- See and remove your devices that are associated with Apple ID purchases
- Use a Mac or PC to see or remove your associated devices
- Remove your associated iPhone, iPad, or iPod touch
- More about associated devices
- Check your Apple ID device list to see where you’re signed in
- See where you’re signed in
- Use your iPhone, iPad, iPod touch, or Apple Watch to see where you’re signed in
- Use your Mac to see where you’re signed in
- Use your PC to see where you’re signed in
- Use the web to see where you’re signed in
- Add a device to the list
- Remove a device from the list
- Use your iPhone, iPad, or iPod touch to remove a device
- Use your Mac to remove a device
- Use your PC to remove a device
- Use the web to remove a device
- Permanently remove a device from your account page
- Use Apple products on enterprise networks
- Apple Push Notifications
- Device setup
- Device Management
- Apple School Manager and Apple Business Manager
- Apple Business Essentials device management
- Software updates
- macOS, iOS, and tvOS
- App Store
- Carrier updates
- Content caching
- Apple Developer
- Feedback Assistant
- Apple diagnostics
- Domain Name System resolution
- Certificate validation
- Apple ID
- iCloud
- Additional content
- Firewalls
- HTTP proxy
See and remove your devices that are associated with Apple ID purchases
Manage the list of devices that can download and play items that you bought with your Apple ID.
When you subscribe to Apple services or buy content from Apple, the device that you’re using becomes associated with your Apple ID. You might want to remove an associated device in these situations:
- If you reach your limit of associations and want to add a new one.
- If you can’t redownload purchases from the App Store, Apple TV app, the iTunes Store, and other Apple services.
- If you want to sell or give away an associated device.
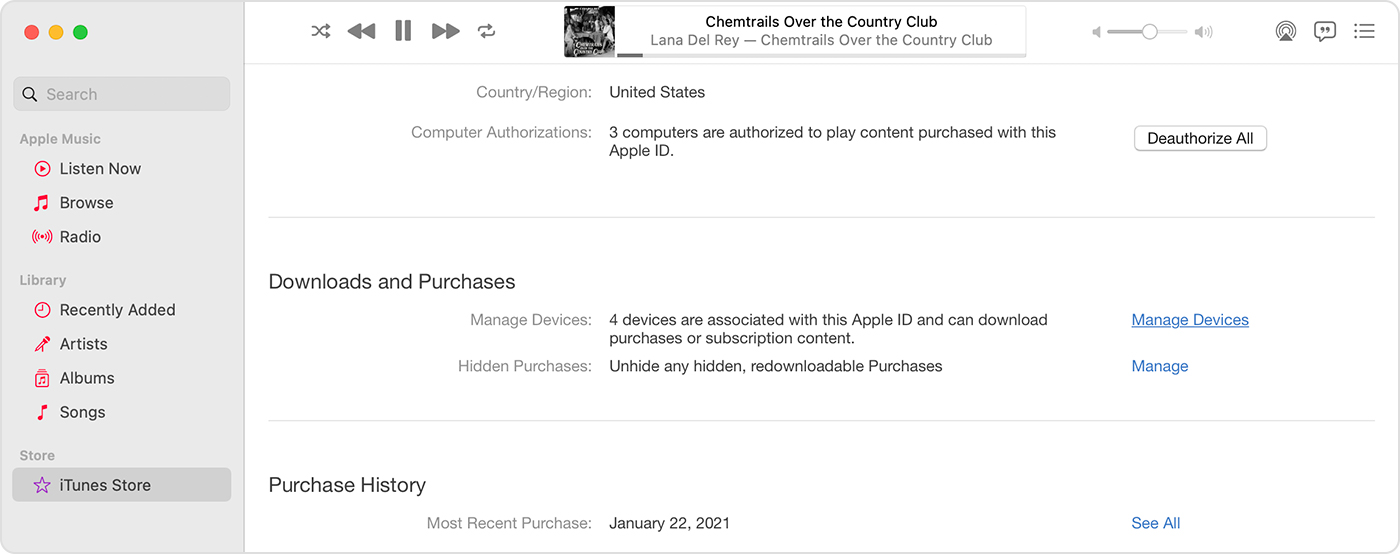
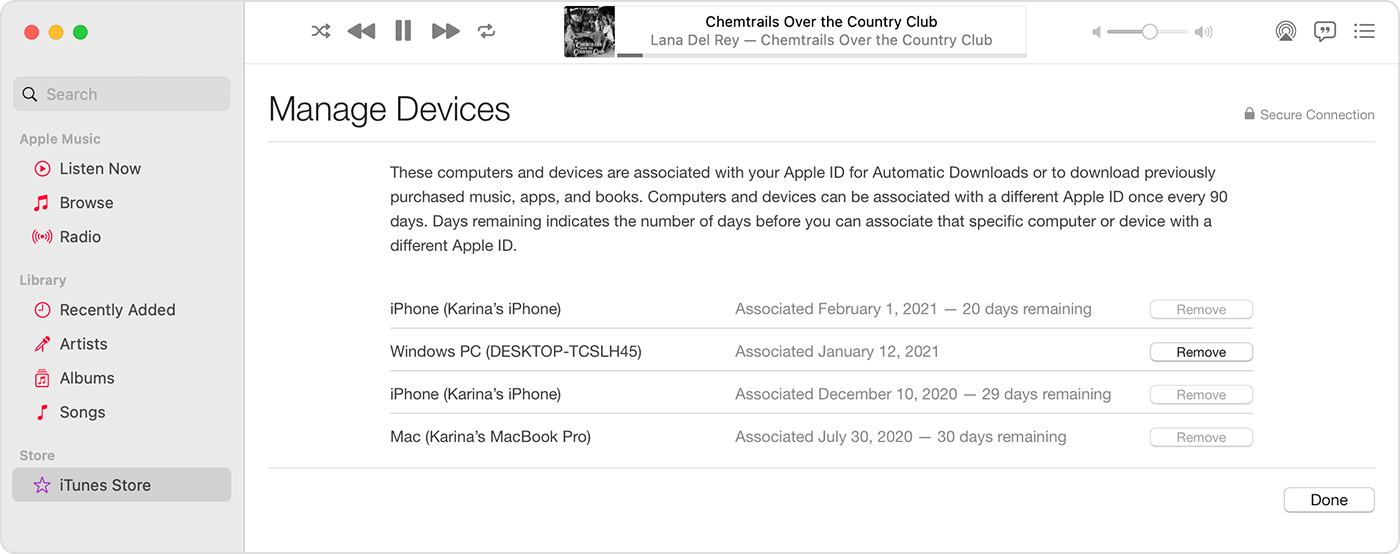
Use a Mac or PC to see or remove your associated devices
- On your Mac, open the Apple Music app. Or on your PC, open iTunes for Windows.
