- How to Block Internet Access in Specific Apps on Android
- Restrict Background Data on Android Natively
- Block Mobile Data and WiFi with Third Party Apps
- NetGuard
- NoRoot Firewall
- Block Unwanted Apps From Eating Up Your Bandwidth
- Request app permissions
- Basic principles
- Workflow for requesting permissions
- Determine whether your app was already granted the permission
- Explain why your app needs the permission
- Request permissions
- Allow the system to manage the permission request code
- Kotlin
- Kotlin
- Manage the permission request code yourself
- Kotlin
- Kotlin
- Handle permission denial
- One-time permissions
- Android auto-resets permissions of unused apps
- Request to become the default handler if necessary
- Grant all runtime permissions for testing purposes
- Additional resources
How to Block Internet Access in Specific Apps on Android
A smartphone is only “smart” as long as it has an internet connection because you need a working internet network for various apps to work. However, that also means that these apps take up a lot of our internet bandwidth. And if you totally rely on mobile data for your Android smartphone and you don’t have an unlimited plan, your bandwidth should get over pretty soon. The problem is, some apps use the internet even when they are running in the background. While communication apps like WhatsApp, Messenger need to be connected to the internet all the time, other apps don’t really need to be connected always. So, if you have a limited data plan or even a broadband WiFi connection which has a monthly bandwidth limit, you should limit the internet usage of apps on your Android smartphone.
The good news is, there are ways to block internet access in specific apps on Android. You can do it through Android’s built-in options or you can use a third party app. First, let’s take a look at how you can restrict internet for specific apps on Android natively:
Restrict Background Data on Android Natively
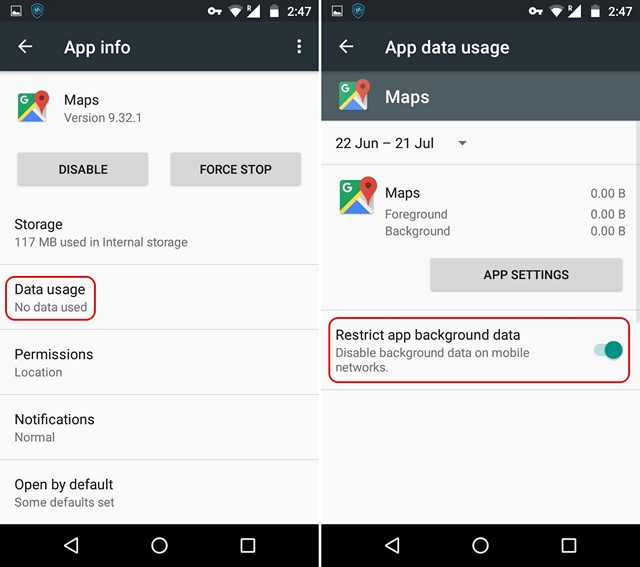
You can easily set background data restrictions for specific apps on Android. All you need to do, is head over to Settings->Apps and select the app you want to block background data for. In the App Info page, you can tap “Data usage” and here, enable “Restrict app background data”. This makes sure that the app does not fetch any mobile data while running in the background. However, if you open the app, it will use the internet.
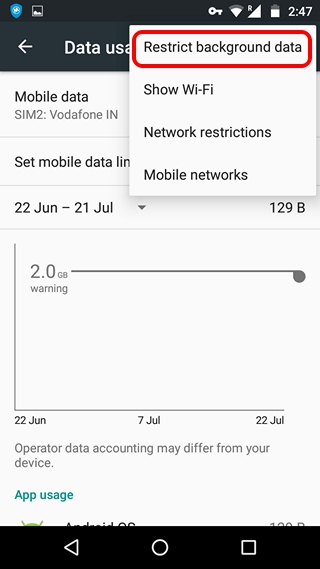
If you want to restrict background data for all the apps, you can go to Settings->Data usage, hit the three dot button and tap on “Restrict background data”. Here, you can also set a monthly mobile data limit, so that you know when your mobile data is close to getting over.
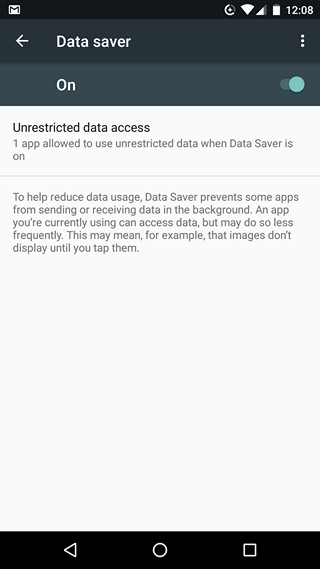
Android N includes a Data Saver mode, which basically restricts the background data on all apps. However, you can select the apps you want to enable unrestricted data access for.
