- 🤔Adding SSL Certificates into your Android App with Retrofit
- 🏁 Intro
- 📄 Let’s talk about the certificates
- 🥺 What is the difference?
- 😬 Give me the implementation!
- 🏃♂️ Let’s get started!
- 💻 The Code
- 🏆 Conclusion
- How to Download and Install a PKCS#12 onto Your Android Device
- How to Download a Certificate onto Your Android Device
- Step 1 — Open Certificate Pick Up Email on Android Device
- Step 2 — Enter Certificate Pick-Up Password
- Step 3 — Create a PKCS#12 Passphrase
- Step 4 — Download the Certificate onto Your Device
- Step 5 – Name Your Certificate
- How to Add a Certificate to Your Android ‘Device Credentials’
- Step 6 — Navigate to Settings > Security
- Step 7 — Locate Your Downloaded Certificate File
- Step 8 — Enter Your PKCS#12 Passphrase
- Step 9 — Adjust Certificate Settings
🤔Adding SSL Certificates into your Android App with Retrofit
When this task was assigned to me in the project I’m working, I thought: this will be easy and it was 🙂, but it wasn’t 🙃, because I didn’t find a lot of posts on how to add my certificate.
You can always read the Official Android SSL Documentation (you should), but the implementation wasn’t clear enough to me, so I decided to create this post to simplify it for anyone who is going through the same problem 👍.
🏁 Intro
In this post I’m going to explain how to add certificates to our Android app when we have a .pfx file, not only the .crt , and of course, it will include a brief explanation of what those files are.
So after reading this tutorial we’re going to be familiarized with:
This tutorial is going to be based on a project using Retrofit to make calls to an API, but you can always adapt it for your specific case.
📄 Let’s talk about the certificates
A certificate authority (CA) is a company or organization that acts to validate the identities of entities (such as websites, email addresses, companies, or individual persons) and bind them to cryptographic keys through the issuance of electronic documents known as digital certificates.
So basically the CAs give us a way to authenticate us by serving as credentials to validate our identity, encrypt our data for secure communication over the insecure networks such as the internet, and give us a way to be sure nothing has been altered by a third party in transit because of the signature of the certificate.
Typically, an applicant for a digital certificate will generate a key pair consisting of a private key and a public key, along with a certificate signing request (CSR). A CSR is an encoded text file that includes the public key and other information that will be included in the certificate (e.g. domain name, organization, email address, etc.). Key pair and CSR generation are usually done on the server or workstation.
The .crt and the .pfx files are CSR encoded.
🥺 What is the difference?
CER (or .CRT) files: CER file is used to store X.509 certificate. Normally used for SSL certification to verify and identify web servers security. The file contains information about certificate owner and public key.
PFX files: Personal Exchange Format, is a PKCS12 file. This contains a variety of cryptographic information, such as certificates, root authority certificates, certificate chains and private keys. It’s cryptographically protected with passwords to keep private keys private and preserve the integrity of the root certificates.
Basically, the PFX contains more information than the CRT.
😬 Give me the implementation!
Okay, if you already know something about the CAs you probably just want to know how to implement them. So, let’s get into it.
If you have tried to add your certificate with a .crt file and Retrofit, you may have found this class in some post or documentation. I’m actually going to use code of that class for the implementation, but I’m going to break it down for easier reading, and to show the small changes we need to add when we’re using a .pfx file so you can use whichever you need.
The source code is gonna be at the end of the post.
🏃♂️ Let’s get started!
In order to add our certificates we’re going to create a method that generates an OkHttpClient. We only need to follow these simple steps:
- Add our file into our project as a raw resource.
2. Create a method that returns an OkHttpClient .
3. Create a KeyStore containing our trusted CAs.
5. Create an SSL Context that contains our trusted CAs.
6. Add our socket factory to our builder.
7. Use the generated OkHttpClient as usual.
- Add our file into our project as a raw resource (in the raw folder).
We can just drag and drop the file into the raw folder or go to our project directory and create it inside the app/src/main/res and then paste our file.