- From the menu bar, choose Account > View My Account. You might need to sign in with your Apple ID.
- Click Manage Devices. If no devices are associated with your Apple ID, you won’t see this section.
- If you want to remove a device, click Remove. If you can’t remove a device, sign out of your Apple ID on that device and try again. If you still can’t remove it, you might need to wait up to 90 days to associate the device with a different Apple ID.
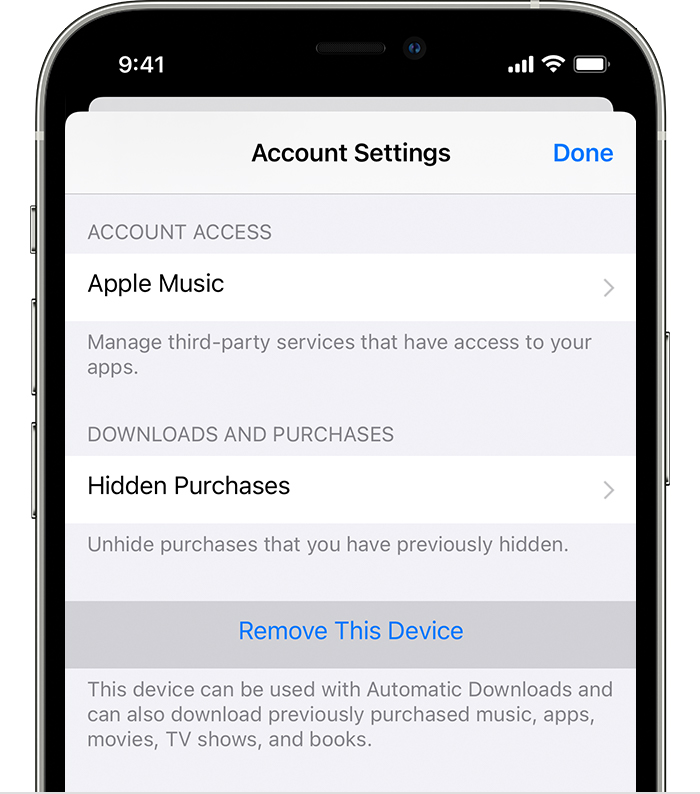
Remove your associated iPhone, iPad, or iPod touch
- Tap Settings, tap your name, then tap Media & Purchases.
- Tap View Account.
- Scroll down, then tap Remove This Device.
More about associated devices
You can have ten devices (no more than five computers) associated with your Apple ID for purchases at one time.
When you try to associate a device that was previously associated, you might see a message that says, «This device is associated with another