While the native Android methods work fine if you are looking to only restrict usage on mobile data, there are third party apps that let you block mobile data as well as WiFi connectivity for certain apps:
Block Mobile Data and WiFi with Third Party Apps
While there are a few good apps that let you block internet for specific apps, we’ll suggest you Mobiwol because it’s free and it brings most of the features you’d need. So, install Mobiwol on your Android smartphone and follow the steps:
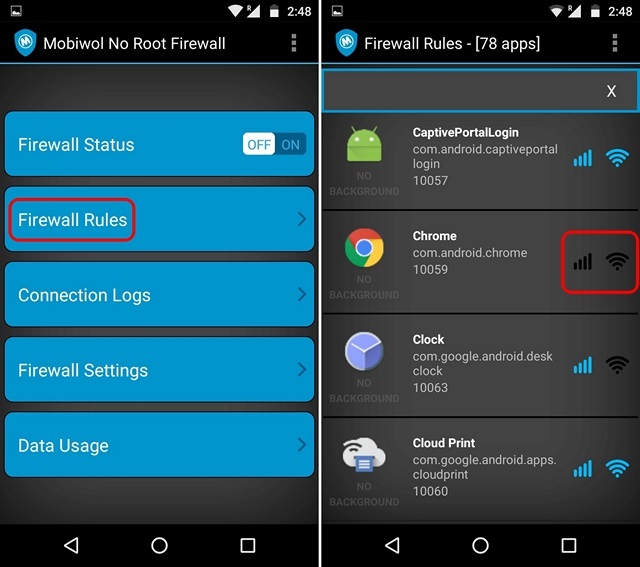
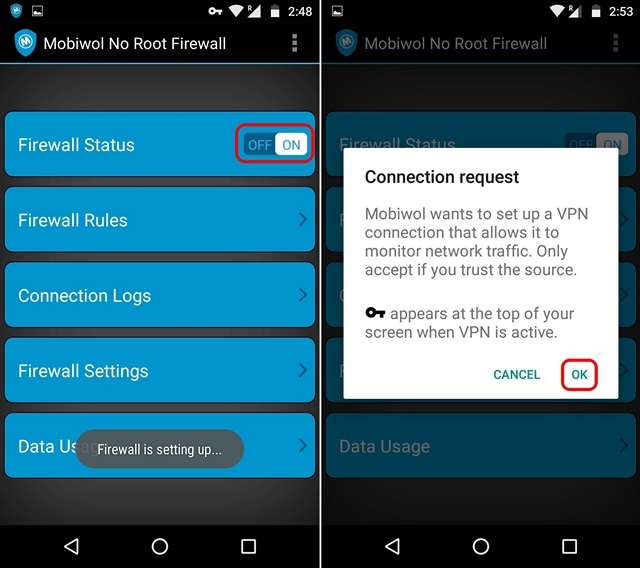
1. When you first open Mobiwol, you will see the home page of the app with its main options listed upfront. You can go to “Firewall Rules“, where you will find all the apps on your device including the system apps. You can just tap on the mobile network & WiFi icon to disable the respective connections for the app.
Note : Be careful to not block system apps because that may lead to unexpected behaviour and inconsistent performance of your device.
2. Once done, you can go back to the main page of the app and turn on “Firewall Status”. When you turn it on, the app will make a VPN connection request. Tap “Ok” and the firewall will turn on.
Note : Mobiwol and most other similar firewall apps create a VPN connection, so that they can filter the internet connection on your device to stop usage on blocked apps.
