- One Across : Celebs on Squares
- 8 приложений для Android, которые нужно удалить. Они опасны
- Вредоносные приложения для Android
- Как найти вирус на Android
- Как отменить подписку на Андроиде
- In-app updates
- Update flows
- Flexible updates
- Immediate updates
- Support in-app updates in your app
- Developer guide
- Prerequisites
- Work profiles
- Key features of a work profile
- Work profile benefits on Android 5.0+
- Considerations for work profiles
- Prevent intents from failing between profiles
- Share files across profiles
- Implement managed configurations
- Best practices for implementing managed configurations
- When first launching the app
- Listen for changes to managed configurations
- Dedicated devices
- Set up single sign-on with Chrome custom tabs
- Requirements
- How do I implement SSO with custom tabs?
- Test your app
- Use Test DPC to test your Android app
- Provision a work profile
- Provision a fully managed device
- End-to-end testing
One Across : Celebs on Squares
Вам надоели старомодные кроссворды? Ты любишь кино? One Across — это кроссворд с интересным поворотом: посмотрите на фотографии своих кино-кумиров (актеров, режиссеров, музыкантов и т. Д.) И заполните кроссворд их именами. Тысячи знаменитостей из кино ждут вас, чтобы развлечься с каждым новым началом.
Но дело не только в кинобизнесе:
➤ Играйте в классические кроссворды, чтобы улучшить свой словарный запас и легко выучить язык.
➤ Или вы учитесь на врача? Проверьте свои возможности в обнаружении слов из медицинских терминов.
И еще больше уровней!
➤ Свежий взгляд: если вам нравится играть в настольные игры и головоломки, вам понравится наш красивый, чистый и интуитивно понятный интерфейс.
➤ Удобно и легко играть.
➤ Играйте онлайн с подсказками и картинками или офлайн с подсказками.
➤ Неограниченное количество комбинаций кроссвордов, созданных на лету с любого нового старта. Тысячи словесных подсказок перемешиваются и восстанавливаются при каждом дубле.
➤ Поддерживаются кроссворды разных размеров. Размер сетки адаптируется к вашему устройству.
➤ 100% захватывающая игра в слова: у вас никогда не будет скучных моментов! Сыграйте в этот кроссворд один раз, и вы не сможете его разгадать!
➤ Разблокируйте неограниченное количество подсказок или неограниченное количество кроссвордов с помощью нашей системы покупок в приложении.
Источник
8 приложений для Android, которые нужно удалить. Они опасны
Кто бы что ни говорил, но Google Play – это помойка. Не даром её признали самым популярным источником вредоносного софта для Android. Просто пользователи в большинстве своём доверяют официальном магазину приложений Google и скачивают оттуда любое ПО без разбору. А какой ещё у них есть выбор? Ведь их всегда учили, что скачивать APK из интернета куда опаснее. В общем, это действительно так. Но остерегаться опасных приложений в Google Play нужно всегда. По крайней мере, постфактум.
Есть как минимум 8 приложений, которые нужно удалить
Google добавила в Google Play функцию разгона загрузки приложений
Исследователи кибербезопасности из антивирусной компании McAfee обнаружили в Google Play 8 вредоносных приложений с многомиллионными загрузками. Попадая на устройства своих жертв, они скачивают получают доступ к сообщениям, а потом совершают от их имени покупки в интернете, подтверждая транзакции кодами верификации, которые приходят в виде SMS.
Вредоносные приложения для Android
Нашли вирус? Удалите его
В основном это приложения, которые потенциально высоко востребованы пользователями. Среди них есть скины для клавиатуры, фоторедакторы, приложения для создания рингтонов и др.:
- com.studio.keypaper2021
- com.pip.editor.camera
- org.my.famorites.up.keypaper
- com.super.color.hairdryer
- com.celab3.app.photo.editor
- com.hit.camera.pip
- com.daynight.keyboard.wallpaper
- com.super.star.ringtones
Это названия пакетов приложений, то есть что-то вроде их идентификаторов. Поскольку всё это вредоносные приложения, их создатели знают, что их будут искать и бороться с ними. Поэтому они вполне могут быть готовы к тому, чтобы менять пользовательские названия приложений, которые видим мы с вами. Но это мы не можем этого отследить. Поэтому куда надёжнее с этой точки зрения отслеживать именно идентификаторы и удалять вредоносный софт по ним.