2. Create a method that returns an OkHttpClient .
This method is where we’re going to add our certificate to our OkHttpClient so we can use it to make calls to an API. In this example, I’m going to simplify, but you can always add custom settings.
3. Create a KeyStore containing our trusted CAs.
The KeyStore class is going to help us to store our certificates, but the type of instance is very important, that’s going to make the difference between using a .crt file or a .pfx .
.CRT → the default type is gonna work for you. KeyStore.getInstance(KeyStore.getDefaultType())
.PFX → you need to use PKCS12, this is a special format to place the certificate (includes its “intermediate”) with the private key.
KeyStore.getInstance(«PKCS12»)
The password is the one you need to use when you want to read your file. In this code I’m setting it as a String , but you should always keep it secure, so you better use a file with it or as a Build Config Field.
4. Create a KeyManagerFactory so we can have keyManagers with the algorithm of our certificate.
We’re getting an instance of an X509 Factory because that’s the standard of my public key certificate and it’s the most used one.
5. Create an SSL Context that contains our trusted CAs.
In this case we’re using an instance of a TLS Context because our server required so, and as TLS is basically a newer version of SSL we can use it as default.
6. Finally, add our socket factory to our builder.
Just use the socketFactory of the sslContext that we created in the last step and set it to the builder.
7. Use the generated OkHttpClient as usual.
Now that we added our trusted CAs to an OkHttpClient we can proceed to use it with a Retrofit instance as usual.
And just like that we’ll be able to make some calls to our API 🎉.
💻 The Code
🏆 Conclusion
Adding our trusted CAs in our Android app is not complicated and can be very useful when we have multiple flavors or build types with different API environments and some of those are secured with a CA.
Remember to remove your Development certificate when you’re building a Release version of your app; you don’t wanna give it away 😅. I also suggest deleting the file from Git for security reasons.
This post was made to try to simplify the explanation of the implementation that you probably are gonna find on the internet.
Источник
How to Download and Install a PKCS#12 onto Your Android Device
One of the questions we’re most often asked is, «how do I download and install my Digital Certificate to my phone?» If you want to encrypt emails or authenticate to corporate networks using your mobile device, installing the certificate can be a bit of a barrier. Fortunately, Digital Certificates are compatible with most of the leading mobile operating systems, so it’s easy to implement and enforce the same security policies, even on mobile devices.
You can view the full ‘how-to’ video here or continue reading for the in-depth guide.
Note: This post is about how to install certificates onto devices. If you’re looking for information about what mobile certificates can be used for, please visit our mobile page.
The method involved in installing Digital Certificates onto your mobile device will vary by operating system. To help you support mobile devices in your workplace, we’ve put together a user guide that walks through how to install a Digital Certificate or PKCS#12 file onto an Android phone. The overall process is really simple; let’s take a look now:
A couple things before we get started.
- This example will show you how to install a PKCS#12 (as opposed to other file types) onto an Android device, which is our recommended option as the file type is easily accepted and provides the simplest installation experience for the end user.
- I’m running through this using a GlobalSign Digital Certificate and GlobalSign’s certificate issuance process, but the general steps should be the same regardless of the supplier and issuing Certificate Authority.
There are two main parts to downloading and installing a certificate on an Android device — downloading the PKCS#12 or .pfx file onto the Android and adding it to the device’s «credential store». We will take you through the steps involved in each part now. Let’s get rolling!
How to Download a Certificate onto Your Android Device
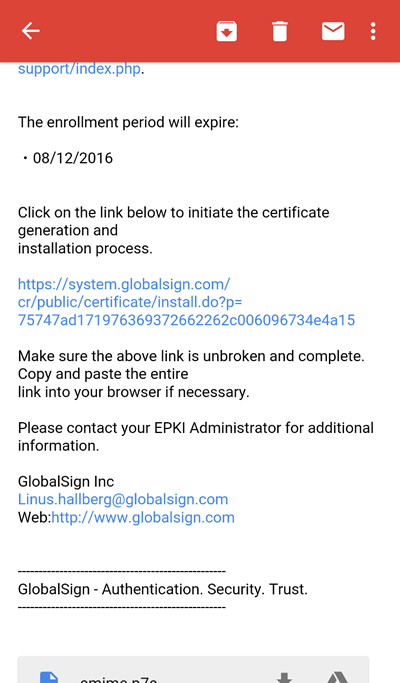
Step 1 — Open Certificate Pick Up Email on Android Device
Certificate delivery is completed using an over-the-air enrollment method, where the certificate enrollment is delivered directly to your Android device, via email using the email address you specified during the registration process.
