- Droid SQLi Android
- Droid SQLi позволяет внедрять SQL-код в целевой URL. Злоумышленнику нужно всего лишь указать уязвимый URL-адрес, и инструмент автоматически атакует его
- Для чего используется Droid SQLi?
- DroidSQLi — Android App For Hackers
- Droid SQLi Android
- Droid SQLi lets you perform SQL injections into a target URL. The attacker only needs to provide a vulnerable URL and the tool will attack it automatically
- What is Droid SQLi used for?
- SQL Injection
- How to do SQL injection on Android using DriodSQLi
Droid SQLi Android
Droid SQLi позволяет внедрять SQL-код в целевой URL. Злоумышленнику нужно всего лишь указать уязвимый URL-адрес, и инструмент автоматически атакует его



SQL-инъекция — это метод, используемый для взлома приложений, основанные на данных, путем внедрения вредоносного SQL-кода для изменения нормального функционирования программы. Это серьезная ошибка безопасности, которая может нанести большой ущерб.
Для чего используется Droid SQLi?
По словам его разработчика Эдгарда Чаммаса, приложение DroidSQLi позволяет злоумышленникам внедрять SQL-код в целевой URL-адрес всегда для образовательных целей и без каких-либо гарантий того, что оно будет работать должным образом. Пользователь, который хочет попробовать его, будет нести всю ответственность за возможный результат.
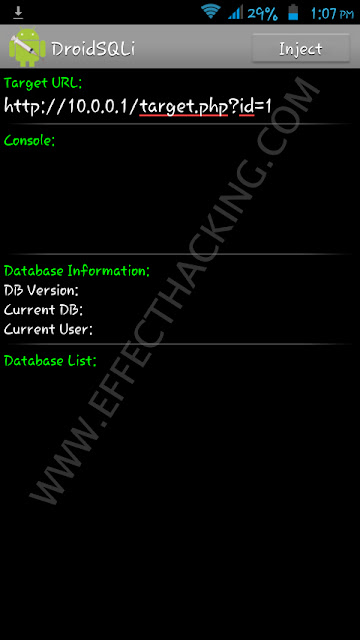
Если вы считаете себя достаточно смелым, вам «просто» нужно найти уязвимый целевой URL и этот инструмент автоматически начнет атаку путём внедрения SQL-кода. Если процесс работает, имена доступных баз данных появятся на интерфейсе, и всю необходимую информацию можно получить, нажав на них.
Источник
DroidSQLi — Android App For Hackers
[Download link is at the end of this article]
Pretty simple huh? Now you may want to know «what are the injection techniques DroidSQLi supports». If yes, take a look:
- Time based injection
- Blind injection
- Error based injection
- Normal injection
Wait. did I forget something? Yes. I didn’t tell you how to find SQLi vulnerable sites.
Here is an easy way to find SQLi vulnerable websites:
Just use any of the following Google dorks:
- inurl:index.php?id=
- inurl:trainers.php?id=
- inurl:buy.php?category=
- inurl:article.php?ID=
- inurl:play_old.php?id=
- inurl:declaration_more.php?decl_id=
- inurl:pageid=
- inurl:games.php?id=
- inurl:page.php?file=
- inurl:newsDetail.php?id=
- inurl:gallery.php?id=
- inurl:show.php?id=
- inurl:staff_id=
If you want more SQLi google dorks, read the article » Google Dorks Ultimate Collection For Hackers «.
I hope you liked the article, if you did, feel free to share this article with your friends and followers.
Источник
Droid SQLi Android
Droid SQLi lets you perform SQL injections into a target URL. The attacker only needs to provide a vulnerable URL and the tool will attack it automatically





An SQL injection is a technique used to attack data-based applications by inserting malicious SQL code to alter the normal functioning of the program. This is a serious security error that can do a lot of damage.
What is Droid SQLi used for?
According to its developer Edgard Chammas, the DroidSQLi application lets attackers perform the SQL injection into a target URL, always for educational purposes and without any guarantee that it will work properly. The user who wants to try it will be solely responsible for the possible result.
If you consider yourself to be brave enough, you ‘just’ have to find a vulnerable destination URL and the app will start the SQL injection attack fully automatically. If the process works, the names of the accessible databases will appear on the interface and all the necessary information can be obtained by clicking on them.
Источник
SQL Injection
SQL Injection (SQLI) is when untrusted data is used to construct an SQL query. The data is inserted (or «injected») into the SQL query string.
SQLI has been ranked #1 on Top 10 security threats by OWASP.
It is a top threat for a few reasons. It is easy for attackers to detect and exploit. It is a powerful attack because it give access to application databases, and most modern web applications rely heavily on databases. It is successful because it circumvents the normal access controls to database data. Web applications usually have full or near full access and SQLI attacks are able to use access to their advantage.
SQLI attacks can have many different goals.
Probe application or database structure
- Bypass application logins
- Usernames
- Passwords
- Identity info
- Credit cards
- Change orders or transactions
- Elevate permissions
Imagine a login form. When the form is submitted, the application code constructs an SQL query to search for a matching username and password in the users table. (Assume the code is encrypting the password. It should never be stored in plain text!)
A hacker visits the login form and, instead of providing a username, submits an carefully-crafted string in its place.
Read the resulting SQL carefully. Notice that the string closes the single-quote in order to «break out» of the intended input value. OR 1=1 will always return true and — indicates the start of a comment in SQL. The result is that the query will match all users and the password clause will be ignored. Potentially, this SQLI attack could bypass the login page and grant access.
