- PGPTools для iPhone и iPad — надежное шифрование личной переписки
- Researchers Propose New Way to Limit Location Tracking With ‘Pretty Good Phone Privacy’
- Pretty Good Phone Privacy
- Pretty good phone privacy iphone
- Best phones for privacy
- How to keep your phone private
- Secure your lock screen
- Manage your location services
- Limit app accessibility
- Don’t save password in your browser
- Use a password manager
- Stick to official apps
- Stay off public Wi-Fi
- Activate Find my iPhone
- Best phones for privacy
- Purism Librem 5
- iPhone 12
- Google Pixel 5
- Bittium Tough Mobile 2
- Silent Circle Blackphone 2
- Fairphone 3
PGPTools для iPhone и iPad — надежное шифрование личной переписки
В последнее время проблема защиты личных данных тревожит не только IT-специалистов и продвинутых пользователей, но и всякого, кто в курсе событий последних лет, таких как массовые утечки конфиденциальной информации, взломы аккаунтов, кражи данных учетных записей и т.д.
Впрочем, защититься от постороннего вмешательства не так уж сложно — это может сделать фактически любой пользователь, не прикладывая особых усилий. В этом материале мы расскажем о простой, но довольно эффективной утилите PGPTools, которая позволит надежно зашифровать вашу личную переписку и гарантировать ее конфиденциальность.
Как и следует из названия программы, в ее основе лежит система шифрования с нескромным, но многообещающим названием PGP, что расшифровывается как Pretty Good Protect. Разработана она была почти 15 лет назад и считается одной из самых надежных в своем роде. Упрощенно, принцип работы отчетного приложения выглядит следующим образом — двое пользователей имеют PGP-ключ шифрования, при помощи которого могут как распознавать, так и создавать закодированные сообщения.
При этом PGPTools позволяет отправлять зашифрованные послания не только на электронную почту, но и через любой другой сервис, поддерживающий текстовые сообщения — Skype, ICQ, SMS, WhatsApp и т.д. Для этого нужно лишь скопировать код из приложения и вставить в сообщение, после чего получатель произведет обратную процедуру — скопирует код из мессенджера, а затем введет его в PGPTools, где он и будет расшифрован.
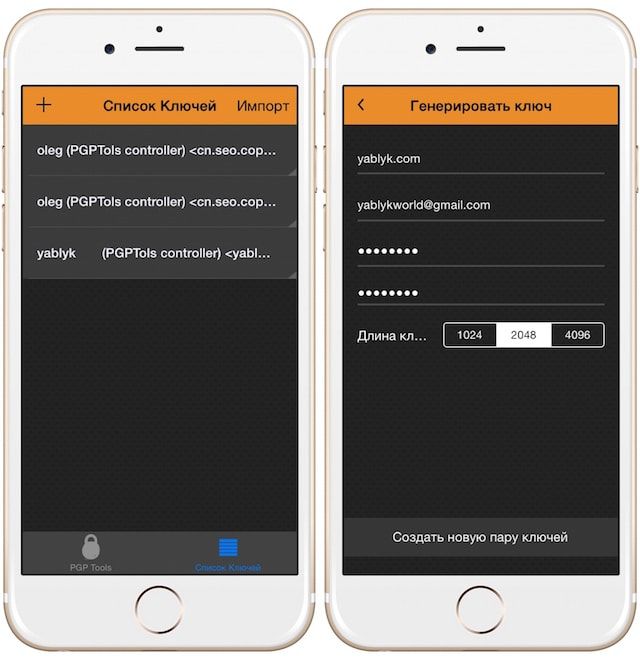
Важная особенность PGPTools — максимальная простота интерфейса и процесса взаимодействия с ним. Чтобы не пугать пользователей тонкими настройками и большим количеством сложных технических опций, разработчики практически упразднили их. Приложение разделено всего на два основных экрана — на одном отображается список ключей, на другом производится непосредственно шифрование и расшифровка сообщений.
Итак, нажав «+» в верхнем левом углу в разделе «Список ключей» (скриншот выше), необходимо ввести его имя, электронный адрес получателя, пароль и выбрать длину ключа в битах (1024, 2048 или 4096). Имеется также возможность импорта уже созданных ранее PGP-ключей.