Apple ID. You cannot associate this device with another Apple ID for [number] days.» You might need to wait up to 90 days to associate the device with a different Apple ID.
This list of associated devices is not the same as the list of devices that you’re currently signed in to with your Apple ID. You can see where you’re signed in on your Apple ID account page.
Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. Apple assumes no responsibility with regard to the selection, performance, or use of third-party websites or products. Apple makes no representations regarding third-party website accuracy or reliability. Contact the vendor for additional information.
Источник
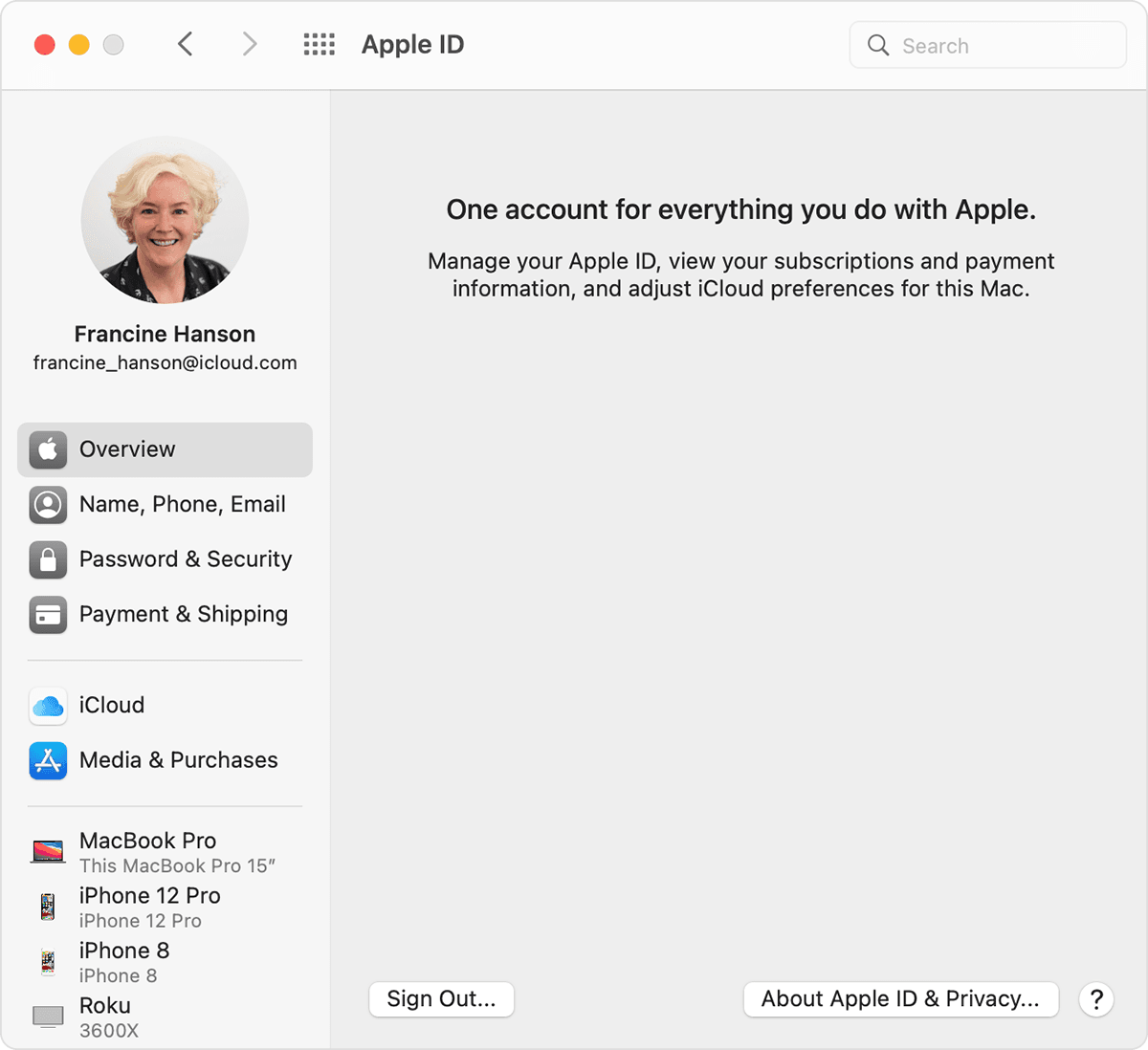
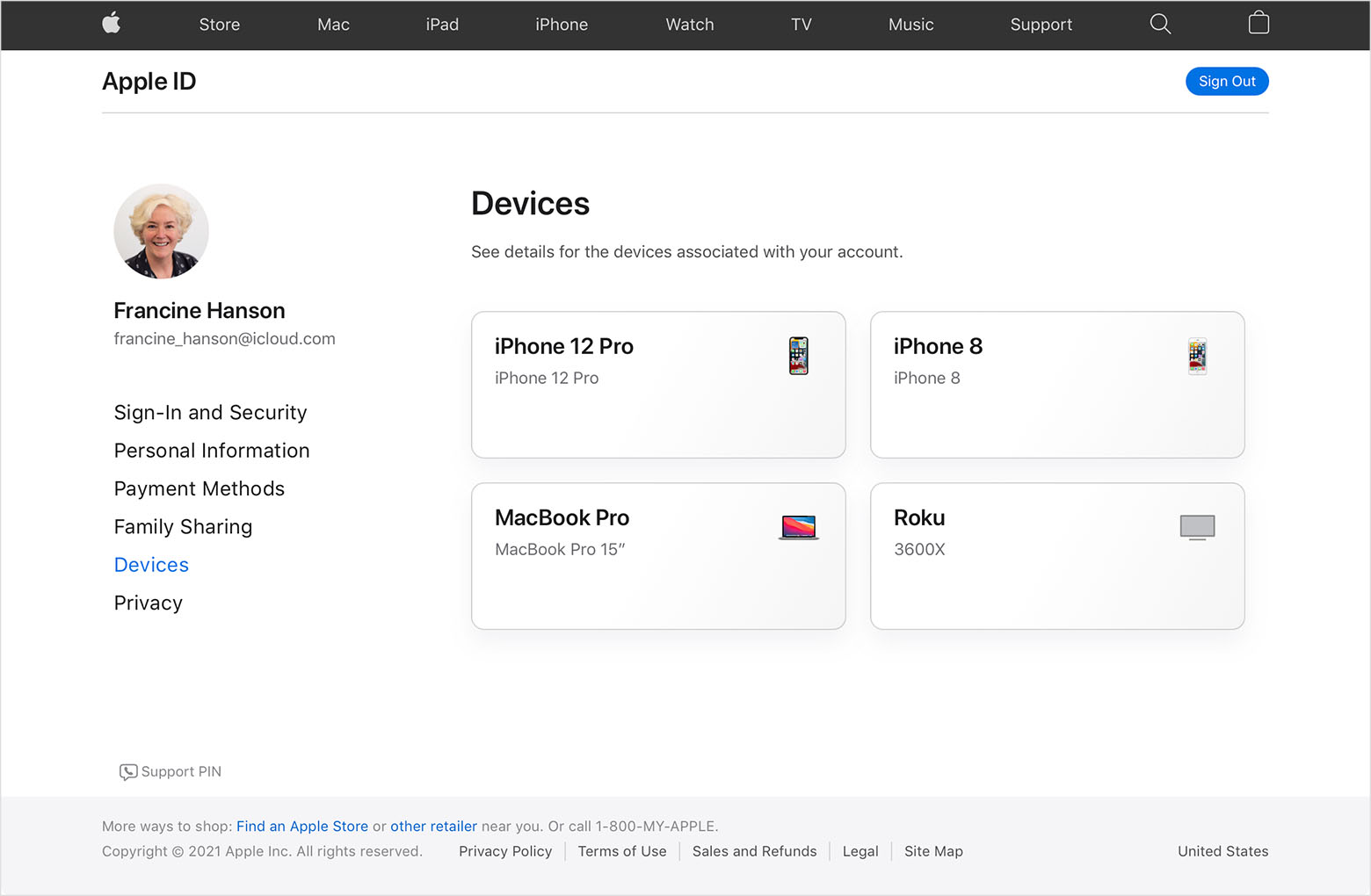
Check your Apple ID device list to see where you’re signed in
Learn which devices appear in your Apple ID device list, how to see your device’s details, and how to remove a device, if necessary.