Как найти вирус на Android
Но ведь, скажете вы, на смартфоны софт устанавливается с пользовательскими названиями. Да, это так. Поэтому вам понадобится небольшая утилита, которая позволит вам эффективно выявить весь шлаковый софт, который вы себе установили, определив название их пакетов.
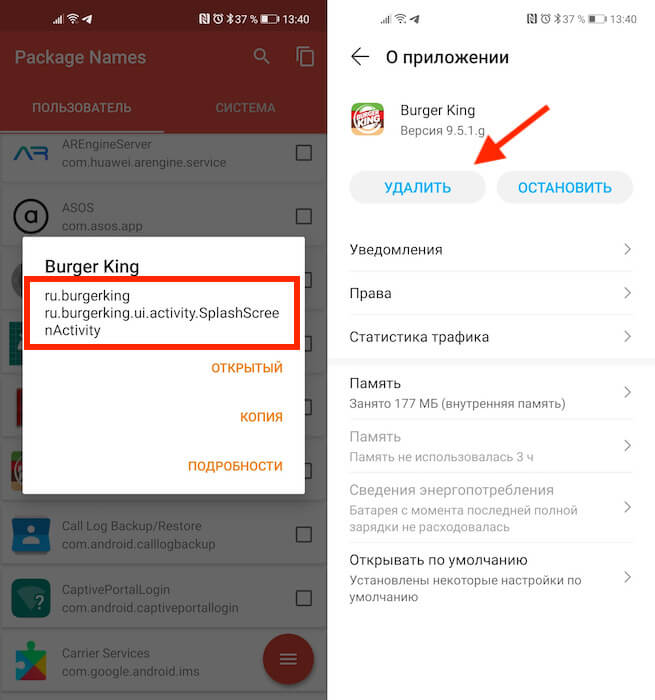
- Скачайте приложение для чтения пакетов Package Name Viewer;
- Запустите его и дайте те привилегии, которые запросит приложение;
В красном квадрате приведен пример названия пакета
- Поочерёдно вбивайте в поиск названия пакетов, приведённые выше;
- При обнаружении приложений с такими именами, нажимайте на них и удаляйте.
Package Name Viewer удобен тем, что позволяет не просто найти нужное приложение по названию его пакета, но и при необходимости перейти в настройки для его удаления. Для этого достаточно просто нажать на иконку приложения, как вы попадёте в соответствующий раздел системы, где сможете остановить, отключить, удалить накопленные данные, отозвать привилегии или просто стереть нежелательную программу.
Как отменить подписку на Андроиде
Лучше всего приложение именно удалить. Это наиболее действенный способ защитить себя от его активности. Однако не исключено, что оно могло подписать вас на платные абонементы, поэтому для начала проверьте свою карту на предмет неизвестных списаний, а потом просмотрите список действующих подписок в Google Play:
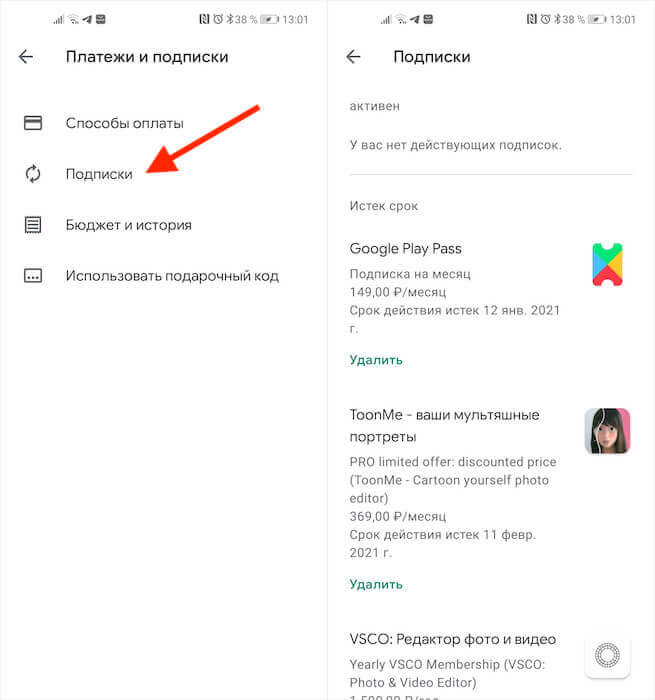
- Запустите Google Play и нажмите на иконку своего профиля;
- В открывшемся окне выберите раздел «Платежи и подписки»;
Если подписка оформлена через Google Play, отменить её ничего не стоит
- Здесь выберите «Подписки» и проверьте, нет ли среди них неизвестных;
- Если есть, просто нажмите напротив неё на кнопку «Отменить».