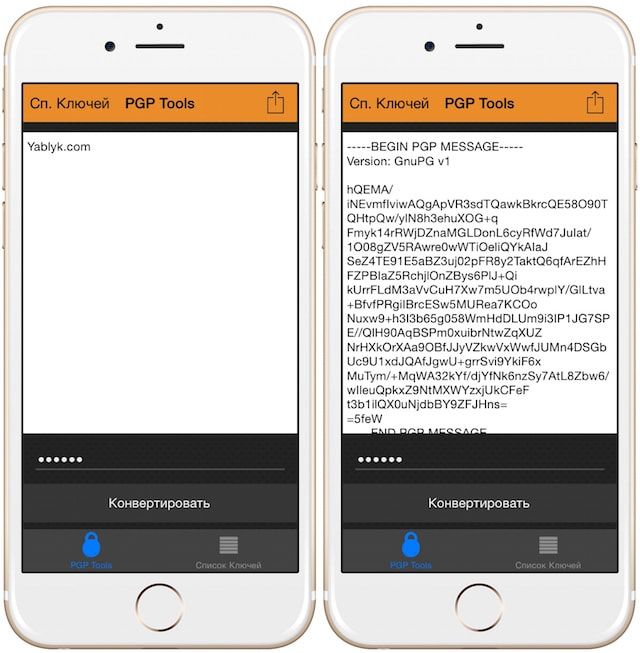
После чего можно переходить непосредственно к переписке, то есть, в раздел PGPTools. В основное поле нужно ввести или вставить из буфера обмена исходный текст, затем выбрать ключ из списка созданных, ввести пароль от него и нажать кнопку «Конвертировать». Полученный код можно скопировать и отправить получателю по E-mail, через мессенджеры, социальные сети и т.д. Обратный процесс не менее прост — получаем код, вставляем в основное поле, выбираем ключ, вводим пароль и видим на экране расшифрованное сообщение.
Простота, удобство и эффективность PGPTools делают данную программу весьма привлекательной для широкой массы пользователей. При этом приложение можно использовать практически на любом устройстве — под управлением iOS, Android, Windows Phone, а также десктопных платформах.
Источник
Researchers Propose New Way to Limit Location Tracking With ‘Pretty Good Phone Privacy’
Researchers at the University of Southern California (USC) Viterbi School of Engineering and Princeton University have proposed a way to limit smartphone tracking from carriers. It’s called Pretty Good Phone Privacy (PGPP).
Pretty Good Phone Privacy
Even if you have GPS turned off there’s a good chance your carrier is still able to track your location. Our phones reveal personal identifiers to cell towers owned by major network operators. However, there is a software fix that could change that, dubbed Pretty Good Phone Privacy.
It decouples phone connectivity from authentication and billing by anonymizing personal identifiers sent to cell towers. Their new system works by breaking the direct line of communication between the user’s cellphone and the cell tower. Instead of sending a personally identifiable signal to the cell tower, it sends an anonymous “token.” It does this by using a mobile virtual network operator, such as Cricket or Boost, as a proxy or intermediary.
Barath Raghavan, an assistant professor in computer science at USC, an a co-author of this solution:
We’ve unwittingly accepted that our phones are tracking devices in disguise, but until now we’ve had no other option—using mobile devices meant accepting this tracking. We figured out how to decouple authentication from connectivity and ensure privacy while maintaining seamless connectivity, and it is all done in software.
Since the system works by stopping a phone from identifying its user to the cell tower, all other location-based services—such as searching for the nearest gas station, or contact tracing—still work as usual. The researchers hope the technology will be accepted by major networks as default, particularly with mounting legal pressure to adopt new privacy measures.
Источник
Pretty good phone privacy iphone
Краткое описание:
Почтовый клиет с OpenPGP, обменом ключами через p2p, импортом ключей из других клиентов.
Описание:
p≡p is a cyber security solution which protects the confidentiality and reliability of communications for citizens, for public offices and for enterprises. It provides end-to-end cryptography in all common crypto-standards through the app that you install on your phone.
p≡p for Android makes e-mail encryption easy on mobile devices for everyone by automatic and seamless integration of end-to-end encryption. Set it up with your existing e-mail address under a minute. Send and receive as many messages as you want without any restrictions on the number of devices the p≡p app runs on.
p≡p supports the user with advanced automation and is fully compatible with OpenPGP
★ it will automatically encrypt your e-mail and attachments, including pictures
★ it can ensure no one can intercept your perfectly encrypted e-mail
★ it is peer-to-peer and uses no central service
★ it works with all your existing e-mail account(s)
★ it can authenticate your communication partner and prevent identity theft
★ it offers security and privacy by default
p≡p is end-to-end and supports all commonly used Android devices.
p≡p is easy for your recipients too – depending on their security capabilities, they can exchange encrypted messages with you.