See where you’re signed in
Use the steps below to see the devices that you’re currently signed in to with your Apple ID.
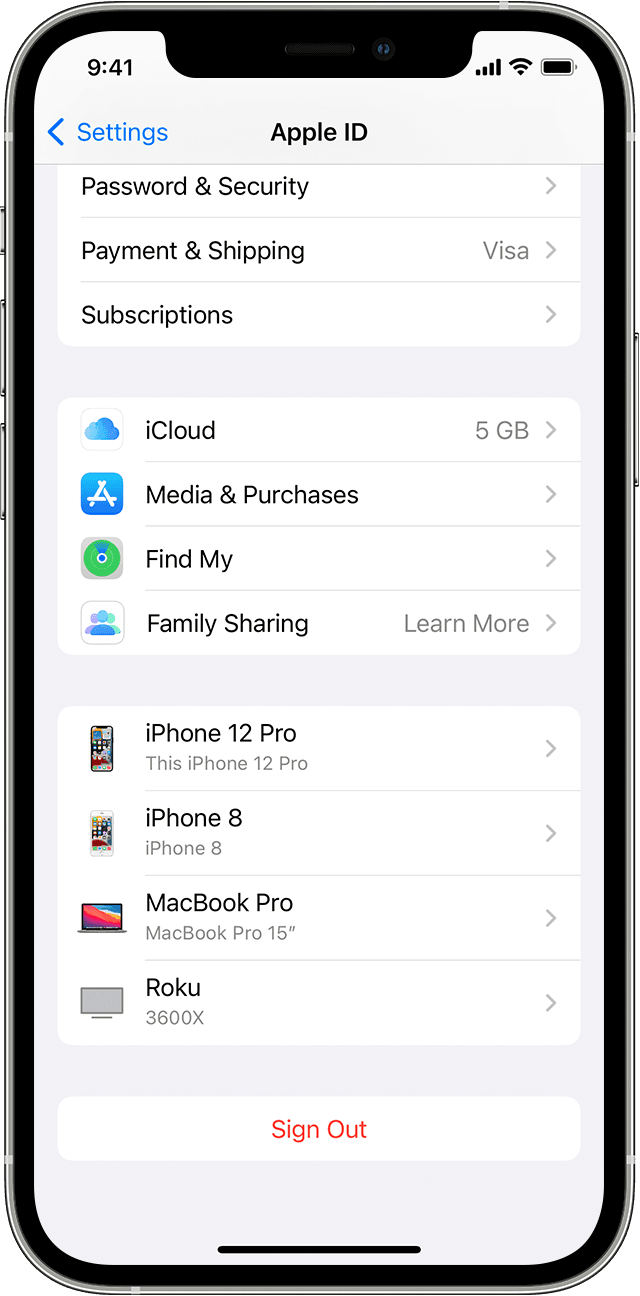
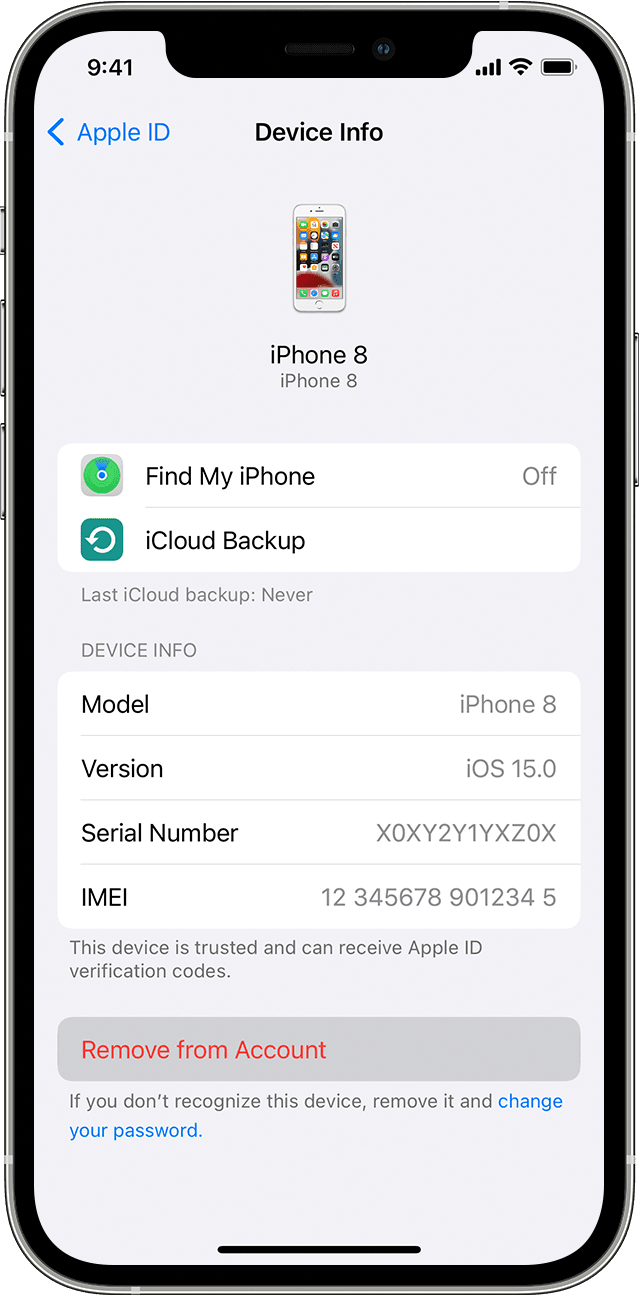
Use your iPhone, iPad, iPod touch, or Apple Watch to see where you’re signed in
- Tap Settings > [your name], then scroll down.