Click the link in your certificate pick up email.
Step 2 — Enter Certificate Pick-Up Password
Click on the enrollment link in the email. Next, you will be prompted to enter the one-time certificate password you created (or an administrator created for you), during the certificate ordering process.
Enter your certificate pick up password when prompted.
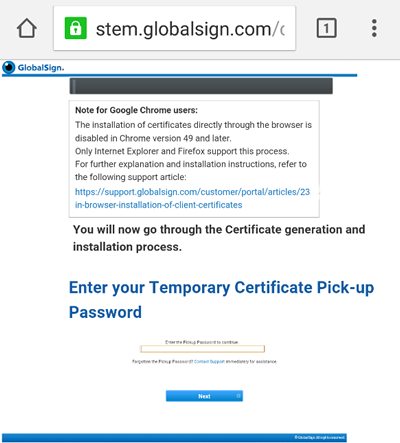
Step 3 — Create a PKCS#12 Passphrase
Next, create the password you will use when you install the certificate onto your device (covered in the next section). Our system asks that your password is no less than 12 characters and is only alpha-numeric. That means no special characters. Make sure you read our subscriber agreement and click ‘I agree’ to proceed.
Create the password you will use during the install process.
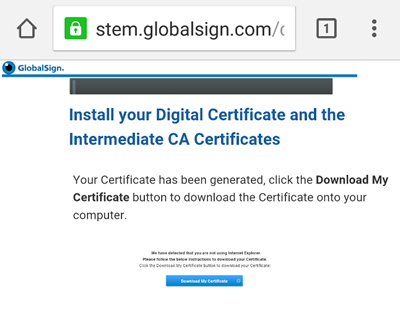
Step 4 — Download the Certificate onto Your Device
After your certificate has been generated, you will be prompted to download the certificate to your device. The file will appear in the ‘downloads’ folder on your device.
Download the certificate onto your device.
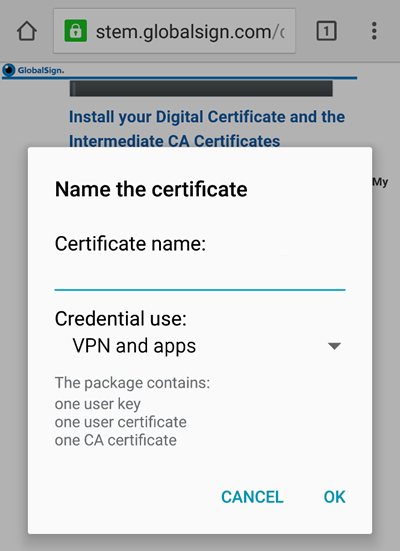
Step 5 – Name Your Certificate
Give your certificate a name so you can easily find it in your certificate store later.
How to Add a Certificate to Your Android ‘Device Credentials’
At this point you may have a warning on your phone saying ‘network may be monitored by a trusted third party’. Technically what Android is saying here is ‘if a malicious or compromised certificate is being installed here then it’s possible someone is monitoring you.’ So the warning is made a little scarier than it needs to be because a certificate doesn’t have to be genuinely malicious to trigger the warning. In the Android developer community people are calling for this feature to be removed. So fear not, let’s move onto the next step.
To complete the install and remove that pesky warning, you need to add the certificate to your device’s security credentials.