With p≡p, you don’t need a separate account, you can send secure messages to anyone anywhere, regardless of their email provider.
Just install the app and you can communicate in confidence with your peers.
Now also with function to import keys from another p≡p client — Outlook, Android, iOS (Enigmail soon as well).
Требуется Android: 4.3 и выше
Русский интерфейс: Частично
Версия: 1.1.204 Paid (Katafrakt)
Версия: 1.1.008 Paid (Katafrakt)
версия: 1.0.213 (F-Droid) 
Сообщение отредактировал iMiKED — 22.03.21, 06:31
А заявлено несколько другое. 4.3+. Возможно, единичный случай.
Сообщение отредактировал Dementy000 — 17.12.18, 13:22
pEp — это решение для кибербезопасности, которое защищает конфиденциальность и надежность связи для граждан, государственных учреждений и предприятий. Он обеспечивает сквозную криптографию во всех распространенных криптостандартах через приложение, которое вы устанавливаете на свой телефон.
pEp для Android делает
шифрование электронной почты на мобильных устройствах легкой для всех благодаря автоматической и плавной интеграции сквозного шифрования. Установите его с вашим существующим адресом электронной почты в течение минуты. Отправляйте и получайте столько сообщений, сколько хотите, без каких-либо ограничений на количество устройств, на которых работает приложение pEp.
pp поддерживает пользователя с продвинутой автоматизацией и полностью совместим с OpenPGP
— автоматически зашифрует вашу электронную почту и вложения, в том числе фотографии
— гарантия того, что никто не сможет перехватить вашу зашифрованную электронную почту
— децентрализованное шифрование
— работает со всеми вашими существующими учетными записями электронной почты
— можно подтвердить подлинность вашего партнера по общению и предотвратить кражу личных данных
— по умолчанию обеспечивается безопасность и конфиденциальность
pEp является сквозным и поддерживает все распространенные устройства Android.
pEp также прост для ваших получателей — в зависимости от их возможностей безопасности они могут обмениваться с вами зашифрованными сообщениями.
С pEp, вам не нужна отдельная учетная запись, вы можете отправлять защищенные сообщения кому угодно, независимо от их поставщика электронной почты.
Просто установите приложение, и общайтесь конфиденциально.
Поддерживается функция импорта ключей из другого pp-клиента — Outlook, Android, iOS (скоро также Enigmail).
Сообщение отредактировал tweed_man — 17.12.18, 19:05
Источник
Best phones for privacy
Last updated: 4th Nov 2021 — Estimated read time: 7 minutes
How to keep your phone private
Every electronic device is hackable. Luckily there are measures you can take to protect yourself and your personal data.
Secure your lock screen
This may seem obvious, but some people still only rely on a swipe to unlock their smartphone. To keep your phone protected, you should set a strong password or PIN. Make sure the password or number isn’t related to you, such as your birth date. Anything too obvious is easy for a thief to guess.
Manage your location services
If you turn off your location services, you and your phone can’t be tracked.
Limit app accessibility
Many of the apps on your phone will request access to other things on your device, like your files, camera, or GPS. Make sure you have these turned off for apps that don’t need them to prevent oversharing information.
Don’t save password in your browser
Don’t allow your browsers, such as Safari or Chrome, to save your passwords. They’re actually stored in your browser as plain text, so if your phone is ever compromised, so are your passwords.
Use a password manager
You can install a password manager to manage and keep track of your passwords online. You won’t have to remember the complicated ones or risk writing them down for someone to find.
Stick to official apps
Only download apps from the official app stores (Apple Store and Google Play Store). These platforms have security measures in place to protect you. Downloading apps elsewhere could open you up to malicious viruses.
Stay off public Wi-Fi
You can’t guarantee that public Wi-Fi will be safe and secure. Someone else could be on the Wi-Fi trying to intercept your data. To avoid this, stick to data whilst out and about.
Activate Find my iPhone
For iPhones, you can activate Find My iPhone to track your phone if it’s lost or stolen. You can also remotely wipe the data and contents from your phone if you’re sure you can’t get it back.
Best phones for privacy
Take a look at some of the best smartphones you can buy that have privacy and security at the heart of their design.
Purism Librem 5
The Purism Librem 5 is designed with ultimate security in mind.
This private phone allows you to fully protect your information and maintain control over the use of your data. This brand prides itself on being the “future of digital privacy”. Check out some of their privacy features below.