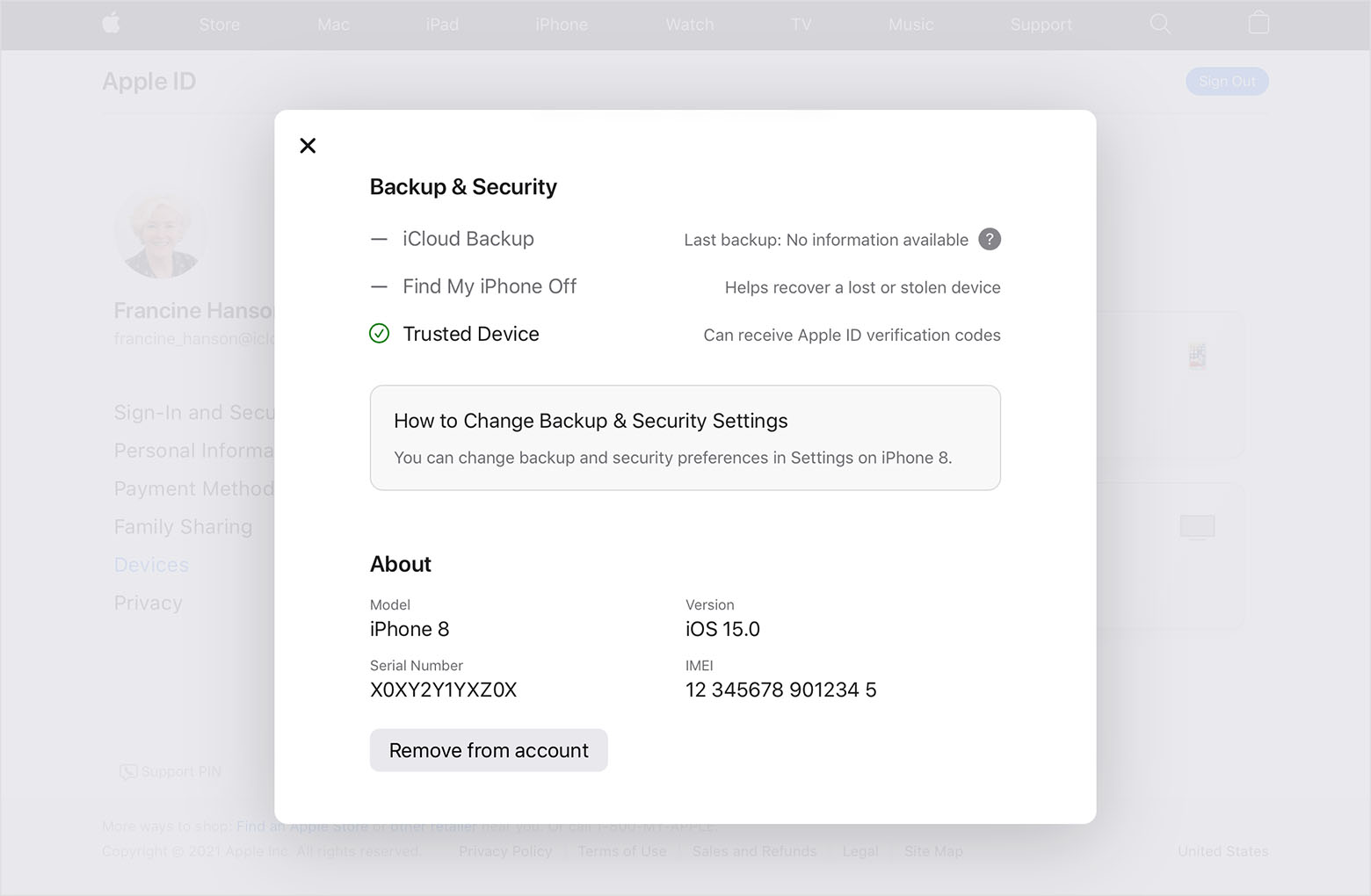
- Tap any device name to view that device’s information, such as the device model, serial number, OS version, and whether the device is trusted and can be used to receive Apple ID verification codes. The information might vary depending on the device type. You might need to answer your security questions to see device details.