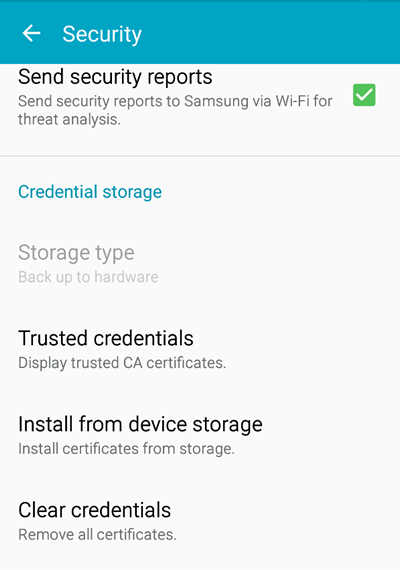
Step 6 — Navigate to Settings > Security
Select «Install from device storage» from your security settings to get the certificate file from the ‘downloads’ folder of your device.
Select «install from phone storage» to find your recently downloaded certificate.
Step 7 — Locate Your Downloaded Certificate File
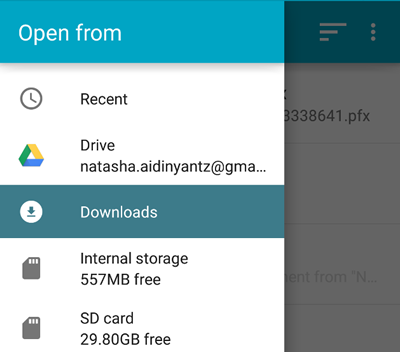
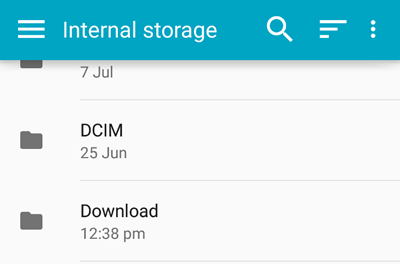
You should be able to find the ‘downloads’ folder in the left hand menu as soon as you click on ‘Install from device storage’.
If you can’t find it, you can navigate there by clicking «Internal storage» from the list of locations in the «Open from» window. Then navigate to the «Download» folder and select your certificate .pfx file.
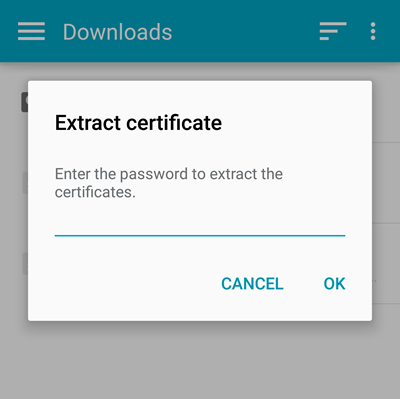
Step 8 — Enter Your PKCS#12 Passphrase
Enter the password you created in Step 3 above.
Enter the PKCS#12 passphrase you created earlier.
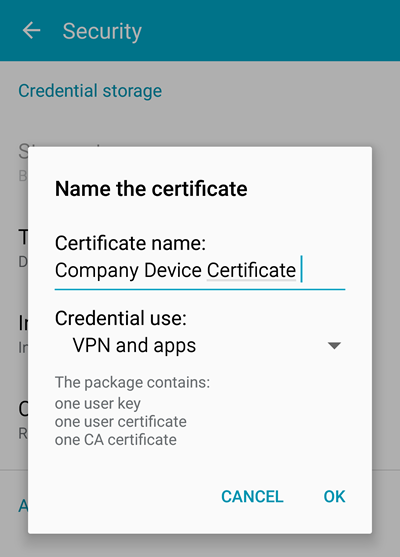
Step 9 — Adjust Certificate Settings
Now that the certificate has been added to your device’s credentials, you can set the certificate name and its use — VPN and Apps or Wi-Fi depending on where you plan on using the certificate to authenticate.
Little is known about why this option is given. A certificate should always be able to do both. My advice is to pick the one which is closest to what you want to do with your certificate, but it won’t matter which one you chose as you should still be able to authenticate into both services with an X.509 certificate from GlobalSign.
Set your certificate name and purpose.
The certificate is now successfully downloaded onto your Android device. You can now use it as an authentication factor for connecting to VPN clients, Wi-Fi, email and other corporate apps, as well as for digitally signing and encrypting emails (S/MIME).
Источник