues, bug reports, and code contributions, please use Kraken2’s GitHub repository.
Источник
Kraken V2 Android Banking RAT
The description is not complete as the bot was finished by itself
Send SMS — send SMS with the specified text to the number specified in the command;
Start USSD — execute a USSD request;
Start Application — launch the application specified in the command;
Replace URL Admin Panel / Forwarding — change the address of the managing server;
Get All SMS — send copies of SMS stored on the device to the managing server;
Get All Installed Applications — get information about installed applications;
Get All Permissions — check the availability of additional permissions to work;
Get Logs Keylogger — start intercepting keystrokes;
[banner_200x200]
[/banner_200x200]
Show Message Box — show the dialog box with the text specified in the command;
Show Push Notification — show push notifications whose contents are specified in the command;
Show Automatically Push Notification — show a push notification whose content is specified in the Trojan’s code;
Start Fake-Locker — block the device screen by the WebView window, which will show the contents of the web page specified by the server;
Get Numbers From Phone Book — transfer all numbers from the phone book to the server;
Sending SMS to your Contacts — send SMS to all contacts from the phone book;
Request Permission For Injection — request permission to access data;
Request Permission For Geolocation — request permission to determine the location of the device;
Start Accessibility Service — request access to accessibility features;
Start Permission — request access to additional permissions;
Start Forward Calls — start forwarding calls to the number specified by the attackers;
Stop Forward Calls — stop call forwarding;
Open Link in Browser — open the specified link in the browser;
Open Link in Activity — open a link to a web page in a WebView;
CryptoLocker — encrypt files stored on the device and show a message with a ransom request;
Decrypt File System — decrypt files;
Record Sound — start recording the environment using the microphone built into the device;
Get IP Bot — determine the IP address of the device;
Kill Bot — clear the Trojan’s configuration file and stop the malicious application.
Источник
Kraken v1.5 Unleashed
Free RAR, ZIP, 7-Zip and Hash password recovery tool for Windows. No trial, no limits!
Read Me — The Manual — How To.
Terms & Conditions
Kraken is free to use and is provided ‘as-is’, without any express or implied warranty. By using Kraken, you agree to NOT use this software for illegal activities.
You also agree to take FULL responsibility and that the author of this program, IN NO EVENT will be held liable for any damage arising from the use of this software.
- Windows with .NET 4.7.1 (no need for Windows 10 users)
Back to top
Download & Install Kraken
— Holy Crack, Batman!
Kraken is packed into a self-extracting archive, just download, extract and unleash!
- Download Kraken v1.5
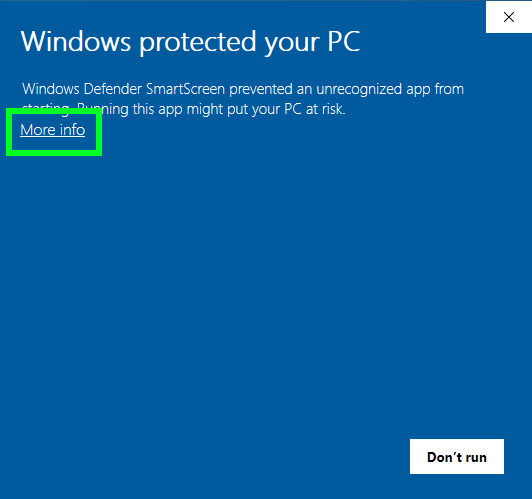
- Run Kraken_v1.5.exe and select «More info» then click «Run anyway» in the Windows Defender Smartscreen prompt.
Back to top
Preparations.
Inside the Kraken folder, there are 2 folders called «Recovery» and «Dictionary».
- Drop all your RAR/ZIP-files into the «Recovery» folder. Note: Unprotected RAR & ZIP-files will be ignored.
- Drop all dictionary.txt files into the «Dictionary» folder. (Optional).
Where to find dictionary password files? Google is your friend.
Unleash the Kraken!
- Start Kraken.exe
- Agree to the terms & conditions
- Select «Start New»
- Select wether you want to recover a RAR/ZIP file or a Hashed string. If there’s only one password protected file in the «Recovery» folder, it will be selected automatically.
- Select «Bruteforce» or «Dictionary» recovery method and follow the instructions. Back to top
Bruteforce
The Bruteforce method generates all possible combinations out of a charset and test it against the password protected file until there’s a match. This methods can take everything from a few seconds up to days, weeks, months and even years depending on the complexity of the password. The longer the password and variations and mixture of chars and symbols, the harder it is to recover.
However, if you partly remember the password, you can speed up the recovery process significantly by defining a prefix and/or suffix. More info below.
- Select «Charset» or define your own (option 9). If you define your own, type in all chars you want to be included in the Charset and press [ENTER].
- Set Password Min-length. This defines the length of the password Kraken should start with. 1 is default.
- Set Password Max-length. This defines the maximum length of the password. If nothing is specified, «Unlimited» will be set.
- Set Password Prefix. Should the password start with a fixed string of chars? Press [ENTER] to skip.
- Set Password Suffix. Should the password end with a fixed string of chars? Press [ENTER] to skip.
- Select Bruteforce speed. Press [ENTER] to start Kraken.
Dictionary Method
A dictionary is a *.txt file containing pre-defined passwords that is being tested against the protected file until there’s a match.
Where to find free dictionary files? Google is your friend 😉
Drop your dictionary *.txt file(s) into Kraken’s «Dictionary» folder.
- Select a dictionary.txt file. If there’s only one dictionary in the «Dictionary» folder, it will be selected automatically.
- Select «Recovery Speed».
- Start Kraken
Back to top
Recovery Speed
Kraken comes with 4 different speed options depending on how much of your systems resources you want Kraken to use. If you need to use your computer while Kraken is running, speeds up to mormal are recommended.
- Crawl — very slow.
- Slow
- Normal
- Fast — WARNING! Very high CPU usage!
Back to top
Autosave progress & Continue
Kraken automatically saves your recovery progress every 1000 password so you wont loose time spent trying to recover your password protected files.
To continue from where you left off, start Kraken and select «Continue» from the main menu and Kraken will load your previous configuration. Select recovery speed and start.
Password Backup
When Kraken successfully recovers a password, it will automatically be saved to «Recovered Passwords.txt» and to your clipboard so you wont loose it again 😉
Extract Recovererd Files
After a successful RAR, Zip or 7-Zip recovery, Kraken asks if you want to extract the archive. Press Y to extract or [ENTER] to exit.
You’ll find your extracted archive in a folder on your desktop with the same name as your recovered file.
Prefix and Suffix
If you know the password start with one or more chars, then use Prefix and Suffix to speed up the recovery process.
You know the password start with www. and end with .com but forgot what’s in between. Then set www. as Prefix and .com as Suffix.
Kraken will then only bruteforce what is between the Prefix and Suffix. Ex:
You know the password starts with #123 but forgot the rest, then set #123 as Prefix.
Kraken will then only bruteforce what comes after the Prefix. Ex:
You know the password ends with _ABC but forgot the rest, then set _ABC as Suffix.
Kraken will then only bruteforce what comes before the Suffix. Ex:
Источник