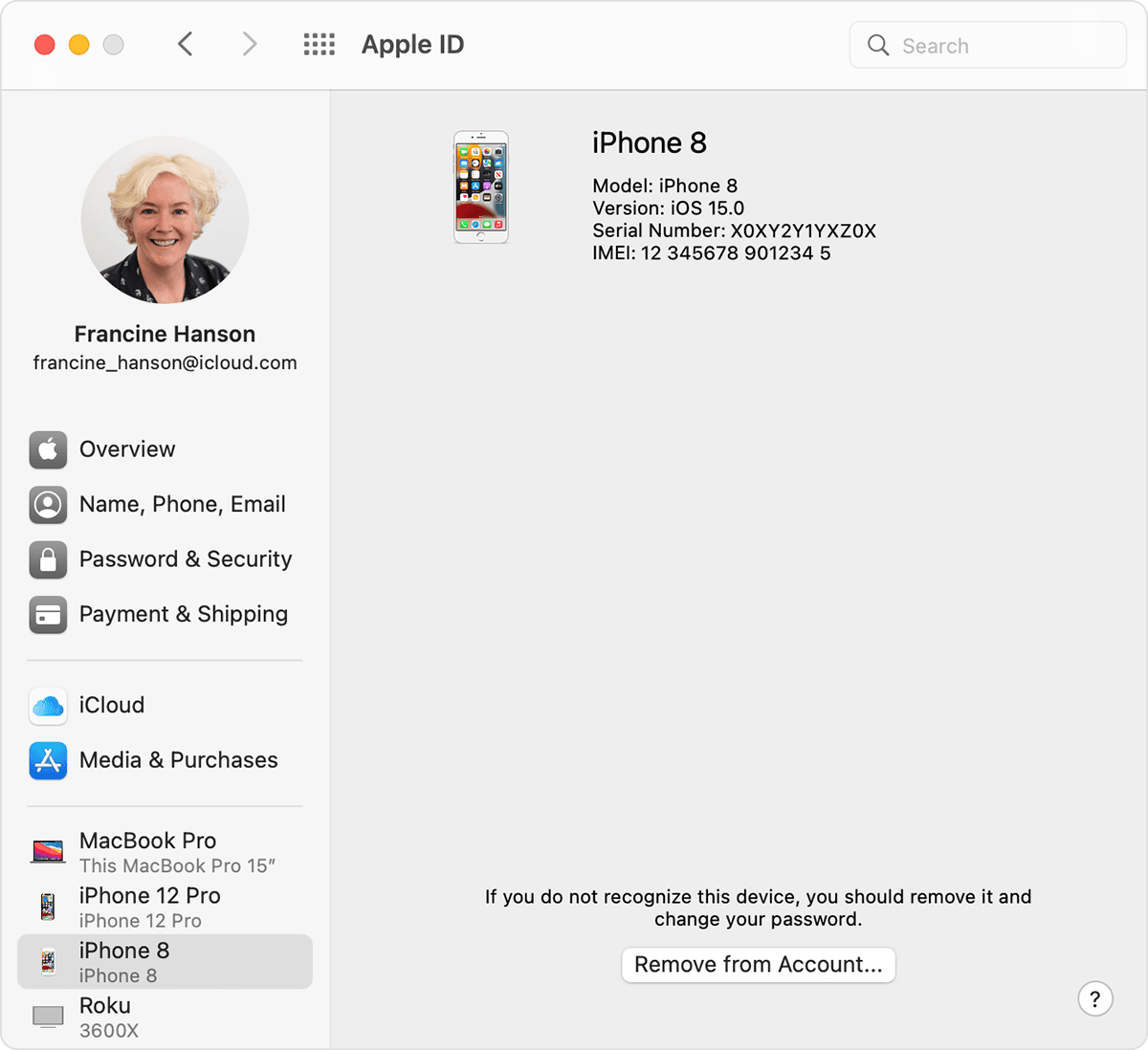
Use your Mac to see where you’re signed in
- Choose Apple menu > System Preferences.
- Click Apple ID.
- Click any device name to view that device’s information, such as the device model, serial number, and OS version. The information might vary depending on the device type. You might need to answer your security questions to see device details.
Use your PC to see where you’re signed in
- Open iCloud for Windows.
- Click Account Details, then click Manage Apple ID.
- Click any device name to view that device’s information, such as the device model, serial number, and OS version. The information might vary depending on the device type.
Use the web to see where you’re signed in
From the Devices section of your Apple ID account page, you can see all of the devices that you’re currently signed in to with your Apple ID, including Android devices, consoles, and smart TVs:
- Sign in to appleid.apple.com,* then select Devices.
- If you don’t see your devices right away, click View Details and answer your security questions.
- Click any device name to view that device’s information, such as the device model, serial number, and OS version. The information might vary depending on the device type.
* Depending on how you created your Apple ID, you might be required to provide additional information.
Add a device to the list
To add a device to the list, you need to sign in with your Apple ID. After you sign in on a device with your Apple ID, that device appears in the list. Here’s where you need to sign in:
- For iOS or iPadOS, sign in to iCloud, iMessage, FaceTime, iTunes & App Stores, or Game Center on the device. You can also see your paired Apple Watch.
- For macOS or Windows 10 and later, sign in to iCloud on the device.
- For Apple TV HD and later, sign in to the iTunes and App Store on the device.
- For Apple TV (3rd generation) and earlier, sign in to the iTunes Store on the device.
Your AirPods will appear in the Find My app, but they won’t appear in your Apple ID device list. You can remove your AirPods from your account using Find My. Devices running iOS 7 or earlier or OS X Mavericks or earlier won’t appear in your device list.
Remove a device from the list
If your device is missing, you can use Find My to find your device and take additional actions that can help you recover it and keep your data safe. If you aren’t using your device anymore, or if you don’t recognize it, you might want to remove it from the list.
If you set up two-factor authentication for your Apple ID, removing a device will ensure that it can no longer display verification codes. It also won’t have access to iCloud and other Apple services, including Find My, until you sign in again with two-factor authentication. The device won’t reappear in the list unless you sign in again.
Use your iPhone, iPad, or iPod touch to remove a device
- Tap the device to see its details, then tap Remove from Account.
- Review the message that appears, then tap again to confirm that you want to remove the device.
- Want to permanently remove the device from your account page?
Use your Mac to remove a device
- Choose Apple menu > System Preferences.
- Click Apple ID.
- Click the device to see its details, then click Remove from Account.
- Review the message that appears, then click again to confirm that you want to remove the device.
- Want to permanently remove the device from your account page?
Use your PC to remove a device
- Open iCloud for Windows.
- Click Account Details, then click Manage Apple ID.
- Click the device to see its details, then click Remove from Account.
- Review the message that appears, then click again to confirm that you want to remove the device.
- Want to permanently remove the device from your account page?
Use the web to remove a device
- Sign in to appleid.apple.com, then select Devices.
- Click the device to see its details, then click «Remove from account.»
- Review the message that appears.
- Click again to confirm that you want to remove the device.
- Want to permanently remove the device from your account page?
Permanently remove a device from your account page
If you’re still signed in with your Apple ID on the device, it might reappear on your account page the next time your device connects to the Internet. To permanently remove the device from your account page, sign out of iCloud, iTunes & App Stores, iMessage, FaceTime, and Game Center on that device, or erase that device.
Источник
Use Apple products on enterprise networks
Learn which hosts and ports are required to use your Apple products on enterprise networks.