В принципе, если подписка была оформлена через Google Play и оплата уже прошла, вы можете потребовать у Google вернуть уплаченные деньги. О том, как это делается, мы описывали в отдельной статье. Но поскольку разработчики таких приложений обычно тщательно продумывают способы воровства денег, как правило, они не используют встроенный в Google Play инструмент проведения платежей, чтобы их в случае чего не могли отозвать.
Источник
In-app updates
When your users keep your app up to date on their devices, they can try new features, as well as benefit from performance improvements and bug fixes. Although some users enable background updates when their device is connected to an unmetered connection, other users might need to be reminded to install updates. In-app updates is a Play Core library feature that prompts active users to update your app.
The in-app updates feature is supported on devices running Android 5.0 (API level 21) or higher, and requires your app to use Play Core library version 1.5.0 or higher. Additionally, in-app updates are only supported for Android mobile devices, Android tablets, and Chrome OS devices.
Update flows
Your app can use the Play Core library to support the following UX flows for in-app updates:
Flexible updates
Flexible updates provide background download and installation with graceful state monitoring. This UX flow is appropriate when it’s acceptable for the user to use the app while downloading the update. For example, you might want to encourage users to try a new feature that’s not critical to the core functionality of your app.
Figure 1. An example of a flexible update flow.
Immediate updates
Immediate updates are fullscreen UX flows that require the user to update and restart the app in order to continue using it. This UX flow is best for cases where an update is critical to the core functionality of your app. After a user accepts an immediate update, Google Play handles the update installation and app restart.
Figure 2. An example of an immediate update flow.
Support in-app updates in your app
Learn how to support in-app updates in your app, depending on your development environment:
Content and code samples on this page are subject to the licenses described in the Content License. Java is a registered trademark of Oracle and/or its affiliates.
Источник
Developer guide
Android’s enterprise features provide organizations with a secure, flexible, and unified Android mobility platform—combining devices, applications, and management. Android apps are compatible with Android’s enterprise features by default. However, there are additional features you can use to make your app work best on managed Android devices:
- Work profile compatibility—Modify your Android app so it functions best on a managed device.
- Managed configurations—Modify your app to allow IT admins the option to specify custom settings for your apps.
- Dedicated devices—Optimize your app so that it can be deployed on an Android device as a kiosk.
- Single Sign-On (SSO)—Simplify the sign-on process for users signing in to different apps on their managed Android device.
Prerequisites
- You’ve created an Android app.
- You’re ready to modify your app so that it works best for organizations.
- Minimum version: Android 5.0 Lollipop recommended version: Android 6.0 Marshmallow and later.
Note: Android’s enterprise features are built into most Android 5.0 devices; however, Android 6.0 and later offers additional features, especially with regard to dedicated devices.
Work profiles
You can manage a user’s business data and applications through a work profile. A work profile is a managed corporate profile associated with the primary user account on an Android device. A work profile securely isolates work apps and data from personal apps and data. This work profile is in a separate container from the personal profile, which your user controls. These separate profiles allow organizations to manage the business data they care about, but leave everything else on a user’s device under the user’s control. For a deep dive into best practices, see the Work profiles guide. For an overview of those best practices, see below.