Attacks which can communicate with the SQL database are not limited to simple commands like in the previous example. Here are a few other examples.
Any query which utilizes user input is vulnerable to SQLI.
The most frequent area of attack are WHERE clauses. They receive the most dynamic data as the application searches for results matching a URL or a user requests searches using various parameters.
Other query types are equally vulnerable, just not as frequently used. INSERT , UPDATE , DELETE statement must be considered, as well as other SQL clauses like SELECT and ORDER BY .
If dynamic data contributes to the SQL in anyway, then it must be considered vulnerable.
Often is possible to see the results of SQL Injection immediately. This allows an attacker to know right away when they have found an exploit. This is useful if the goal is to steal data.
However, it is possible for an SQLI exploit to exist which does not return visible proof. Imagine that there is a page which will accept an SQL Injection and send it to the database, but which will display the same standard error page to a user regardless of whether the SQL Injection succeeded or not. Because an attacker cannot see the results this is referred to as a «Blind SQL Injection».
One common technique is to inject an SQL query which will cause the database to pause or return a slow response if the injection works.
The easiest version is to use SLEEP() to create a slow response. If it works, the server will pause for 5 seconds. If it does not work, it won’t.
Here is a more elaborate example which, when injected, will use IF() to test if the first character the username for user_id=1 is CHAR(97) (the letter ‘a’). If true, then the BENCHMARK() function executes a slow process 5 million times. If false, it finishes the query quickly. An attacker could go through the entire alphabet in a loop to determine the full username.
This technique can be used to examine the structure of the database (table names, column names) as well as the values in the table rows.
Sanitizing input is the best way to prevent SQL Injection. However, there is something easier which can serve as a first line of defense. The application never needs full database privileges. This follows the principle of Least Privilege. The application should have the least amount of privilege necessary to do its job. Frequently, developers are lazy and grant broad privileges without taking time to consider which ones are actually necessary.
Of course, the application needs to be able to read and write to most tables. But some tables might be privileged and could be restricted. The application’s database user could be forbidden from creating, truncating, or dropping any of the tables. SQL has a special permission (the GRANT OPTION) which allows granting permissions to other database users. It is a powerful privilege and unlikely that the application needs it.
Most importantly, never let the application connect as root user. The root user is the most privileged user in SQL. It is easy to create a new user exclusively for the application’s use—one command to create, one command to grant access. There is no reason to give attackers such a gift.
The best defense against SQLI is sanitizing the incoming data. This means escaping characters in the data which have special meaning to SQL.
In simple terms, this means putting a backslash ( \ ) before any single quotes. However, it would be naive to simply add slashes before single quotes because there are many tricks to circumvent detection. Instead, use a well-tested sanitization library which will account for all possibilities.
In PHP, the function mysqli_real_escape_string() is a helpful tool for escaping strings for use with MySQL databases.
In addition to sanitizing, whitelisting and validating data expectations can be useful tools in preventing SQLI. For example, if a text input field is expecting a postal zip code, then it is reasonable to restrict the value to letters, numbers, spaces, and dashes, and to limit its length.
Prepared statements are an effective prevention measure against SQLI attacks. An SQL statement is prepared with placeholders for any dynamic data. Data must match a data type specified (string, integer, etc.) and must act exclusively as data. It cannot add any code to the SQL query.
It is important to recognize that there are other injection types besides SQL Injection. SQLI is most common because of its popularity and easy access from web pages. But any data passed to an «interpreter» can be injected with additional content.
Some other examples include:
- Code injection (PHP, JavaScript, etc.)
- OS/shell commands
- LDAP
- XML parsers
Источник
How to do SQL injection on Android using DriodSQLi
Hello folks! SQL injection on Android has dependably been an a good time for programmers, particularly novices! Be that as it may, hold up a moment, have you at any point thought of doing this assault from your telephone? This isn’t a fantasy or bad dream please. Today I’m going to demonstrate to you the means with respect to how you can do this comfortable fingertips! Praise, lets proceed onward!
Before beginning further, on the off chance that you are confounded about SQL, what do SQL infusion assault truly mean, I counsel you to peruse this instructional exercise some time recently:
Additionally Read these articles to get a brisk thought with reference to how you can accomplish this straight from your crate. Given underneath is a point by point direct on SQL Injection assaults, and to be noticed, these instructional exercises have picked up a basic thankfulness as well. I exceptionally suggest you as well, to experience it!
Lets start now! You need to have a rooted Android. To know more read :
First you have to download the apk file from here :
(Copy the above link and download)
Now you should have little knowledge of Google dorks. Here is the list of Google dorks vulnerable to SQL injection:
Here is the link to download a whole list :
Let’s take an example to describe the process in step by step manner:
1. Let’s take a google dork link
2.Copy and paste this link to Google.
3.At that point tap on any connection that you wish to infuse with SQL for eg:
4.Duplicate the entire URL
5.Presently, open the DriodSQLi apk
At that point at the place of Target URL:
Glue the duplicated interface from Google i.e.( www.atozpictures.com/pictures.php?Id=2)
7. At that point tap on Inject
Done ..now hold up till the procedure closes.
Wow we have effectively hacked the database with SQL.
Hope you enjoyed reading this tutorial SQL injection through Android!
Do like, comment & share with your friends! 🙂
Источник