This article is intended for enterprise and education network administrators.
Apple products require access to the internet hosts in this article for a variety of services. Here’s how your devices connect to hosts and work with proxies:
- Network connections to the hosts below are initiated by the device, not by hosts operated by Apple.
- Apple services will fail any connection that uses HTTPS Interception (SSL Inspection). If the HTTPS traffic traverses a web proxy, disable HTTPS Interception for the hosts listed in this article.
Make sure your Apple devices can access the hosts listed below.
Apple Push Notifications
Learn how to troubleshoot connecting to the Apple Push Notification service (APNs). For devices that send all traffic through an HTTP proxy, you can configure the proxy either manually on the device or with a configuration profile. Beginning with macOS 10.15.5, devices can connect to APNs when configured to use the HTTP proxy with a proxy auto-config (PAC) file.
Device setup
Access to the following hosts might be required when setting up your device, or when installing, updating, or restoring the operating system.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| albert.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Device activation | Yes |
| captive.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | Internet connectivity validation for networks that use captive portals | Yes |
| gs.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Yes | |
| humb.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Yes | |
| static.ips.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | Yes | |
| sq-device.apple.com | 443 | TCP | iOS and iPadOS | eSIM activation | — |
| tbsc.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Yes | |
| time-ios.apple.com | 123 | UDP | iOS, iPadOS, and tvOS | Used by devices to set their date and time | — |
| time.apple.com | 123 | UDP | iOS, iPadOS, tvOS, and macOS | Used by devices to set their date and time | — |
| time-macos.apple.com | 123 | UDP | macOS only | Used by devices to set their date and time | — |
Device Management
Network access to the following hosts might be required for devices enrolled in Mobile Device Management (MDM).
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| *.push.apple.com | 443, 80, 5223, 2197 | TCP | iOS, iPadOS, tvOS, and macOS | Push notifications | Learn more about APNs and proxies. |
| deviceenrollment.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | DEP provisional enrollment | — |
| deviceservices-external.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | — | |
| gdmf.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Used by an MDM server to identify which software updates are available to devices that use managed software updates | Yes |
| identity.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | APNs certificate request portal | Yes |
| iprofiles.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Hosts enrollment profiles used when devices enroll in Apple School Manager or Apple Business Manager through Device Enrollment | Yes |
| mdmenrollment.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | MDM servers to upload enrollment profiles used by clients enrolling through Device Enrollment in Apple School Manager or Apple Business Manager, and to look up devices and accounts | Yes |
| setup.icloud.com | 443 | TCP | iOS and iPadOS | Required to log in with a Managed Apple ID on Shared iPad | — |
| vpp.itunes.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | MDM servers to perform operations related to Apps and Books, like assigning or revoking licenses on a device | Yes |
Apple School Manager and Apple Business Manager
Network access to the following hosts as well as the hosts in the App Store section is required for full functionality of Apple School Manager and Apple Business Manager.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
| *.business.apple.com | 443, 80 | TCP | — | Apple Business Manager | — |
| *.school.apple.com | 443, 80 | TCP | — | Schoolwork Roster service | — |
| isu.apple.com | 443, 80 | TCP | — | — | |
| ws-ee-maidsvc.icloud.com | 443, 80 | TCP | — | Schoolwork Roster service | — |
Apple Business Essentials device management
Network access to the following hosts is required for full functionality of Apple Business Essentials device management.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| axm-adm-enroll.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | DEP enrollment server | — |
| axm-adm-mdm.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | MDM server | — |
| axm-adm-scep.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | SCEP server | — |
| axm-app.apple.com | 443 | TCP | iOS, iPadOS, and macOS | Used by Apple Business Essentials to view and manage apps and devices | — |
Software updates
Make sure you can access the following ports for updating macOS, apps from the Mac App Store, and for using content caching.
macOS, iOS, and tvOS
Network access to the following hostnames is required for installing, restoring, and updating macOS, iOS, and tvOS.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| appldnld.apple.com | 80 | TCP | iOS and iPadOS | iOS updates | — |
| configuration.apple.com | 443 | TCP | macOS only | Rosetta 2 updates | — |
| gdmf.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Software update catalog | — |
| gg.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | iOS, tvOS, and macOS updates | Yes |
| gnf-mdn.apple.com | 443 | TCP | macOS only | macOS updates | Yes |
| gnf-mr.apple.com | 443 | TCP | macOS only | macOS updates | Yes |
| gs.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | iOS, iPadOS, tvOS, and macOS updates | Yes |
| ig.apple.com | 443 | TCP | macOS only | macOS updates | Yes |
| mesu.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | Hosts software update catalogs | — |
| ns.itunes.apple.com | 443 | TCP | iOS and iPadOS | Yes | |
| oscdn.apple.com | 443, 80 | TCP | macOS only | macOS Recovery | — |
| osrecovery.apple.com | 443, 80 | TCP | macOS only | macOS Recovery | — |
| skl.apple.com | 443 | TCP | macOS only | macOS updates | — |
| swcdn.apple.com | 80 | TCP | macOS only | macOS updates | — |
| swdist.apple.com | 443 | TCP | macOS only | macOS updates | — |
| swdownload.apple.com | 443, 80 | TCP | macOS only | macOS updates | Yes |
| swpost.apple.com | 80 | TCP | macOS only | macOS updates | Yes |
| swscan.apple.com | 443 | TCP | macOS only | macOS updates | — |
| updates-http.cdn-apple.com | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Software update downloads | — |
| updates.cdn-apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Software update downloads | — |
| xp.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Yes |
App Store
Access to the following hosts might be required for updating apps.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| *.itunes.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | Store content such as apps, books, and music | Yes |
| *.apps.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Store content such as apps, books, and music | Yes |
| *.mzstatic.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Store content such as apps, books, and music | — |
| itunes.apple.com | 443, 80 | TCP | iOS, iPadOS, tvOS, and macOS | Yes | |
| ppq.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Enterprise App validation | — |
Carrier updates
Cellular devices must be able to connect to the following hosts to install carrier bundle updates.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| appldnld.apple.com | 80 | TCP | iOS and iPadOS | Cellular carrier bundle updates | — |
| appldnld.apple.com.edgesuite.net | 80 | TCP | iOS and iPadOS | Cellular carrier bundle updates | — |
| itunes.com | 80 | TCP | iOS and iPadOS | Carrier bundle update discovery | — |
| itunes.apple.com | 443 | TCP | iOS and iPadOS | Carrier bundle update discovery | — |
| updates-http.cdn-apple.com | 80 | TCP | iOS and iPadOS | Cellular carrier bundle updates | — |
| updates.cdn-apple.com | 443 | TCP | iOS and iPadOS | Cellular carrier bundle updates | — |
Content caching
A Mac that provides content caching must be able to connect to the following hosts, as well as the hosts listed in this document that provide Apple content such as software updates, apps, and additional content.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| lcdn-registration.apple.com | 443 | TCP | macOS only | Server registration | Yes |
| suconfig.apple.com | 80 | TCP | macOS only |
Clients of macOS content caching must be able to connect to the following hosts.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| lcdn-locator.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Content caching locator service | — |
| serverstatus.apple.com | 443 | TCP | macOS only | Content caching client public IP determination | — |
Apple Developer
Access to the following hosts is required for app notarization and app validation.