✔ The Librem 5 operates on PureOS, which is neither iOS nor Android. Purism claim it’s the most efficient operating system for providing privacy without compromising on performance
✔ Tracking is disabled by default on the phone and its apps
✔ The phone has a physical ‘kill switch’ built into its design. When pressed, it disconnects Wi-Fi, Bluetooth, signal, microphone, camera, and GPS
✔ There is no need to enter banking details to download an app from the app store
✔ Ideal for individuals and businesses, with built-in software protection that fights viruses and common threats
✔ Source code is available for audit — perfect for CTOs and tech enthusiasts
✔ Continuous privacy updates ensure the phone stays secure and protected
✔ Applications are isolated from one another. They don’t have visibility or access into areas that are not needed or allowed.
iPhone 12
A familiar name, the Apple iPhone 12 comes with a few features to make you feel more secure.
✔ Face ID means only your face looking into the phone’s camera sensor can unlock the iPhone
✔ Supports two-factor authentication with a PIN number and Face ID to make your phone extra secure
✔ The Find My iPhone feature allows you to not only locate your phone if it’s lost or stolen, but also remotely wipe your data
✔ With iOS 14 you can control how much data is shared with apps. Apps must ask your permission to track you
✔ Cloud backup allows you to save your data to iCloud to erase your device or switch to a new one. Having this option means you’re less likely to lose any information
✔ If you’ve got other Apple devices, you’ll sometimes get asked to cross-reference that it’s you trying to log in.
Google Pixel 5
The Google Pixel 5 is the most up-to-date model in the Pixel series and runs on the newest operating system, Android 11.
✔ Set different types of app permissions: ‘One-time permissions’ and ‘Permissions auto-reset’. The former means you can give apps access to your microphone, camera, and location, but it has to request permission each time. The latter means your device will turn off the data permissions on apps you haven’t used in a while. Between these settings, no app can automatically track your activity without your given consent
✔ The Google Safe Browsing feature helps you avoid suspicious websites and links
✔ Google Play sends privacy fixes to your phone to avoid things like downloading dangerous apps
✔ Gain greater control over all of your Google devices from your phone by knowing exactly what’s connected in your home (like the TV, lights, smart kitchen appliances) and turning off things that aren’t needed or wanted
✔ Android 11 comes with added privacy enhancements to protect work profiles on company-owned computers.
Bittium Tough Mobile 2
Founded in 1985, Bittium specialise in producing secure devices for governments, leading authorities, companies, and anyone else who wants strict privacy measures.
✔ Has multi-layered security integrated into both the hardware and internal software on the phone to keep your data secure from prying eyes. Includes tamper detection to prevent spying, disk encryption, and OS security
✔ Easily activate Privacy Mode by holding the button in the top right on the case. It will light up green when it’s on, and disable the microphone, camera, and Bluetooth so you can ensure no one is spying on you
✔ Includes Bittium Secure Suite device management, allowing individuals or organisations to communicate securely
✔ User credentials are encrypted and privately stored, so no one can access your passwords and other sensitive information
✔ There are three variants of the mobile phone, depending on the level of security desired. Choose with Google Mobile Services, without Google Mobile Services, or with separated operating systems (only available for governments and qualified organisations).
Silent Circle Blackphone 2
Silent Circle is an encrypted communications company that specialises in privacy. Like Bittium, they are aimed at governments and organisations that require strict security measures, but anyone can buy their smartphones.
✔ Encrypted by default to protect the internal data on your device
✔ Apps have to ask for your permission before saving, storing, or tracking any information
✔ Comes with the Blackphone Security Centre management system
✔ Use the Spaces feature to separate personal apps, data, and activity from work-related ones. This keeps your data on both accounts fully protected and secure
✔ Buy their Silent Phone license for secure calls and video conferences. You’ll also get access to their Burn feature which deletes all communications between people.
Fairphone 3
Not only is the Fairphone 3 privacy-conscious, but it’s also one of the most sustainable and recyclable smartphones on the market. If you want to support ethical manufacturing, check out this brand.
✔ Lock your SIM card to prevent loss of data if your phone is stolen. By doing this, your phone will require a PIN every time you start it up. If the user doesn’t enter this correctly, they won’t be able to make calls, text, or use data
✔ Use Android Device Manager to remotely wipe your lost or stolen phone. You can also set a new password through this if you think yours has been compromised
✔ Operates on /e/OS, in partnership with /e/ Foundation, which focuses on maintaining user privacy.
While phones designed with extra privacy features are helpful, there’s plenty more you can do to keep your smartphone safe.
Follow us on Twitter for more tips and guides.
Источник