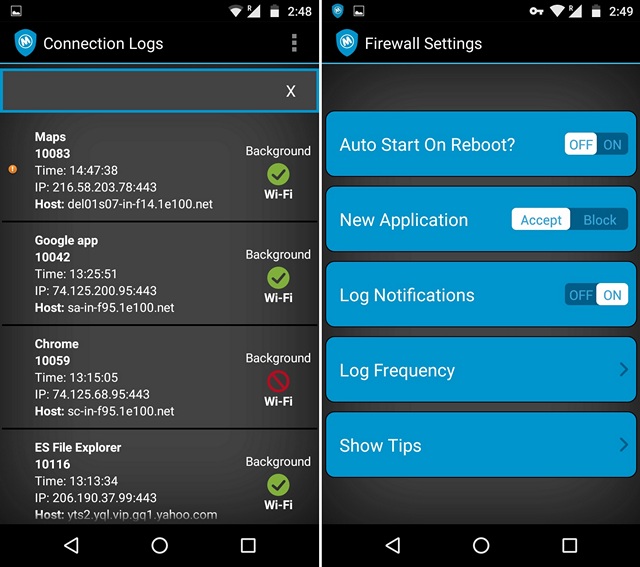
3. Then, you can try opening the blocked apps and you will see that they don’t have internet access. Mobiwol also lets you check the apps that are using the connection in the background via “Connection Logs”.
Other than that, you can check out the app settings to make sure it auto-starts on reboot, accept or block newly installed apps, get log notifications and its frequency and get tips about the app.
If you would like a more feature rich app, you can try the below mentioned apps that also let you block internet in specific apps:
NetGuard
NetGuard is another great firewall app that not only blocks internet access for specific apps but lets you use conditions like allow WiFi/mobile data when screen is on and block internet while roaming. It also supports multiple device users, tethering and more. Some would say that NetGuard is even better than Mobiwol but the problem is, NetGuard’s unique features like log out outgoing traffic, network speed, ability to block addresses etc. are available only in the paid version of the app.
Install: (Free with in-app purchases for Pro features)
NoRoot Firewall
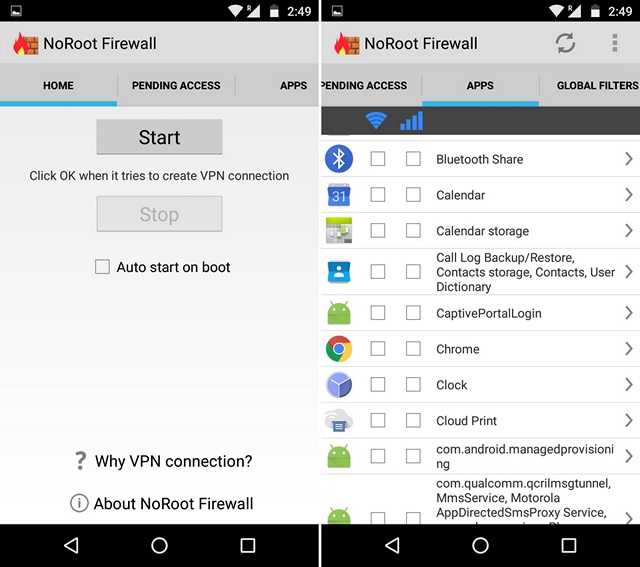
NoRoot Firewall is a highly popular firewall app that brings advanced capabilities to the table. The app not only lets you block mobile data/WiFi access for apps, it also lets you set custom filters and conditions based on IP address, domain name and host address. While the app’s interface might seem clunky, it is available for free, so you can give it a try.
Block Unwanted Apps From Eating Up Your Bandwidth
If you are okay with just restricting background data for apps, you can do it on Android easily. However, if you need to block internet access altogether for unwanted apps, you will have to rely on the aforementioned third party apps. These apps work great but the only limitation they bring is VPN, which might lower down your internet speed a bit. We have tried the apps and the decrease in the internet speed is not huge, so you can certainly use these apps. Well, try these apps and let us know how you like them in the comments section below.
Источник
Request app permissions
Every Android app runs in a limited-access sandbox. If your app needs to use resources or information outside of its own sandbox, you can declare a permission and set up a permission request that provides this access. These steps are part of the workflow for using permissions.
If you declare any dangerous permissions, and if your app is installed on a device that runs Android 6.0 (API level 23) or higher, you must request the dangerous permissions at runtime by following the steps in this guide.
If you don’t declare any dangerous permissions, or if your app is installed on a device that runs Android 5.1 (API level 22) or lower, the permissions are automatically granted, and you don’t need to complete any of the remaining steps on this page.
Basic principles
The basic principles for requesting permissions at runtime are as follows:
- Ask for permissions in context, when the user starts to interact with the feature that requires it.
- Don’t block the user. Always provide the option to cancel an educational UI flow related to permissions.