App notarization
Starting with macOS 10.14.5, software is checked for notarization before it will run. In order for this check to succeed, a Mac must be able to access the same hosts listed in the Ensure Your Build Server Has Network Access section of Customizing the Notarization Workflow.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| 17.248.128.0/18 | 443 | TCP | macOS only | Ticket delivery | — |
| 17.250.64.0/18 | 443 | TCP | macOS only | Ticket delivery | — |
| 17.248.192.0/19 | 443 | TCP | macOS only | Ticket delivery | — |
App validation
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
| *.appattest.apple.com | 443 | TCP | iOS, iPadOS, and macOS | App validation, Touch ID and Face ID authentication for websites | — |
Feedback Assistant
Feedback Assistant is an app used by developers and members of the beta software programs to report feedback to Apple. It uses the following hosts:
| Hosts | Port | Protocol | OS | Description | Supports proxies |
| bpapi.apple.com | 443 | TCP | tvOS only | Provides beta software updates | Yes |
| cssubmissions.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Used by Feedback Assistant to upload files |
Apple diagnostics
Apple devices might access the following host in order to perform diagnostics used to detect a possible hardware issue.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
| diagassets.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Used by Apple devices to help detect possible hardware issues | Yes |
Domain Name System resolution
In order to use encrypted Domain Name System (DNS) resolution in iOS 14, tvOS 14, and macOS Big Sur, the following host will be contacted.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
| doh.dns.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Used for DNS over HTTPS (DoH) | Yes |
Certificate validation
Apple devices must be able to connect to the following hosts to validate digital certificates used by the hosts in this article.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| certs.apple.com | 80, 443 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| crl.apple.com | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| crl.entrust.net | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| crl3.digicert.com | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| crl4.digicert.com | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| ocsp.apple.com | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| ocsp.digicert.cn | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation in China | — |
| ocsp.digicert.com | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| ocsp.entrust.net | 80 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| ocsp2.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | — |
| valid.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Certificate validation | Yes |
Apple ID
Apple devices must be able to connect to the following hosts in order to authenticate an Apple ID. This is required for all services that use an Apple ID, such as iCloud, app installation, and Xcode.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| appleid.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Apple ID authentication in Settings and System Preferences | Yes |
| appleid.cdn-apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Apple ID authentication in Settings and System Preferences | Yes |
| idmsa.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Apple ID authentication | Yes |
| gsa.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | Apple ID authentication | Yes |
iCloud
In addition to the Apple ID hosts listed above, Apple devices must be able to connect to hosts in the following domains to use iCloud services.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| *.apple-cloudkit.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.apple-livephotoskit.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.apzones.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services in China | — |
| *.cdn-apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.gc.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.icloud.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.icloud.com.cn | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services in China | — |
| *.icloud.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.icloud-content.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iCloud services | — |
| *.iwork.apple.com | 443 | TCP | iOS, iPadOS, tvOS, and macOS | iWork documents | — |
Additional content
Apple devices must be able to connect to the following hosts to download additional content. Some additional content might also be hosted on third-party content distribution networks.
| Hosts | Ports | Protocol | OS | Description | Supports proxies |
|---|---|---|---|---|---|
| audiocontentdownload.apple.com | 80, 443 | TCP | iOS, iPadOS, and macOS | GarageBand downloadable content | — |
| devimages-cdn.apple.com | 80, 443 | TCP | macOS only | Xcode downloadable components | — |
| download.developer.apple.com | 80, 443 | TCP | macOS only | Xcode downloadable components | — |
| playgrounds-assets-cdn.apple.com | 443 | TCP | iPadOS and macOS | Swift Playgrounds | — |
| playgrounds-cdn.apple.com | 443 | TCP | iPadOS and macOS | Swift Playgrounds | — |
| sylvan.apple.com | 80, 443 | TCP | tvOS only | Apple TV screen savers | — |
Firewalls
If your firewall supports using hostnames, you might be able to use most Apple services above by allowing outbound connections to *.apple.com. If your firewall can only be configured with IP addresses, allow outbound connections to 17.0.0.0/8. The entire 17.0.0.0/8 address block is assigned to Apple.
HTTP proxy
You can use Apple services through a proxy if you disable packet inspection and authentication for traffic to and from the listed hosts. Exceptions to this are noted above. Attempts to perform content inspection on encrypted communications between Apple devices and services will result in a dropped connection to preserve platform security and user privacy.
Источник