Key features of a work profile
- Separate and secure profile
- Managed Google Play for application distribution
- Separate badged work applications
- Profile-only management capabilities controlled by an admin
Work profile benefits on Android 5.0+
- Full device encryption
- One Android application package (APK) for both profiles when there’s a personal profile and a work profile present on the device
- Device policy controller (DPC) is limited to the work profile
- Device administration via the DevicePolicyManager class
Considerations for work profiles
- The Android system prevents intents from crossing profiles and IT admins can enable or disable system apps.
- A file path (Uniform Resource Identifier [URI]) that’s valid on one profile may not be valid on the other.
Prevent intents from failing between profiles
It’s difficult to know which intents can cross between profiles, and which ones are blocked. The only way to know for sure is by testing. Before your app starts an activity, you should verify that the request is resolved by calling Intent.resolveActivity() .
- If it returns null , the request doesn’t resolve.
- If it returns something, it shows that the intent resolves, and it’s safe to send the intent.
Note: For detailed testing instructions, see Prevent Failed Intents.
Share files across profiles
Some developers use URIs to mark file paths in Android. However, because there are separate file systems when a work profile is present, we recommend:
| Use: Content URIs |
|
| Don’t use: File URI |
|
Next steps: Once your app supports managed profiles, test it in a work profile. See Test your app.
Implement managed configurations
Managed configurations are a set of instructions that IT admins can use to manage their users’ mobile devices in a specific way. These instructions are universal and work across any EMM, allowing admins to remotely configure applications on their users’ phones.
If you’re developing apps for business or government, you may need to satisfy your industry’s specific set of requirements. Using managed configurations, the IT admin can remotely specify settings and enforce policies for their users’ Android apps; for example:
- Configure if an app can sync data via cellular/3G, or only Wi-Fi
- Allow or block URLs on a web browser
- Configure an app’s email settings
- Enable or disable printing
- Manage bookmarks
Best practices for implementing managed configurations
The Set up Managed Configurations guide is the key source for information on how to build and deploy managed configurations. After you’ve reviewed this documentation, see recommendations below for additional guidance.
When first launching the app
As soon as you launch an application, you can see if managed configurations are already set for this app in onStart() or onResume() . Additionally, you can find out if your application is managed or unmanaged. For example, if getApplicationRestrictions() returns:
- A set of application-specific restrictions—You can configure the managed configurations silently (without requiring user input).
- An empty bundle—Your application acts like it’s unmanaged (for example, how the app behaves in a personal profile).
- A bundle with a single key value pair with KEY_RESTRICTIONS_PENDING set to true—your application is being managed, but the DPC isn’t configured correctly. You should block this user from your app, and direct them to their IT admin.
Listen for changes to managed configurations
IT admins can change managed configurations and what policies they want to enforce on their users at any time. Because of this, we recommend you ensure that your app can accept new restrictions for your managed configuration as follows:
- Fetch restrictions on launch—Your app should call getApplicationRestrictions() in onStart() and onResume() , and compare against old restrictions to see if changes are required.
- Listen while running—Dynamically register ACTION_APPLICATION_RESTRICTIONS_CHANGED in your running activities or services, after you’ve checked for new restrictions. This intent is sent only to listeners that are dynamically registered, and not to listeners declared in the app manifest.
- Unregister while not running—In onPause() , you should unregister for the broadcast of ACTION_APPLICATION_RESTRICTIONS_CHANGED .
Dedicated devices
Dedicated devices are kiosk devices used for a single purpose, such as digital signage displays, ticket printing kiosks, or checkout registers.
When an Android device is configured as a dedicated device, the user sees an application locked to the screen with no Home or Recent Apps buttons to escape the app. Dedicated devices can also be configured to show a set of applications, such as a library kiosk with an app for the library catalog and a web browser.