- If the user denies or revokes a permission that a feature needs, gracefully degrade your app so that the user can continue using your app, possibly by disabling the feature that requires the permission.
- Don’t assume any system behavior. For example, don’t assume that permissions appear in the same permission group. A permission group merely helps the system minimize the number of system dialogs that are presented to the user when an app requests closely-related permissions.
Workflow for requesting permissions
Before you declare and request runtime permissions in your app, evaluate whether your app needs to do so. You can fulfill many use cases in your app, such as taking photos, pausing media playback, and displaying relevant ads, without needing to declare any permissions.
If you conclude that your app needs to declare and request runtime permissions, complete these steps:
- In your app’s manifest file, declare the permissions that your app might need to request.
- Design your app’s UX so that specific actions in your app are associated with specific runtime permissions. Users should know which actions might require them to grant permission for your app to access private user data.
- Wait for the user to invoke the task or action in your app that requires access to specific private user data. At that time, your app can request the runtime permission that’s required for accessing that data.
Check whether the user has already granted the runtime permission that your app requires. If so, your app can access the private user data. If not, continue to the next step.
You must check whether you have that permission every time you perform an operation that requires that permission.
Check whether your app should show a rationale to the user, explaining why your app needs the user to grant a particular runtime permission. If the system determines that your app shouldn’t show a rationale, continue to the next step directly, without showing a UI element.
If the system determines that your app should show a rationale, however, present the rationale to the user in a UI element. This rationale should clearly explain what data your app is trying to access, and what benefits the app can provide to the user if they grant the runtime permission. After the user acknowledges the rationale, continue to the next step.
Request the runtime permission that your app requires in order to access the private user data. The system displays a runtime permission prompt, such as the one shown on the permissions overview page.
Check the user’s response, whether they chose to grant or deny the runtime permission.
If the user granted the permission to your app, you can access the private user data. If the user denied the permission instead, gracefully degrade your app experience so that it provides functionality to the user, even without the information that’s protected by that permission.
Figure 1 illustrates the workflow and set of decisions associated with this process:

Determine whether your app was already granted the permission
To check if the user has already granted your app a particular permission, pass that permission into the ContextCompat.checkSelfPermission() method. This method returns either PERMISSION_GRANTED or PERMISSION_DENIED , depending on whether your app has the permission.
Explain why your app needs the permission
If the ContextCompat.checkSelfPermission() method returns PERMISSION_DENIED , call shouldShowRequestPermissionRationale() . If this method returns true , show an educational UI to the user. In this UI, describe why the feature, which the user wants to enable, needs a particular permission.
Additionally, if your app requests a permission related to location, microphone, or camera, consider explaining why your app needs access to this information.
Request permissions
After the user views an educational UI, or the return value of shouldShowRequestPermissionRationale() indicates that you don’t need to show an educational UI this time, request the permission. Users see a system permission dialog, where they can choose whether to grant a particular permission to your app.
Traditionally, you manage a request code yourself as part of the permission request and include this request code in your permission callback logic. Another option is to use the RequestPermission contract, included in an AndroidX library, where you allow the system to manage the permission request code for you. Because using the RequestPermission contract simplifies your logic, it’s recommended that you use it when possible.
Allow the system to manage the permission request code
To allow the system to manage the request code that’s associated with a permissions request, add dependencies on the following libraries in your module’s build.gradle file:
You can then use one of the following classes:
- To request a single permission, use RequestPermission .
- To request multiple permissions at the same time, use RequestMultiplePermissions .
The following steps show how to use the RequestPermission contract. The process is nearly the same for the RequestMultiplePermissions contract.
In your activity or fragment’s initialization logic, pass in an implementation of ActivityResultCallback into a call to registerForActivityResult() . The ActivityResultCallback defines how your app handles the user’s response to the permission request.
Keep a reference to the return value of registerForActivityResult() , which is of type ActivityResultLauncher .
To display the system permissions dialog when necessary, call the launch() method on the instance of ActivityResultLauncher that you saved in the previous step.
After launch() is called, the system permissions dialog appears. When the user makes a choice, the system asynchronously invokes your implementation of ActivityResultCallback , which you defined in the previous step.
Note: Your app cannot customize the dialog that appears when you call launch() . To provide more information or context to the user, change your app’s UI so that it’s easier for users to understand why a feature in your app needs a particular permission. For example, you might change the text in the button that enables the feature.
Also, the text in the system permission dialog references the permission group associated with the permission that you requested. This permission grouping is designed for system ease-of-use, and your app shouldn’t rely on permissions being within or outside of a specific permission group.
The following code snippet shows how to handle the permissions response:
Kotlin
And this code snippet demonstrates the recommended process of checking for a permission, and requesting a permission from the user when necessary:
Kotlin
Manage the permission request code yourself
As an alternative to allowing the system to manage the permission request code, you can manage the permission request code yourself. To do so, include the request code in a call to requestPermissions() .
Note: Your app cannot customize the dialog that appears when you call requestPermissions() . The text in the system permission dialog references a permission group, but this permission grouping is designed for system ease-of-use. Your app shouldn’t rely on permissions being within or outside of a specific permission group.
The following code snippet demonstrates how to request a permission using a request code:
Kotlin
After the user responds to the system permissions dialog, the system then invokes your app’s implementation of onRequestPermissionsResult() . The system passes in the user response to the permission dialog, as well as the request code that you defined, as shown in the following code snippet:
Kotlin
Handle permission denial
If the user denies a permission request, your app should help users understand the implications of denying the permission. In particular, your app should make users aware of the features that don’t work because of the missing permission. When you do so, keep the following best practices in mind:
Guide the user’s attention. Highlight a specific part of your app’s UI where there’s limited functionality because your app doesn’t have the necessary permission. Several examples of what you could do include the following:
- Show a message where the feature’s results or data would have appeared.
- Display a different button that contains an error icon and color.
Be specific. Don’t display a generic message; instead, mention which features are unavailable because your app doesn’t have the necessary permission.
Don’t block the user interface. In other words, don’t display a full-screen warning message that prevents users from continuing to use your app at all.
At the same time, your app should respect the user’s decision to deny a permission. Starting in Android 11 (API level 30), if the user taps Deny for a specific permission more than once during your app’s lifetime of installation on a device, the user doesn’t see the system permissions dialog if your app requests that permission again. The user’s action implies «don’t ask again.» On previous versions, users would see the system permissions dialog each time your app requested a permission, unless the user had previously selected a «don’t ask again» checkbox or option.
In certain situations, the permission might be denied automatically, without the user taking any action. (Similarly, a permission might be granted automatically as well.) It’s important to not assume anything about automatic behavior. Each time your app needs to access functionality that requires a permission, you should check that your app is still granted that permission.
To provide the best user experience when asking for app permissions, also see App permissions best practices.
One-time permissions
Starting in Android 11 (API level 30), whenever your app requests a permission related to location, microphone, or camera, the user-facing permissions dialog contains an option called Only this time, as shown in Figure 2. If the user selects this option in the dialog, your app is granted a temporary one-time permission.
Your app can then access the related data for a period of time that depends on your app’s behavior and the user’s actions:
- While your app’s activity is visible, your app can access the data.
- If the user sends your app to the background, your app can continue to access the data for a short period of time.
- If you launch a foreground service while the activity is visible, and the user then moves your app to the background, your app can continue to access the data until that foreground service stops.
- If the user revokes the one-time permission, such as in system settings, your app cannot access the data, regardless of whether you launched a foreground service. As with any permission, if the user revokes your app’s one-time permission, your app’s process terminates.
When the user next opens your app and a feature in your app requests access to location, microphone, or camera, the user is prompted for the permission again.
Android auto-resets permissions of unused apps
If your app targets Android 11 (API level 30) or higher and isn’t used for a few months, the system protects user data by automatically resetting the sensitive runtime permissions that the user had granted your app. Learn more in the guide about app hibernation.
Request to become the default handler if necessary
Some apps depend on access to sensitive user information related to call logs and SMS messages. If you want to request the permissions specific to call logs and SMS messages and publish your app to the Play Store, you must prompt the user to set your app as the default handler for a core system function before requesting these runtime permissions.
For more information on default handlers, including guidance on showing a default handler prompt to users, see the guide on permissions used only in default handlers.
Grant all runtime permissions for testing purposes
To grant all runtime permissions automatically when you install an app on an emulator or test device, use the -g option for the adb shell install command, as demonstrated in the following code snippet:
Additional resources
For additional information about permissions, read these articles:
To learn more about requesting permissions, download the following sample apps:
- Android RuntimePermissionsBasic Sample Java | Kotlin
Content and code samples on this page are subject to the licenses described in the Content License. Java is a registered trademark of Oracle and/or its affiliates.
Источник