Set up single sign-on with Chrome custom tabs
Enterprise users often have multiple apps on their device, and they prefer to sign in once to access all of their work applications. Typically, users sign in through a WebView; however, there are a couple reasons why this isn’t ideal:
- Users often need to sign in multiple times with the same credentials. The WebView solution often isn’t a true Single Sign-On (SSO) experience.
- There can be security risks, including malicious applications inspecting cookies or injecting JavaScript® to access a user’s credentials. Even trusted developers are at risk if they rely on potentially malicious third-party SDKs.
A solution to both problems is to authenticate users using browser Custom Tabs, instead of WebView. This ensures that authentication:
- Occurs in a secure context (the system browser) where the host app cannot inspect contents.
- Has a shared cookie state, ensuring the user has to sign in only once.
Requirements
Custom Tabs are supported back to API level 15 (Android 4.0.3). To use Custom Tabs you need a supported browser, such as Chrome. Chrome 45 and later implement this feature as Chrome Custom Tabs.
How do I implement SSO with custom tabs?
Google has open sourced an OAuth client library that uses Custom Tabs, contributing it to the OpenID Connect working group of the OpenID Foundation. To set up Custom Tabs for SSO with the AppAuth library, see the documentation and sample code on GitHub.
Test your app
After you’ve developed your app, you’ll want to test it—both in a work profile and on a fully managed device. See the instructions below.
Use Test DPC to test your Android app
We provide the Test DPC app to help Android developers test their apps in an enterprise environment. Using Test DPC, you can set EMM policies or managed configuration values on a device—as if an organization managed the device using an EMM. To install Test DPC on a device, choose one of the following methods:
- Install Test DPC from GooglePlay.
- Build from the source on GitHub.
For more information on how to configure Test DPC, see the instructions below and the Test DPC User Guide.
Provision a work profile
To test your app in a work profile, you need to first provision a work profile on device using the Test DPC app, as follows:
- Install Test DPC on the device.
- In the Android launcher, tap the Set up Test DPC app icon.
- Follow the onscreen instructions.
- Install your app on the device and test to see how it runs in the work profile.
Android creates a work profile and installs a copy of Test DPC in the work profile. You use this work-badged instance of Test DPC to set policies and managed configurations in the work profile. To learn more about setting up a work profile for development, read the developer’s guide Work profiles.
Provision a fully managed device
Organizations use fully managed devices because they can enforce a full range of management policies on the device. To provision a fully managed device, follow these steps:
- Install Test DPC on the device.
- Confirm that there are no other users or a work profile on the device.
- Confirm that there are no accounts on the device.
- Run the following Android Debug Bridge (adb) command in your terminal:
- Once you’ve completed provisioning the device owner, you can test your app on that device. You should specifically test how managed configurations and intents work on that device.
You can also use other provisioning methods—see the Test DPC User Guide. To learn how IT admins typically enroll and provision Android-powered devices, read Provision devices.
End-to-end testing
After you’ve finished testing your app in the environments above, you’ll likely want to test your app in an end-to-end production environment. This process includes the steps a customer needs to take to deploy your app in their organization, including:
- App distribution through Play
- Server-side managed configuration
- Server-side profile policy control
You need to access an EMM console to complete the end-to-end testing. The easiest way to get one is to request a testing console from your EMM. Once you have access, complete these tasks:
- Create a test version of your application with a new ApplicationId.
- Claim a managed Google domain and bind it to your EMM. If you already have a testing domain that’s bound to an EMM, you may need to unbind it to test it with your preferred EMM. Please consult your EMM for the specific unbinding steps.
- Publish your application to the private channel for their managed Google domain.
- Use the EMM console and EMM application to:
- Set up work devices.
- Distribute your application.
- Set managed configuration.
- Set device policies.
This process will differ based on your EMM. Please consult your EMM’s documentation for further details. Congrats! You’ve completed these steps and verified that your app works well for enterprise users.
Content and code samples on this page are subject to the licenses described in the Content License. Java is a registered trademark of Oracle and/or its affiliates.
Источник